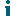Microsoft Azure App Registration
Microsoft Azure App Registration
For migration to Microsoft 365, if you have decided that oversized attachments should be migrated to the Microsoft OneDrive store associated with the user mailbox, use this page to register the MNE application with the Microsoft Azure portal and to grant the migration account with access to the OneDrive stores.
|
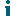
|
NOTE: Oversizedattachmentsaredefinedusingthemaximumsizelimitforattachmentsthatissetinthe Data Migration Wizard on the Select Date and Size Filters screen. |
App registration
Follow instructions to manually register the App: You must perform the steps in Manually registering the MNE application with the Microsoft Azure portal on page 22 to manually register Migrator for Notes to Exchange with the Microsoft Azure portal site. After App registration is complete, you will need to provide the following information from the Azure portal to configure migration of oversized attachments.
-
Tenant Domain Name: Your tenant’s primary domain name on the Azure portal. For example, Sitraka.onmicrosoft.com.
-
Registered App Client ID (SSDM): The application ID created with delegated permissions after the application is registered in the Microsoft Azure portal. It is automatically populated if you used the one-click registration. With the manual registration process, the client ID that you enter for the SSDM is the same as the Registered App Client ID.
-
Registered App Client ID: The Application ID created with application permissions after the application is registered in the Microsoft Azure portal.
-
Registered App Client Secret: The Application Secret created after the application is registered in the Microsoft Azure portal.
Show App Client Secret: When the check box is selected, the App Client Secret value is not masked but is displayed so that you can make note of the client secret value to use if you are manually registering the application with Microsoft Azure.
Manually registering the MNE application with the Microsoft Azure portal
Manually registering the MNE application with the Microsoft Azure portal
To find your Microsoft 365 tenant’s primary domain name, log in into Microsoft 365 Admin Center as an administrator. Under Settings, click Domains and find a domain which ends in .onmicrosoft.com. This is your Microsoft 365 tenant domain name, for example Sitraka.onmicrosoft.com.
The process of registering an application with the Microsoft Azure portal is also described in the Microsoft topic Register an application with the Microsoft identity platform.
|
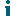
|
NOTE: If you are connecting to Microsoft Azure China portal, you can use the same manual procedure to register an application with Azure China. You can find the Azure China portal at: https://portal.azure.cn |
Depending on the region from which you are accessing the Microsoft portal site, the user interface can differ.
To manually register the MNE application
-
Sign in the Microsoft Azure portal. (You must have global admin rights to register an application.)
-
Search for App registrations in the search box at the top.
- OR-
In the left navigation pane, click the Azure Active Directory service, click App registrations and click New registration.
-
On the Register an application page, enter the application registration information:
-
Name: For example, Quest Migrator for Notes to Exchange.
-
Supported account types: Select Accounts in any organizational directory (Any Azure AD directory - Multi tenant)
-
Redirect URI:
▫ Select Public client/native (mobile & desktop)
▫ Enter a URI: https://login.microsoftonline.com/common/oauth2/nativeclient
|
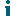
|
NOTE: The Redirect URI is required to register the MNE application for both the Admin console and the SSDM to be able to access mailbox OneDrive storage. |
-
Click Register.
The newly registered application is displayed and the following application details become available.
-
Under Manage in the left section, click API permissions and click Add a permission.
-
On the Request API permissions window on the right, under Microsoft APIs, click Microsoft Graph.
- For MNE Configuration with Oversized Attachment processing:
- Select Application permissions on the right.
- From the list, expand Files, select Files.Read.All, Files.ReadWrite.All, User.Read.All, Application.Read.All, Directory.Read.All and Mail.Send and click Add permissions to grant application permission.
- Go back to add a permission for Microsoft Graph under Microsoft APIs and select the left box Delegated permissions.
- From the list, expand Files, select Files.ReadWrite, Directory.AccessAsUser.All, offline_access, openid and profile and click Add permissions to grant delegated permission.
- For MNE Configuration without Oversized Attachment processing:
- Select Application permissions on the right.
- From the list, expand Files, select User.Read.All, Application. Read.All, Directory.Read.All and Mail.Send and click Add permissions to grant application permission.
- Go back to add a permission for Microsoft Graph under Microsoft APIs and select the left box Delegated permissions.
- From the list, expand Files, select Directory.AccessAsUser.All, offline_access, openid and profile and click Add permissions to grant delegated permission.
|
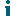
|
IMPORTANT: The option to process Oversized Attachments does not require being enabled if this feature is not in use but does require the use of the Configure button to enter the Application ID. |
-
On the App registrations main page, click Certificates & secrets.
-
Under Client secrets, click New client secret
-
Enter a description and specify an expiration for the client secret (for example, In 2 years).
-
Click Add to generate the client secret.
-
Copy the new client secret value and keep it safe as you need it to complete the application registration in MNE. You cannot retrieve a client secret after you perform another operation or leave this resource management view (blade).
