Analyzing Scanned Files
The Scanned Files by Search Term and Scanned Files by Scope analyses let you view all of the files that have been scanned for sensitive content, along with the search term(s) found. By default, results display the most recent scan performed on each file within the selected scope, but you can also enter a date range.
To generate a Scanned Files analysis:
1Select the object(s) you want to include in your analysis.
2RightChoose the appropriate option, based on how you would like to have results grouped:
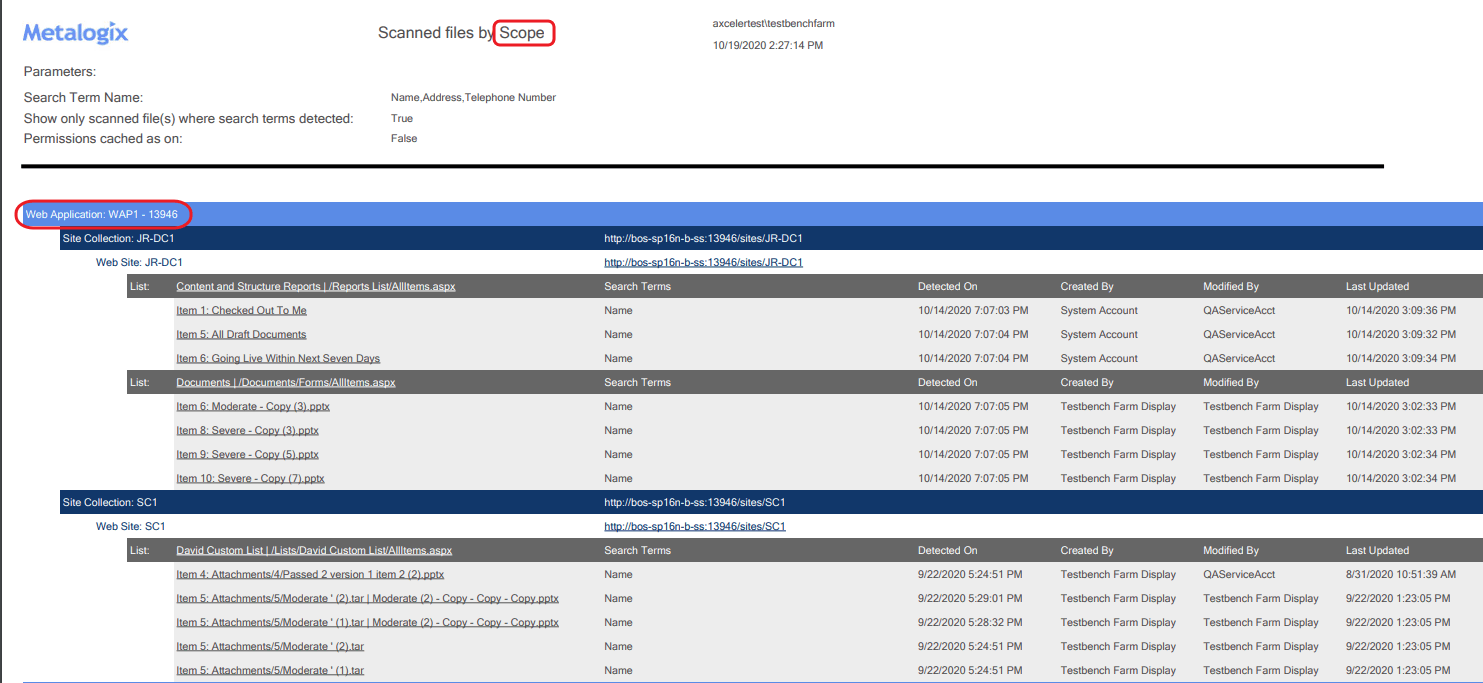
§Compliance > Scanned Files by Scope
OR
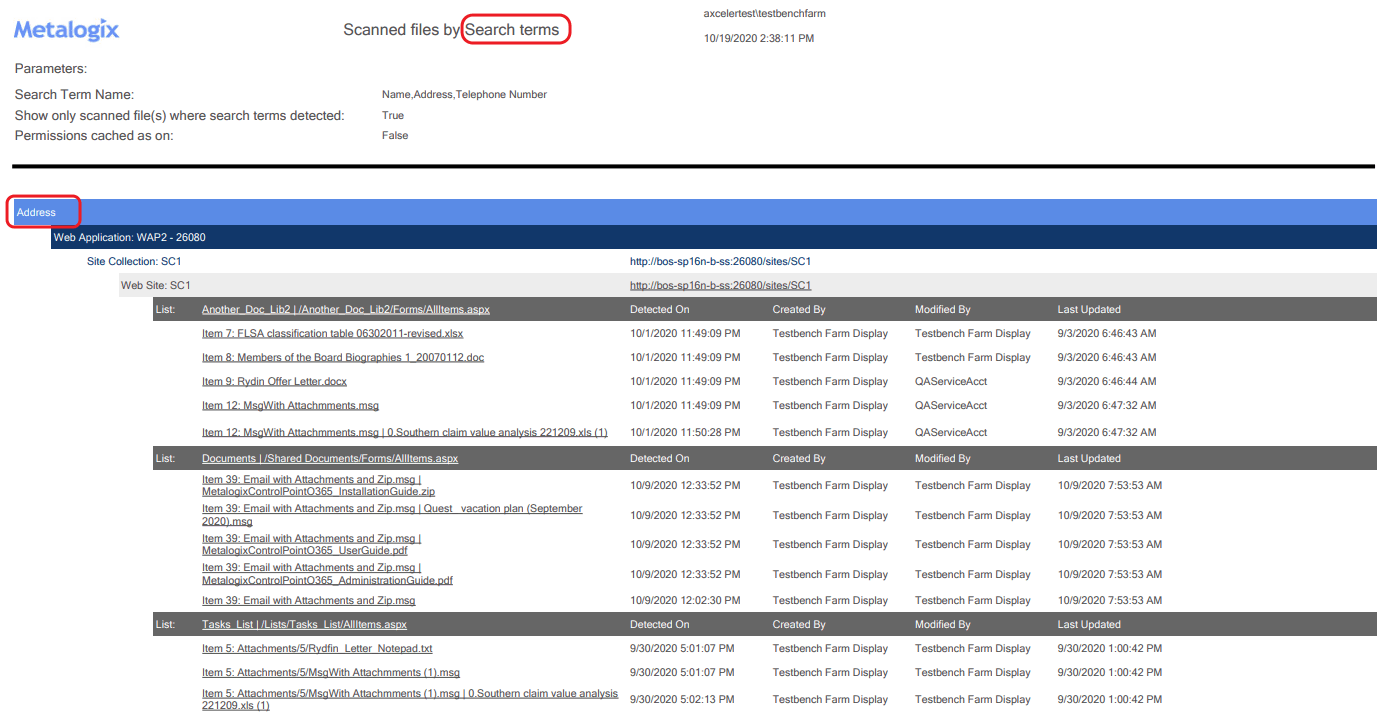
§Compliance > Scanned Files by Search Terms.
3Specify the parameters for your analysis.
IMPORTANT:
§Currently, you can only Filter by Search Terms if you enter one complete search term (that is, you cannot filter by multiple or partial search terms).
If you leave the Filter by Search Terms field blank, all search terms within the scope of your analysis will be included.
4Under Advanced Parameters:
·If you leave the Start Date and End Date blank (the default), the most recent scan performed on each scanned file will be included in analysis results. If you enter a Start Date and End Date, results will include all scans performed within the date range.
·If you want to run the analysis on scans for which the permissions of users who performed the scans were collected since the last run of Discovery, check the Security trimming using cached permissions box. If you leave this box unchecked, the analysis will be run using real-time permissions, but processing time my increase significantly.
Now you can:
·run the operation immediately (by clicking the [Run Now] button)
OR
·schedule the operation to run at a later time or on a recurring basis.
OR
·save the operation as XML Instructions that can be run at a later time.
Results are grouped either by scope or search term (depending on the analysis selected).
Auditing Compliance Actions
The Compliance Action Audit lists actions taken on files scanned by Sensitive Content Manager over a specified date range.
To generate a Compliance Actions Audit:
1Select the object(s) you want to include in the audit.
2Choose Compliance > Compliance Actions Audit.
3Specify the parameters for your analysis.
Now you can:
·run the operation immediately (by clicking the [Run Now] button)
OR
·schedule the operation to run at a later time or on a recurring basis.
OR
·save the operation as XML Instructions that can be run at a later time.
