Restoring Groups
In Microsoft Entra ID, there are two types of groups; Security and Microsoft 365. When a Microsoft 365 group is deleted in Microsoft Entra ID, it is soft deleted. That is, the Microsoft 365 group is moved to the Deleted groups page where it can be restored or permanently deleted. When a security group is deleted in Microsoft Entra ID, it is hard deleted. That is, the security group is permanently deleted and not moved to the Deleted groups page. The Differences report in On Demand Recovery identifies groups as being either hard deleted or soft deleted in Microsoft Entra ID. Both types of groups can be restored from the Differences report.
Supported scenarios
The following scenarios are supported in On Demand Recovery:
- Restoring security groups and group membership
- Restoring Microsoft 365 groups and group membership
- Restoring dynamic groups
- Restoring group owners associated with a security group
- Restoring group owners associated with a Microsoft 365 group
|
|
Note: Because of Microsoft requirements, hard deleted objects will receive a new Object ID upon restore of these objects. Please consider the implications of having a new Object ID after restoring these objects. |
Restored group attributes
For a list of group attributes restored by On Demand Recovery, visit the On Demand Recovery Supported Attributes guide.
Limitations
The following groups are not restored by On Demand Recovery:
Restoring Service Principal Objects
Restoring Service Principal Objects
On Demand Recovery supports backing up and restoring service principal objects with the following properties:
- oAuth2PermissionGrants - the OAuth 2.0 scopes (delegated permissions) that have been granted to an application (represented by a service principal) as part of the user or admin consent process.
- appRoleAssignments - link between a service principal and a directory object.
- roles - administrator roles in Microsoft Entra ID. Refer to this article for details.
- appRoles - the collection of application roles that an application may declare.
- Service principal owners - the owners are a set of users who are allowed to modify service principal objects.
For the full list of service principal attributes that are restored and not restored by On Demand Recovery, see How does On Demand Recovery Handle Object Attributes?
|
|
Note: Due to the design specifications set by Microsoft, the default App Role can only be assigned to a principal if the corresponding resource application has not declared any App Roles. This limitation prevents On Demand Recovery from restoring default application role assignments for such principals. See Microsoft documentation for more information. |
|
|
Note: Because of Microsoft requirements, hard deleted objects will receive a new Object ID upon restore of these objects. Please consider the implications of having a new Object ID after restoring these objects. |
What is the difference between a service principal object and an application object?
When you register a Microsoft Entra application in the Azure portal, two objects are created in your Microsoft Entra tenant; an application object and a service principal object.
- Application object
A Microsoft Entra application is defined by its one and only application object, which resides in the Microsoft Entra tenant where the application was registered, known as the application's "home" tenant. The Microsoft Graph Application entity defines the schema for an application object's properties.
- Service principal object
In order to access resources that are secured by a Microsoft Entra tenant, the entity that requires access must be represented by a security principal. This is true for both users (user principal) and applications (service principal). The security principal defines the access policy and permissions for the user/application in that tenant. This enables core features such as authentication of the user/application during sign-in, and authorization during resource access.
When an application is given permission to access resources in a tenant (upon registration or consent), a service principal object is created. The Microsoft Entra Graph ServicePrincipal entity defines the schema for a service principal object's properties.
For more details, see https://www.microsoftpressstore.com/articles/article.aspx?p=2473127.
Service principals provisioned from Microsoft Entra Gallery
On Demand Recovery supports restoring service principals provisioned from Microsoft Entra Gallery.
Limitations: On Demand Recovery does not backup certificate settings for applications.
To make SAML SSO work after the restore of a service principal provisioned from Microsoft Entra Gallery, you must install the new certificate for the corresponding application. For details on how to provide the certificate for a particular application, refer to the application configuration guide.
To access the application configuration guide
- In Azure Management Portal, navigate to the Microsoft Entra ID section in the left pane and click Enterprise applications.

- Choose the application for which you want to configure single sign-on.
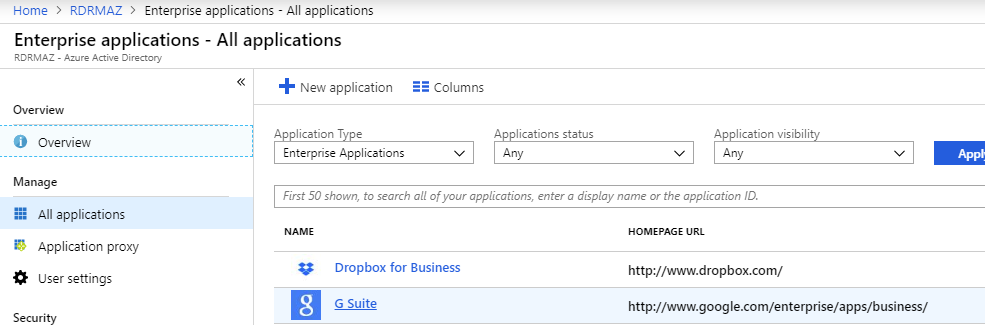
- Under the Manage section, select Single sign-on.

- Click the configuration guide link.
Which actions are shown in the Differences report for a service principal?
