Working with Inactive Mailboxes
Working with Inactive Mailboxes
On Demand Recovery supports restore of inactive mailboxes of hard-deleted users. The Federated Domain scenario is also supported. This feature requires Recovery Manager for Active Directory 9.0 or higher.
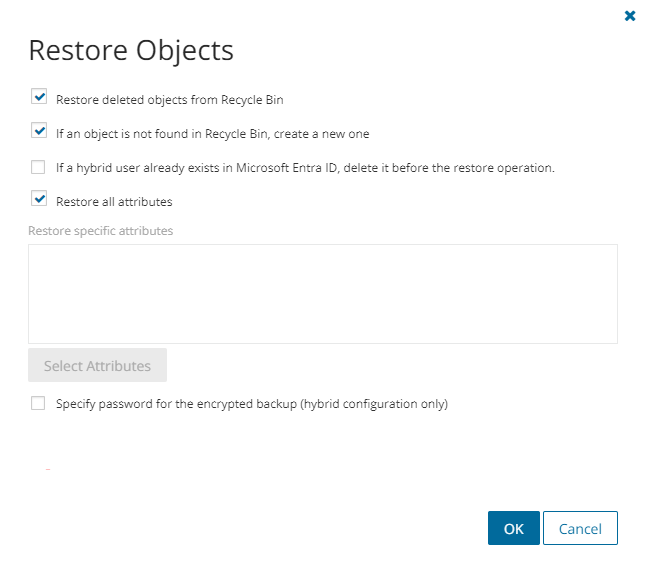
To preserve the original cloud mailbox of a hybrid user after restore, you have to select the If a hybrid user already exists in Microsoft Entra ID, delete it before the restore operation option in the Restore Object dialog.
You can backup and restore data related to inactive mailboxes.
Backup data related to inactive mailboxes
To backup data related to inactive mailboxes:
- Click Manage backups on the Dashboard screen.
- Select the tenant from the list.
The Configure backup dialog opens.
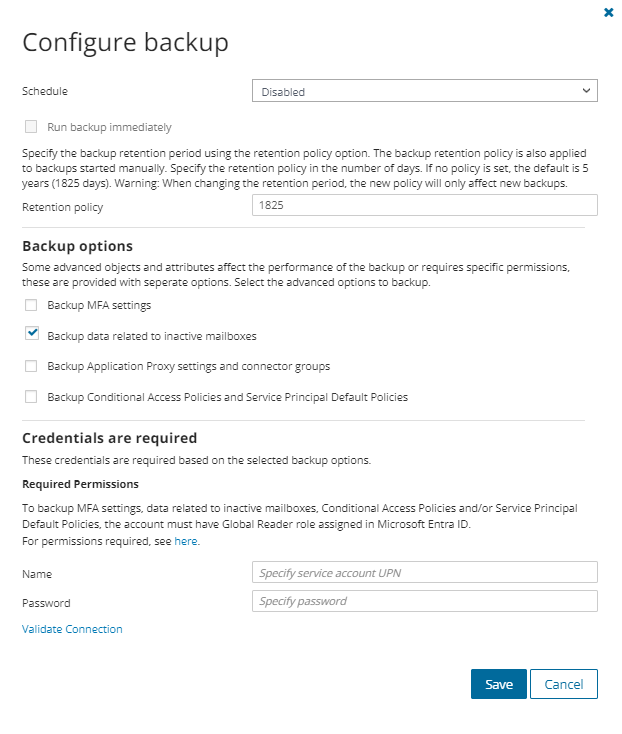
- Select the Backup data related to inactive mailboxes option and specify service account credentials for the tenant. The specified account must have the Global Reader role assigned in Microsoft Entra ID.
- Click Save.
Restore data related to inactive mailboxes
To restore data related to inactive mailboxes:
- On the Dashboard tab, click Manage Restores.
- A list of tenants will appear. Select the name of the tenant that you would like to specify account credentials.
- On the Configure Restore screen, enter the username and password credentials for the service account. The specified account must have the Authentication Administrator role assigned in Microsoft Entra ID.

