When you sign up for the On Demand service for the first time, you create an organization and you are granted the On Demand Administrator role. You can add additional organizations and administrators.
For more information about managing your organization see Managing organizations and regions in the On Demand Global Settings User Guide.
Some common actions with Organizations are reproduced here for your reference:
Creating an organization
- Sign in to Quest On Demand.
- If you have not yet created an organization, click Create Organization.
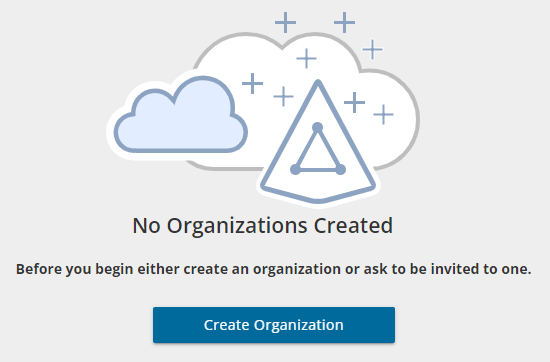
If you have created one or more organizations, the Choose an Organization page opens. Click Create New Organization.
If you have already selected an organization, click your email address at the top right-hand corner of the page and the select Create Organization. The Create Organization page opens.
- Basic information
- Organization Name - name of your organization. For example, Big Box Inc.
- Deployment Region - A Microsoft Azure region or geographic area where data centers are deployed. Not all On Demand modules are available in all regions.
- Authorized Domains
- Domain List - Enter a domain name to restrict restrict users from other domains from accessing this organization. By default, users from all domains have access to this organization. If required, you can restrict access to only users from select domains by adding them to the authorized domains list.
- AI feature
The AI migration assistant is a helpful tool to generate AI summaries for migration tasks. When this feature is enabled in your organization, each migration task wizard that supports this feature will have a Generate AI summaries option in the Reporting step of the migration wizard. If you select this option, an AI summary will be generated for the task, as well as each object in the task. The AI migration assistant uses artificial intelligence to quickly process source materials, highlight critical insights, and offer actionable recommendations.
- Enable AI feature - The AI feature is enabled by default. You use the toggle to activate or deactivate this feature.
- In the Product Name list, enable Migration.
|
|
NOTE: The feature is currently only available in the US region. Customers in other regions can request early access by contacting Quest Technical Support. For more details see KB article https://support.quest.com/kb/4380372 |
- Click Create Organization.
Switching to another organization
If you have multiple organizations associated with your email address, you can select an organization from the Choose an Organization page when you sign in. If you have already selected an organization but want to work with another organization, you can switch to another organization.
- Click your email address at the top right-hand corner of the page.
- Select Switch Organization. The Choose an Organization page opens.
- Highlight and click the organization to which you want to switch.
Renaming an organization
You can rename the organization to which you are currently signed in. You must be an On Demand Administrator to rename an organization.
- Sign in and select the organization that you want to change.
- Click your email address at the top right-hand corner of the page.
- Click the organization name. The Edit Organization page opens.
- In the Organization Name field, enter the new name.
- Click Update Organization Name. The organization name is updated.
Deleting an organization
|

|
Caution: Deleting an organization cannot be undone. |
- Sign in and select the organization that you want to change.
- Click your email address at the top right-hand corner of the page
- Click the organization name. The Edit Organization page opens.
- Click Delete Organization. A confirmation page opens.
- Select the following check boxes to confirm that you understand the impact of deleting an organization.
- All tenants will be removed
- All user information will be lost
- Click Delete Organization.
Quest On Demand uses the Role-based Access Control (RBAC) security policy that restricts information system access to authorized users. Subscribers can create specific roles based on job functions, with the permissions to perform needed operations on the assets of the organization. When users are assigned to On Demand roles, they inherit the authorizations or permissions defined for those roles. RBAC simplifies permission administration for subscribers because permissions are not assigned directly to every user (which can be a significant number of individuals for mid- to large-size organizations) but are instead acquired through role assignments.
