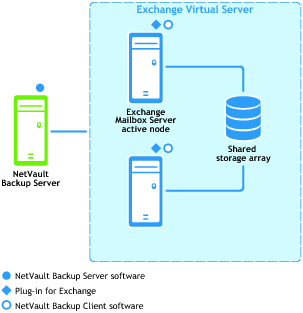
Single Copy Cluster (SCC) or Failover Cluster
|
• |
Supported Exchange Server Versions: Exchange 2007 only |
|
• |
Supported Exchange Server Editions: Enterprise only |
|
• |
Supported Backup Methods: ESE and VSS |
|
• |
Plug‑in for Exchange License Required: Plug‑in for Exchange Enterprise Edition Cluster Support |
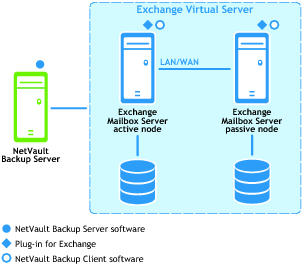
Cluster Continuous Replication (CCR)
|
• |
Supported Exchange Server Versions: 2007 only |
|
• |
Supported Exchange Server Editions: Enterprise only |
|
• |
Supported Backup Methods: ESE (Active Copy only) and VSS (Active or Passive Copy) |
|
• |
Plug‑in for Exchange License Required: Plug‑in for Exchange Enterprise Edition Cluster Support |