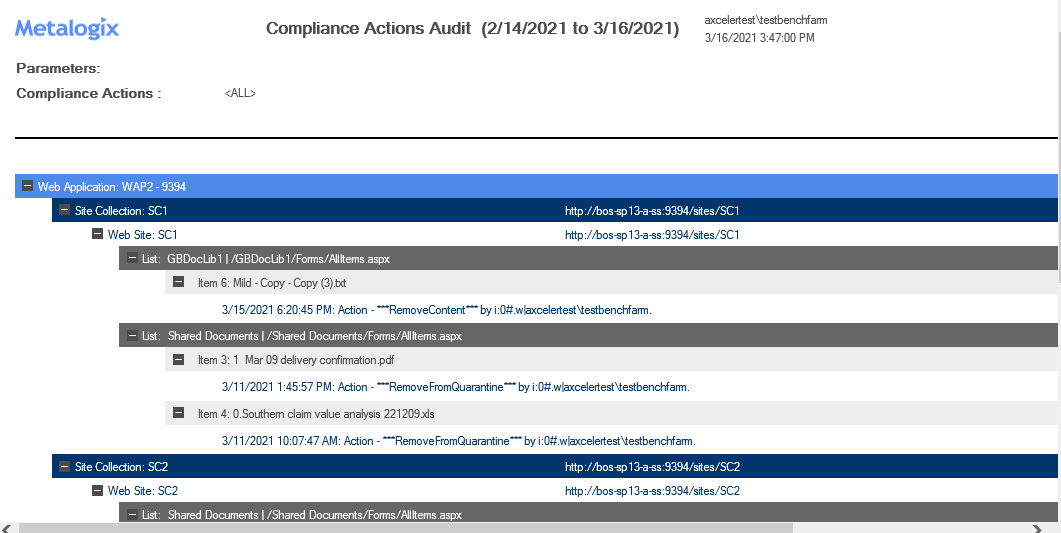
Results include each file within the scope of your analysis, grouped by site collection, along with the date the scan was performed, the action taken, and the account the action was taken by.
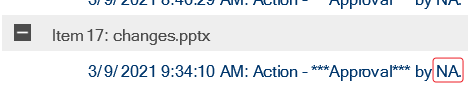
NOTE: For any scans performed prior to version 8.6, the "by" displays NA, as this information was not captured for Compliance reporting purposes in earlier versions of ControlPoint.
Note that for files with embedded items, only the parent item is included in the audit.
Reporting on Sensitive Content Activity
If you are a member of the ControlPoint Compliance Administrators group, you can use the ControlPoint Sensitive Document Activity report to view detailed information about documents analyzed by Sensitive Content Manager that:
·have been identified as "sensitive content" (that is, have been assigned a Severity Level)
AND
·have been accessed by at least one SharePoint user.
NOTE: This report includes sensitive content identified both from bulk scans and as a result of the enforcement of ControlPoint Policies.
Before you can report sensitive document activity:
·Auditing must be enabled for each list or library for which you want to report sensitive document activity. You can enable these settings for individual site collections from within SharePoint or, for a larger scope, using the ControlPoint Manage Audit Settings action.
·At least one Compliance scan must have been returned by Sensitive Content Manager with items that have been assigned a Severity Level.