The following are some key Quest On Demand and tenant roles that you will need to work with On Demand Migration.
On Demand Administrator
This role is assigned to users who have full access to the Quest On Demand application. They can manage organizations and tenants, initiate the migration of tenant assets, manage licenses, audit records and perform many other functions through the Quest On Demand application. Some of the key permissions associated with this role are as follows:
| Can Export Data |
Permission to export data as well as download the premigration report, comparison report and error report. |
On Demand Migration |
| Create, Rename and Delete projects |
Required permission to create, rename and delete migration projects from the Projects Dashboard |
On Demand Migration |
| View projects and manage selected services |
This permission must be selected to activate the individual permissions to view and manage services. Services selected for this permission will be inherited by all child permissions. |
On Demand Migration |
| View projects |
Required permission to be able to view objects tasks and events for the selected services. Only the tiles for the selected services will be shown in the project dashboards.
Always inherited from parent permission |
On Demand Migration |
| Edit project properties |
Permission to edit properties associated with project services. For example, this permission enables access to Accounts Configure Connections and SharePoint Configure Project. |
On Demand Migration |
| Run a full discovery |
Permission to enable the action that allows users to run the task that will discover all available objects. |
Accounts, Teams, SharePoint, Public Folders, Power BI |
| Run a scoped discovery with CSV file |
Permission to enable the actions that allows users to run the task that will discover objects based on a list contained in a prepared CSV file. |
Accounts, Teams, SharePoint |
| Run a scoped discovery from security group |
Permission to enable the actions that allows users to run the task that will discover objects based on selected security group. |
Accounts |
| Run content discovery tasks |
Permission to enable the actions that allows users to discover content and statistics about selected objects. |
Mailboxes, OneDrive, SharePoint, Power BI |
| Run match and map tasks |
Permission to enable the actions that allows users to find matching objects on the target for selected objects and to map objects on source and target based on prepared CSV file. |
Accounts, Teams, SharePoint, Power BI |
| Run provision and migration tasks |
Permission to enable the actions that allow user to provision and migrate selected objects to the target. |
On Demand Migration |
| Manage collections |
Permission to enable actions for creating and manage the Collection feature. |
On Demand Migration |
| Update and delete migration objects |
Permission to enable the action that allows the user to remove selected objects form the list of services object grid. |
On Demand Migration |
| Acknowledge and clear task events |
Permission to enable the action that allows the user to acknowledge and clear events from the Events grid. |
On Demand Migration |
| Manage Desktop Update Agent |
Permission to enable all management actions in Desktop Update Agent. |
Desktop Update Agent |
| View Reporting Dashboard |
Permission to view reports from the project dashboard |
On Demand Migration |
On Demand predefined roles
Quest On Demand is shipped with many predefined roles. On Demand Administrator, Migration Administrator, Audit Administrator, License Management Administrator and Recovery Administrator are some examples.
On Demand custom roles
You can create more roles with specific permissions to allow other users to work with On Demand Migration. See the On Demand Global Settings Current User Guide for more information about setting up roles.
Tenant Administrator
In this document the term Tenant Administrator refers to the Azure active directory user account for the source or target tenant that is assigned the Global administrator security role and has full access to the tenant. Each tenant that you add to a project requires the credentials of the Tenant Administrator. The Tenant Administrator may require additional roles to grant the necessary consents to various On Demand service principals that are created in the tenant to access various assets in the tenant during the migration lifecycle. See Consents and Permissions for more details. For more information about user and service principals see the Microsoft article Application and service principal objects in Azure Active Directory.
Tenant Administrator accounts must have a mailbox with a valid Microsoft Exchange Online license.
To use On Demand Migration, the Tenant Administrator for each tenant in a project must grant Azure consents and permissions to the On Demand Migration service principals.