- Deletion of a service principal object
- Changes to the accountEnabled attribute
- Add/remove roles assigned to service principals (custom roles are not monitored)
- Add/remove owners from service principals
- Add/remove owners from application
Names of administrator roles in the Azure portal are slightly different from the names of the corresponding roles that are shown in the Differences report. For information, see the following comparison table:
Table 1: Names of administrator roles in the Azure portal and the corresponding role in the Differences report
| Global Administrator |
Company Administrator |
| Billing Administrator |
Billing Administrator |
|
Compliance Administrator |
Compliance Administrator |
| Conditional Access Administrator |
Conditional Access Administrator |
| Dynamics 365 Administrator |
CRM Service Administrator |
| Exchange Administrator |
Exchange Service Administrator |
| Guest Inviter |
Guest Inviter |
| Password Administrator |
Helpdesk Administrator |
| Azure Information Protection administrator |
Information Protection Administrator |
| Intune Administrator |
Intune Service Administrator |
| Skype for Business Administrator |
Lync Service Administrator |
| Power BI Administrator |
Power BI Service Administrator |
| Privileged role Administrator |
Privileged Role Administrator |
| Reports Reader |
Reports Reader |
| Security Administrator |
Security Administrator |
| Security Reader |
Security Reader |
| Service Administrator |
Service Support Administrator |
| User Administrator |
User Account Administrator |
Restoring Applications
You can restore applications from the Recycle Bin as well as hard deleted applications. On Demand Recovery performs the following actions when restoring applications:
- If there is an application in the Recycle Bin, it is restored. After the application is restored, On Demand Recovery restores application attributes that are in the backup.
- If there is no application in the Recycle Bin, On Demand Recovery attempts to restore it from the backup.
Supported scenarios
The following scenarios are supported by On Demand Recovery:
- Restoring soft deleted applications.
- Restoring hard deleted applications.
- Restoring applications from the Recycle Bin.
|
|
Note: Because of Microsoft requirements, hard deleted objects will receive a new Object ID upon restore of these objects. Please consider the implications of having a new Object ID after restoring these objects. |
Restoring Application Proxy Settings
Restoring Application Proxy Settings
On Demand Recovery supports the recovery of Application Proxy settings, Connector groups, and Connector group membership.
Supported scenarios
The following scenarios are supported in On Demand Recovery:
- Restoring changes to Application Proxy configuration.
- Restoring connector group membership if an Application Proxy is moved into another connector group.
- If an Application Proxy is moved into another connector group and the previous connector group was deleted, On Demand Recovery puts the Application Proxy back to the connector group with the same name.
- If an Application Proxy is put into another connector group and the previous connector group is deleted and there is no connector group with the same name, the new connector group with this name will be automatically recreated and the Application Proxy will be put into it.
Limitations
All of the Application Proxy settings can only be restored at once, granular restore of Application Proxy settings is not supported.
Configuration data restored for an Application Proxy item
On Demand Recovery restores the following configuration data for an Application Proxy item:
Connector Groups
For deleted connector groups, On Demand Recovery restores the following attributes:
Other connector group data is currently backed up but cannot be restored.
OnPremisesPublishing Settings
An onPremisesPublishing object represents the set of properties for configuring Application Proxy for an on-premises application.
- externalUrl
- internalUrl
- externalAuthenticationType
- isTranslateHostHeaderEnabled
- isTranslateLinksInBodyEnabled
- isOnPremPublishingEnabled
- isHttpOnlyCookieEnabled
- isSecureCookieEnabled
- isPersistentCookieEnabled
- applicationServerTimeout
- useAlternateUrlForTranslationAndRedirect
For details, see https://docs.microsoft.com/en-us/graph/api/resources/onpremisespublishing?view=graph-rest-beta.
Connectors
Connector data is currently backed up but cannot be restored.
- id
- machineName
- externalIP
- status
- connectorGroupId
Prerequisites
Backing up Application Proxy settings is not enabled by default. You must select this option when configuring backup options.
To backup Application Proxy settings and connector groups
- Click Manage backups on the Dashboard screen.
- Select the tenant from the list and click Edit.
The Configure backup dialog opens.
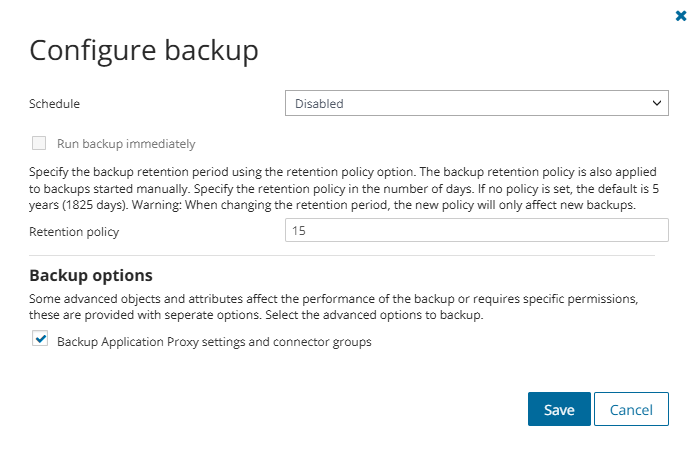
- Select the Backup Application Proxy settings and connector groups option.
- Click Save.
For details, see How does On Demand Recovery Handle Object Attributes?