- Click Save.
User scenario
- There is a hybrid user. This user is deactivated by the administrator for some reason. This means that the user account goes to the Recycle Bin. After 30 days, Microsoft Entra ID cleans this account from the Recycle Bin.
- Then, the user returns and the account is enabled again by the administrator. After the activation, the user is recreated in the cloud with the new mailbox.
- We want to use the original cloud mailbox for the user. The only one way to do this is to restore the user from the backup. But before the restore, the newly created cloud user must be removed from Microsoft Entra ID using this new option.
If you restore a hybrid user and their mailbox with On Demand Recovery
- For Non-Federated Domains, On Demand Recovery restores a cloud user and its mailbox without an on-premises user.
- For Federated Domains, restore of hybrid users requires Recovery Manager for Active Directory. In this scenario, On Demand Recovery restores a hybrid user and its mailbox in the cloud. Recovery Manager for Active Directory restores this hybrid user on premises, then it calls Microsoft Entra Connect to synchronize the user back to the cloud and make the cloud user previously restored by On Demand Recovery be in the Federated Domain. Without Recovery Manager for Active Directory, the cloud user will be non-federated after restore and you will not log in with this user.
Hybrid Connection Port and Protocol Requirements
Hybrid Connection Port and Protocol Requirements
Hybrid configuration with Recovery Manager for Active Directory requires only outbound TCP/UDP port 443 to be opened on the Recovery Manager Portal server to access the internet. If the Recovery Manager Portal server already has access to the internet, you do not need to change the Firewall configuration.
|
|
Note: If you do not want to open all outbound IP Prefixes and your firewall or proxy allows DNS allow lists, you can add connections to <your name space>.servicebus.windows.net to your allow list. |
Table 4: Hybrid connection port and protocol requirements
| HTTPS |
443 (TCP/UDP) |
Outbound |
Figure 2: Hybrid Restore Components Diagram
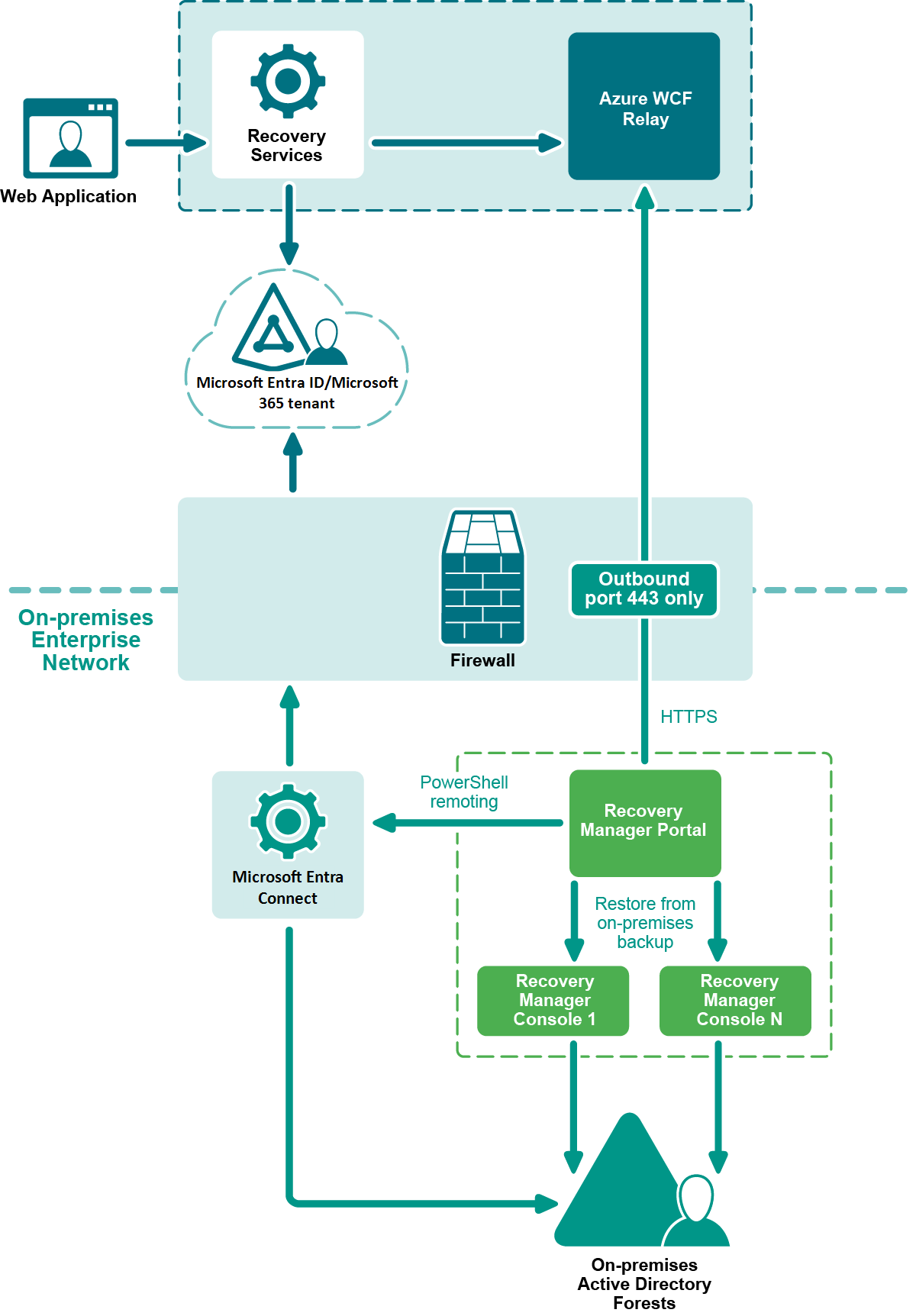
Hybrid Connection Security
FIPS 140-2 compliant TLS protocol is used for traffic encryption. HTTPS certificate is validated on our client side (Recovery Manager Portal).
Server side is Azure WCF Relay that is created and configured in Quest Azure Subscription.
Shared Access Signature (SAS) is used for authentication. A SAS token is based on an access key generated by On Demand Recovery cloud. This key is downloaded to the on-premises server with Recovery Manager Portal and used in the portal configuration to establish the Hybrid connection (from on-premises to the cloud). The SAS token is sent to the cloud and verified on each connection request. For details about Shared Access Signature algorithm, click the following link: https://docs.microsoft.com/en-us/azure/service-bus-relay/relay-authentication-and-authorization.
Restoring Email Address or Phone for Self-Service Password Reset
Restoring Email Address or Phone for Self-Service Password Reset
On Demand Recovery restores an email address or phone that was specified as an authentication method for the self-service password reset user option in the Azure portal. So users can reset their passwords without help of the tenant administrator.
Supported scenarios
The following scenarios are supported by On Demand Recovery:
- Restoring email, mobile phone number, and office phone number for the self-service password reset option.
|
|
Note: Because of Microsoft requirements, hard deleted objects will receive a new Object ID upon restore of these objects. Please consider the implications of having a new Object ID after restoring these objects. |
Limitations
The following scenarios are not supported by On Demand Recovery:
- Restoring user passwords and the password reset is the only option to log in to the Azure portal after the restore of a permanently deleted user.
- The following authentication methods are not restored; security questions, mobile app notification, and mobile app code.
For details on how to enable self-service password reset in your Microsoft Entra tenant, click here.
To log in to the Azure portal after the user restore if an email address was specified as authentication method for the password reset option
- Go to the Azure portal and enter the user name.
- On the Enter password screen, click Forgot my password.

