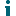Using the QoreStor command line interface
QoreStor includes a custom shell implementation that simplifies command line access. As a superuser, you can use the command /opt/qorestor/bin/setup_qs_user <username> to configure an existing shell user with sudo privileges to run QoreStor CLI commands. You can access the QoreStor command line through a remote access program (such as PuTTY) or through the QoreStor UI Web Terminal.
|
|
NOTE: The user created with /opt/qorestor/bin/setup_qs_user<username> cannot run any other commands with sudo, only QoreStor CLI commands. |
To access the QoreStor command line
- Using a remote access program, connect to your QoreStor server.
- Log in using the superuser credentials or the credentials of the user configured for QoreStor CLI access using setup_qs_user.
- Enter the desired command at the prompt using one of the following command styles:
- If logged in as the superuser, use the full path; for example, /opt/qorestor/bin/system -show or /opt/qorestor/bin/qs_help.
- If logged in as a user configured by setup_qs_user, type system -show or help.
|
|
NOTE: Refer to the QoreStor Command Line Reference Guide for more information on the QoreStor CLI. |
Using the QoreStor REST API
QoreStor provides a REST API in order to provide an efficient method for application management or integration. For more information on using the REST API, see the sections below.
API Overview
All API requests should be sent to https://<QoreStor host>:5233/api. With the exception of the Authentication request, all requests should carry the HTTP header Authorization: Bearer <token>.
API calls will generate one of the response types below. Refer to the API documentation for the specific request for more information on expected responses.
- 200 - OK
- 400 - Bad request
- 401 - Unauthorized
- 404 - Not found
- 500 - Internal server error
Authentication
Authentication to the API is accomplished using the username and password for an existing QoreStor account. Once logged in, a token will be generated that can be used to authenticate API commands.
To use API authentication:
- Run the login request using the username and password for the desired QoreStor account as well as the IP or domain name of your QoreStor server.
curl -X POST "https://QoreStor.host.com:5233/api/auth/login" -H "accept: application/json" -H "Content-Type: application/json" -d "{ \"name\": \"TestUser\", \"password\": \"TestUserPassword\"}"
- In the request response, find and record the value for JWT_Token.
- For subsequent API requests, ensure that the header contains the value Authorization: Bearer <token>.
You may also use this token to authorize API requests via the documentation page. To do so,
- At the top of the API documentation page, click Authorize.
- In the Value field, enter the token.
- Click Authorize.
API Documentation
The detailed documentation for the QoreStor API is hosted on your QoreStor serer. To view the documentation, enter the URL below into a browser.
https://<QoreStor Server>:5233//api/docs/index.html
|
|
NOTE: In the example above, replace <QoreStor Server> with the FQDN or IP address of your QoreStor server. |
The API documentation contains the following:
- An Authorize button to enable authentication.
- A list of available API resource categories. Each list is expandable to reveal the resources in each category.
- Each resource listing can be expanded to view the resource description, parameters and responses, and a Try it Out button that can be used to run the API call with entered parameters.
To view and test an API
|
|
NOTE: The example below uses the GET containers request. The steps are similar for other requests. |
- Before testing the API, authenticate as described in Authentication.
- In the resource list, expand Containers.
- Find the Get Containers request (GET/v1/Containers) and click to expand.
- Click Try it Out. Note that the parameters fields are now enabled.
|
|
NOTE: Parameters for Get Containers are optional. Some requests have required parameters. |
- Optionally, enter the parameters as described below:
- Storage Group - The name of the storage group to which the containers belong
- Type - required container type (cloud, link, or tier)
- Click Execute.
Understanding RDA immutabilty
RDA immutability provides protection from overwrites and deletes on backup files. This technology is present by default for RDS containers, but not all backups are protected by default. Backup applications sending data using the RDA protocol to QoreStor define whether the backup data should be immutable and the time period the data will remain immutable. After you set immutability on the backup data, you cannot modify or delete the backup data from the RDA container until the immutable time period expires. For the current list of supported backup applications that take advantage of this technology, see the Quest QoreStor Interoperability Guide.
Configuring QoreStor settings
Configuring the DR Series system settings
In the QoreStor GUI, you can easily view and configure system settings such as, active directory, system date and time, expansion shelf enclosures, licenses, networking, schedules for system operations, SSL certificates, storage groups, and users.