Migration Service account
You can use a temporary tenant user account to operate on tenant assets. In this document the term Migration Service account refers to the source or target Azure active directory user account that has temporary access to the tenant through the Global administrator security role. Depending on the tenant asset that is being migrated, this temporary user account must grant specific consents. For example, when teams are migrated, the account that is assigned the Migration Service role is added to the team. This temporary role is required for migrating teams by the by the On Demand Migration service.
If you choose to work with this temporary account, you must login to the tenant as the Migration Service and grant the consents and permissions to the On Demand service principal.
When you are done with the migration, it is recommended that you delete the temporary account for security reasons. See Finalizing the Migration for more details.
On Demand Migration provides intuitive project management for migrating Power Apps Office 365 content from one tenant to another. You can create a migration project that provides a full range of migration features, and track accounts and content migration in one comprehensive migration project dashboard. You can create multiple migration projects and use the My Projects list view for a summarized list of all your migration projects.
Migration steps
References to common migration steps are provided in the table below. There are many more activities that are required to prepare and migrate Office 365 assets, and these are described in detail in the subsequent topics.
Each On Demand migration project needs a source and target tenant. These are Commercial tenants. Commercial tenants are exclusively hosted and managed by Microsoft. For users in the United States deployment region, On Demand Migration offers two options depending on the type of Microsoft 365 tenant that you want to add:
- Commercial or GCC Tenant - choose this option if you want to add either a Microsoft 365 commercial tenant hosted on the Azure public cloud or a Microsoft 365 GCC (Government Community Cloud) tenant with moderate cyber-security and compliance standards hosted on the Azure Government cloud. For more information about worldwide endpoints, see Microsoft 365 Worldwide endpoints.
- GCC High Tenant - choose this option if you want to add a Microsoft 365 GCC High tenant with advanced cyber-security and compliance standards like NIST 800-171, FedRAMP High and ITAR hosted on the Azure Government cloud. For more information, see Microsoft 365 U.S. Government GCC High endpoints.
|
|
NOTE: When you create a migration project, a GCC or GCC High tenant can be used as the target tenant only. Currently, only the On Demand Migration module supports GCC and GCC High tenants. |
For more information about adding, removing and managing tenants, see Managing your Azure tenants and on-premises domains in the On Demand Global Settings Current User Guide.
Adding a tenant
- Log in to On Demand using the credentials you used to sign up for On Demand.
- If you have multiple organizations you must select an organization. If you have a single organization it will be automatically selected.
- If there are no tenants in your organization, click Add Tenant.
-or-
In the navigation panel on the left, click Tenants. The Office 365 Tenants page opens. Then click Add Tenant.
- The Add Tenant page opens.
- Enter your Azure AD Global Administrator credentials for the source tenant and click Next. A page opens with the list of permissions that you are granting.
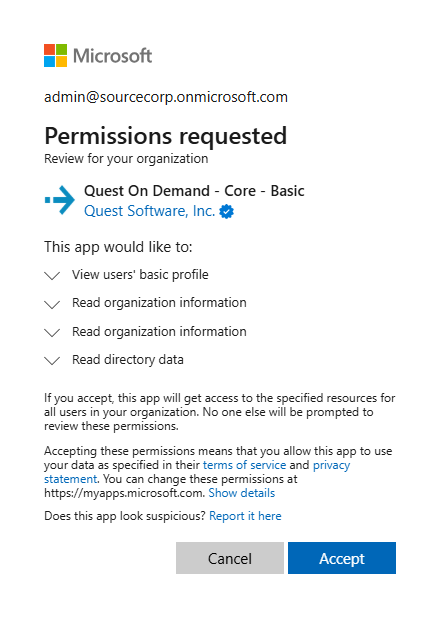
- Click Accept to grant consent to the initial Core - Basic permission set to the On Demand service principal.
- The Office 365 Tenants page opens with the tenant added as a new tile.
- Repeat the steps to add a target tenant.