- On the Get back into your account screen, type the user name and prove that you are not a robot by entering the characters you see on the screen, and then select Next.

- On the next screen, select Email my alternate email, and then select Email.

- Type the verification code from the email into the box, and then select Next.
- Type and confirm your new password, and then select Finish. Your password has been reset and can be used to log in to the Azure portal.

- Log in with the new password.
- Then you may see the screen where you will be asked to verify your email address if the Converged service is not enabled in your environment. You can click Cancel and verify the email address later.
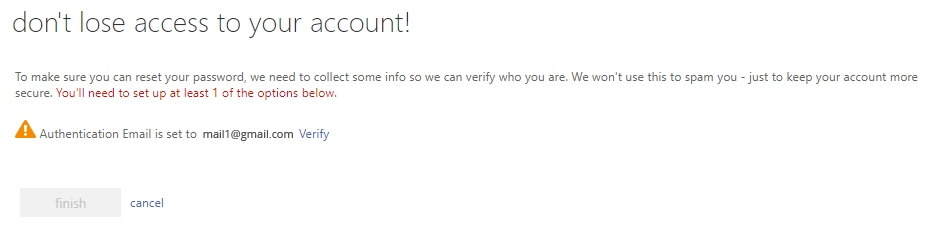
- If the Converged service is enabled, you will get the screen like below. In this case, no further action is required.