Configure Access Group
In order to limit the target accounts that have access to use cached credentials we will use a Domain Local group in the Source Environment to add in the target account members to control which target users accounts will have the ability to authenticate to source workstations.
-
In Active Directory Users and Computers Create a Domain Local Group.
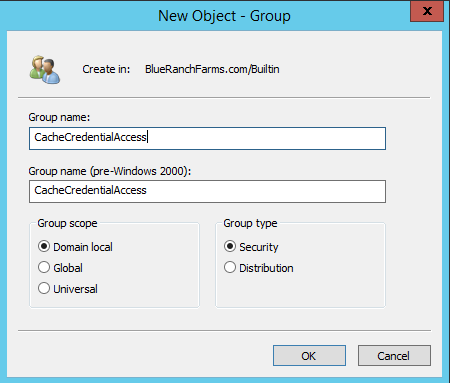
-
Open the group and add in the target user accounts for all migrating source users. In the below example I am adding the target account for Alissa Loftis who is a migrating user from the Source Forest.
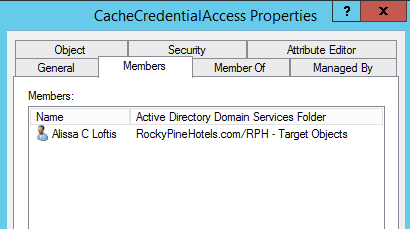
-
Once everyone’s Target user accounts have been added to the source local group, we will then want to assign the right to authenticate for that domain local group on any OU containing workstations being migrated.
-
Once you find the OUs you need to assign the permissions to you want to right click the OU and choose Properties.
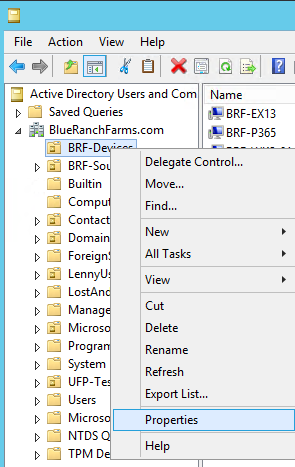
-
Click on the Security tab and choose Advanced.
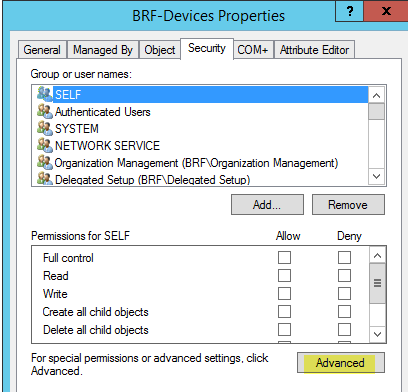
-
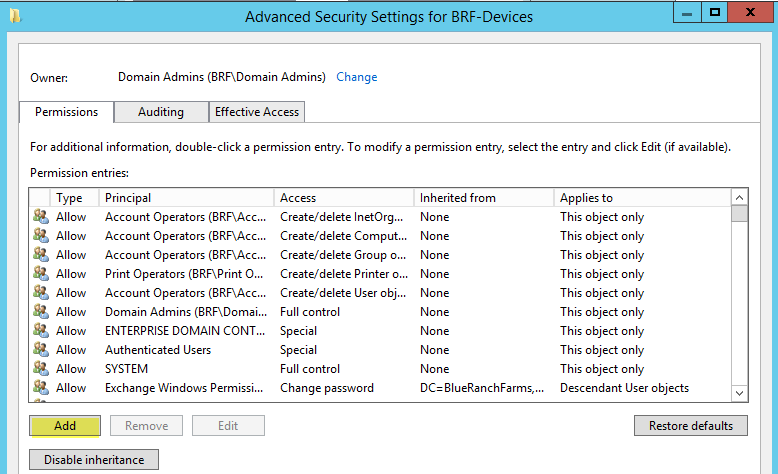
On the Advanced Security Setting screen click on Add.