To report sensitive document activity:
1Select the object(s) for which you want to report sensitive document activity.
2Choose Compliance > Sensitive Document Activity.
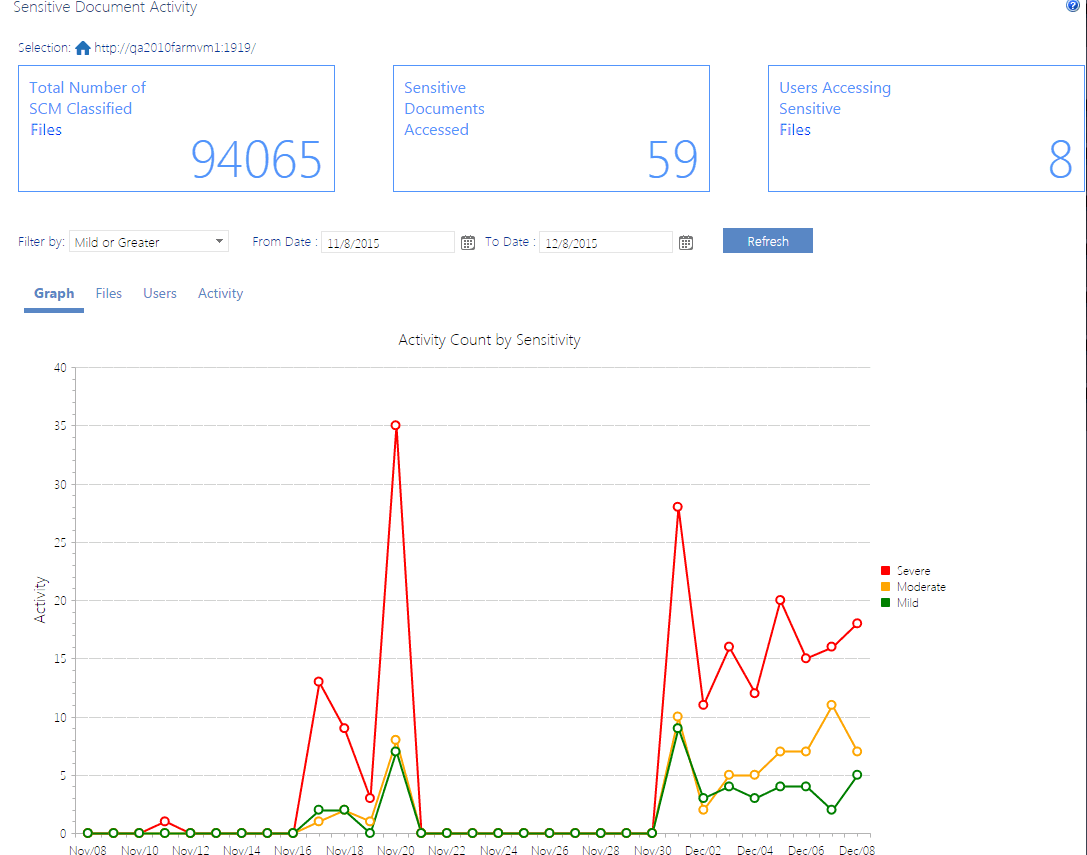
The tiles at the top of the report highlight the following statistics for the selected time period (by default, the past month):
·Total Number of SCM (Sensitive Content Manager) Classified Documents
·Sensitive Documents Accessed (that is, the number of times a document identified as having sensitive content has been accessed by a SharePoint user)
NOTE: The number of times the System Account has modified the Scan Results field for the item on the SharePoint list will be included in this value unless the Sensitive Content Manager Configuration Setting Add Scan Results Column to Scanned SharePoint List is set to false. Details can be found in the ControlPoint Administration Guide.
·Users Accessing Sensitive Documents (that is, the number of unique SharePoint users who have accessed documents identified as containing sensitive content)
·Realtime Scanning (that is, the number of days since the last bulk scan was performed)
To filter results that display in the body of the report:
1.Choose a different severity level from the Filter drop-down and/or modify the default date range.
2.Click [Refresh].
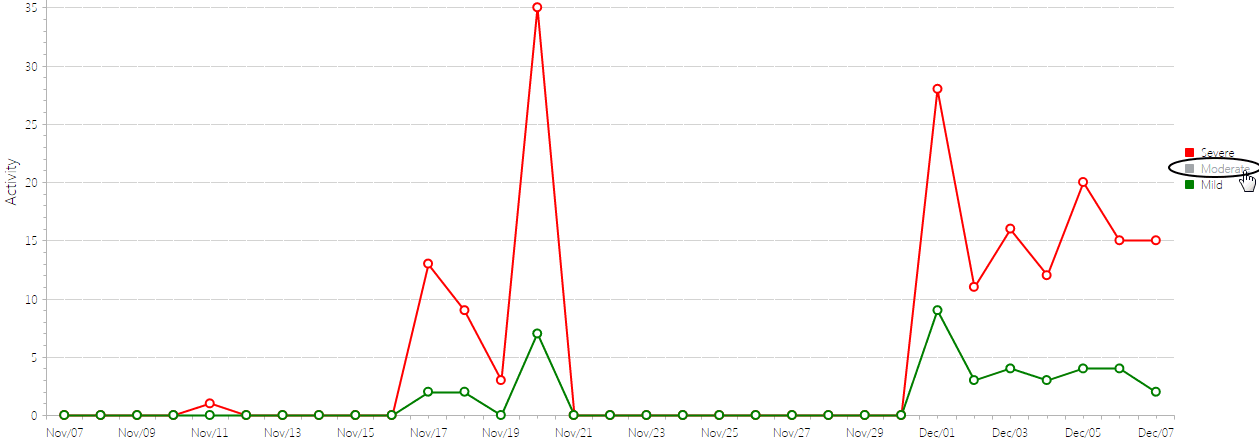
Graph Tab
The Sensitive Document Activity report Graph tab illustrates the Activity Count by Sensitivity for the selected Severity Level(s) and date range.