-
On the App registrations main page, click API permissions.
-
Click Grant admin consent for (your company name).
A confirmation message appears on the top.
-
Click Yes.
-
On the App registration main page, click Authentication.
-
Under Advanced settings, click Yes next to Treat application as a public client and click Save.
-
On the Microsoft Azure App Registration page in MNE, enter the values that were assigned for:
-
Tenant Domain Name: Your Microsoft 365 tenant domain name. For example, Sitraka.onmicrosoft.com.
-
Registered App Client ID (SSDM): The application ID created with delegated permissions after the application is registered in the Microsoft Azure portal. With the manual registration process, the client ID that you enter for the SSDM is the same as the Registered App Client ID.
-
Registered App Client ID: The Application ID created with application permissions after the application is registered in the Microsoft Azure portal.
-
Registered App Client Secret: The Application Secret created after the application is registered in the Microsoft Azure portal.
-
Click Save.
Edit Default Settings: Active Directory Configuration
Edit Default Settings: Active Directory Configuration
This screen collects the information necessary for the program and its wizards to access Active Directory. (The screen is disabled if you are migrating to Microsoft 365 without using the Microsoft AD synchronization tool.)
Click Apply after you enter new information or changes to existing information. The program does not read or save any new information or changes until Apply is clicked.
Active Directory credentials:
-
Automatically grant permissions: The access credentials must be an Active Directory administrative account that is a member of the Exchange Organization Management role group, is configured with remote PowerShell enabled, and has full access to the target Organizational Units (OUs). You can use this option to automatically grant the required permissions to the specified account.
If you use the Automatically grant permissions option, MNE delegates Full Control permissions to the root of the target OUs and the permissions are inherited by all OUs, even the OUs that are added after initial configuration.
Alternately, you could manually grant the permissions using the Active Directory Users and Computers tool. If you grant full access to the target OU using Delegation of Control Wizard, you must select Full Control. Open the wizard and select the following: Create a custom task to delegate | This folder, existing objects in this folder, and creation of new objects in this folder | Full Control.The program will check that the access credentials have Full Control rights to the target Organization Units (OUs), not just read/write permissions. You must reconfigure the account each time you change the target OU.
-
Global Catalog host name: Specify a Global Catalog (GC) at a level higher than all the users, groups, and contacts to be migrated. If you have multiple Global Catalogs/Domain Controllers in an AD forest, you can choose any GC as long as it is in the same domain.
|
|
IMPORTANT: You must enter fully qualified domain names (FQDN) for the Global Catalog host name and the Domain Controller host name. |
-
Domain Controller host name Specify the Domain Controller that is used to read data from or write data to Active Directory.
-
User name and Password: The access credentials used to authenticate the administrator by whose authority the program accesses Active Directory.
-
Always use these values: Select this check box if the wizards will always use these credentials. If this box is selected, the wizard skips the screen that requests credential information. If the check box is empty, the wizard retrieves the values entered here as defaults, but will display the screen to offer the option of accepting or changing the default credentials.
-
Path to existing organizational unit for distribution groups: Fully qualified domain name (FQDN) for the group organizational unit (OU) path.
-
Path to existing organizational unit for creating external members for distribution groups: Fully qualified domain name (FQDN) for the path for an existing organizational unit (OU) to which group members will be assigned when a member must be created as a new AD contact (when there is no corresponding AD user account).
-
Create user objects in Active Directory: Determines whether the Provisioning Wizard will create a new user object in AD when none is found to correspond with a user in the collection. Such new user objects are created in the container specified by the Path to existing organizational unit for creating user objects text box. Ordinarily the objects created are not mail-enabled, although the EnableUsers parameter (in Task Parameters) can be set to 1 to change that default behavior.
-
Path to existing organizational unit for creating user objects: Click Browse to find and specify the relative domain name for an existing organizational unit (for example, cn=users) where any new user objects will be created in AD (when a wizard encounters a contact for which there is no existing corresponding AD user account).
-
Use resource/user forest: If your target environment is configured for a resource forest and a user forest with corresponding user accounts, you must provide these credentials for the Data Migration Wizard to enable mailboxes and to associate the resource accounts with the user accounts. The credentials specified here identify the user forest, while the credentials specified for AD credentials pertain to the resource forest.
Userforestcredentials:
-
Global Catalog host name: The name of the AD server.
-
User name: The user ID of the administrator who will be running the migration program, by whose authority the program accesses the user forest AD. This entry must be the SAM Account name, not the UPN.
-
Password: The password associated with the user name.
-
Apply: Reads and saves new or changed information. Any new information or changes are discarded if you do not click Apply before you exit.
-
More info: Launches the Log Viewer to display the associated log file. This button is enabled only if the program encountered significant errors or warnings that require resolution before continuing in the migration. If no significant errors or warnings are encountered, the button is dimmed (unavailable).
Discover Notes Information
Discover Notes Information