-
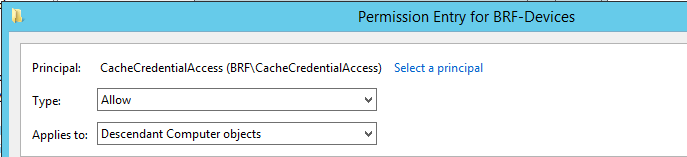
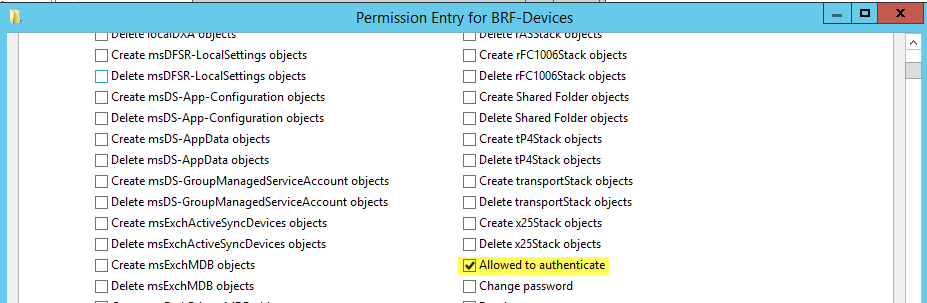
Click Select a Principal and find the domain local group you created previously, ensure the type is set to Allow and the Applies to is set to Descendant Computer Objects. Once the permissions have loaded you want to find and check off the permission Allowed to authenticate. You may have to screen down the list of available permissions to find it. Click Ok, once completed.
-
Back on the Advanced Security Settings screen, click Apply and close both menus.
-
Repeat this process for any OU that you have migrating workstations to ensure each workstation is allowing the domain local group the ability to authenticate so we can pre cache their credentials prior to cutover.
-
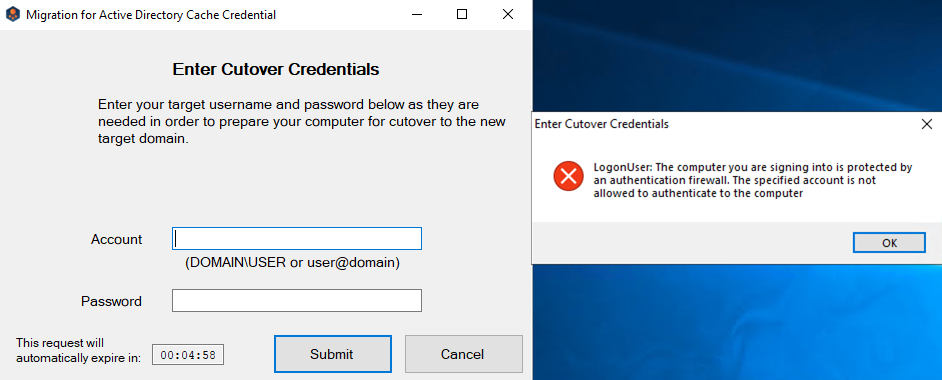
Once all the steps have been completed you should be able to successfully run the Cache Credentials action without error. If you are getting the below error for a workstation, ensure that the domain local group has been assigned the permission to authenticate to it.
Post Migration Cleanup
Once migrations have completed you can safely tear down the trust relationship and remove any assigned permissions for the domain local group.
About Us
Quest creates software solutions that make the benefits of new technology real in an increasingly complex IT landscape. From database and systems management, to Active Directory and Office 365 management, and cyber security resilience, Quest helps customers solve their next IT challenge now. Around the globe, more than 130,000 companies and 95% of the Fortune 500 count on Quest to deliver proactive management and monitoring for the next enterprise initiative, find the next solution for complex Microsoft challenges and stay ahead of the next threat. Quest Software. Where next meets now. For more information, visit www.quest.com.
Technical support resources
Technical support is available to Quest customers with a valid maintenance contract and customers who have trial versions. You can access the Quest Support Portal at https://support.quest.com.
The Support Portal provides self-help tools you can use to solve problems quickly and independently, 24 hours a day, 365 days a year. The Support Portal enables you to:
-
Submit and manage a Service Request
-
View Knowledge Base articles
-
Sign up for product notifications
-
Download software and technical documentation
-
View how-to-videos
-
Engage in community discussions
-
Chat with support engineers online
-
View services to assist you with your product.