Note that you can click a Severity Level in the legend at the right side of the page to hide/display it.
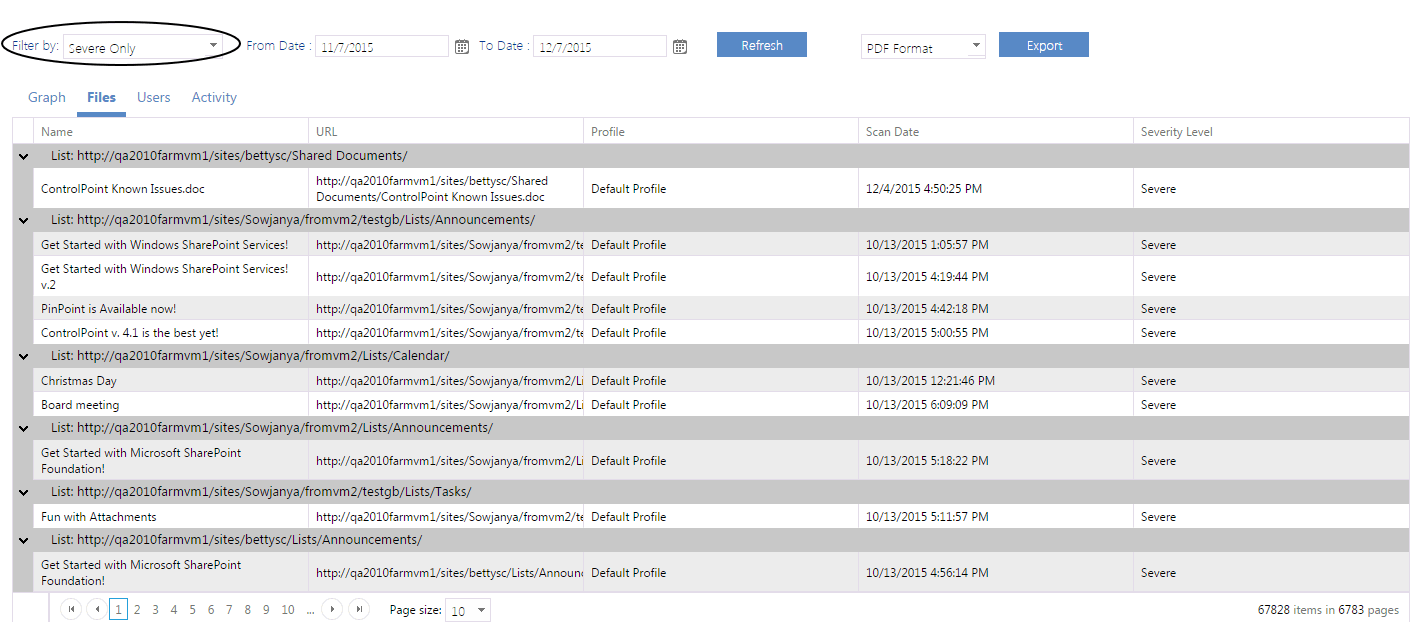
Files Tab
The Sensitive Document Activity report Files tab lists all of the documents the Content Sensitive Manager identified as "sensitive content" for the selected Severity Level(s), grouped by list or library.
Note that this tab displays all content sensitive classified documents for the selected Severity Level(s), regardless of whether they have been accessed, and the date range filter does not apply.
Users Tab
The Users tab lists the SharePoint users who have accessed documents with sensitive content within the specified time period, along with the Number of Docs Accessed.
Activity Tab
The Activity tab lists each individual instance of sensitive content activity, including the User Name. Activity Type, document Severity Level and Activity Date.
Using ControlPoint Sentinel to Detect Anomalous Activity
ControlPoint Sentinel functionality enables you to detect deviations in document views and downloads from individual users' "typical" daily usage patterns. ControlPoint Sentinel uses the following components in its anomalous activity determinations:
·Business Hours: Daily start and end time for each day of the work week.
·The following Anomalous Activity Limits:
§Default daily activity limits: The limits for each (measured in terms of document views and downloads) to apply to any user whose personal activity limits have not yet been characterized.
§Personal daily activity limits: The deviation from "typical" daily usage patterns characterized for each individual user on a given day of the week.
ControlPoint Sentinel relies on SharePoint Audit Log events. Therefore, for this functionality to be effective, the auditing of Delete, Edit, and View/Download must be enabled for every site collection for which you want to collect activity data.