Configuring advanced agent settings
|
1 |
|
2 |
In the Advanced Scanning Options dialog box, provide the following information: |
|
• |
Max scanning depth: indicates the maximum number of hops from a host on the scanning list that a reference-listed host can be for the agent to attempt to collect dependency information about it. |
|
• |
Report connection: when selected, the agent collects details about the connections used by each process (including the ports in use), and reports them as part of the monitoring data. This information is shown on the tabular dependency view. |
|
• |
Submit detail: if enabled, the agent submits detailed observations about the connections. The connection details are displayed in the Netstat Dependency Detail tab. |
|
• |
Exclude agent host: when selected, the agent’s host is excluded from the scanning list. |
|
• |
Use sudo to collect process information: when selected, the agent uses the sudo command to collect process information (by default, this check box is selected). |
|
NOTE: Some UNIX versions report process information only when sudo is used. The account must be in the sudoers list. This setting does not apply to Windows hosts. Recommended: set up your system to enable sudo without a password for the netstat command only. This is possible in many environments. For more information, see your operating system reference documentation. |
|
3 |
Save the new settings to apply them to the selected agent. |
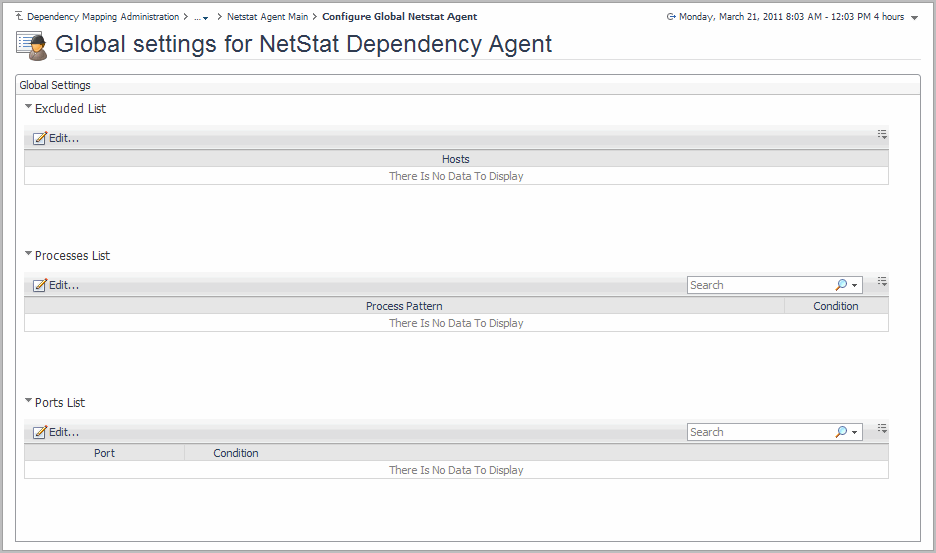
Configuring global agent settings
|
1 |
|
• |
Excluded List - hosts that should never be scanned by agents when collecting the dependency mapping for this environment. For details, see Configuring the excluded list . |
|
• |
Processes List - processes that should always be included or excluded from scanning by all existing or future agents, when collecting the dependency mapping for this environment. For details, see Configuring the processes list . |
|
NOTE: For example, you may want to always exclude the backup.exe process from scanning. For include, you are globally limiting the agents to include only the processes specified in these global settings, or the processes which are specifically included in an agent’s settings. |
|
• |
Ports List - ports that should always be included or excluded from scanning by all existing or future agents, when collecting the dependency mapping for this environment. For details, see Configuring the ports list . |
|
When set to include, the regular expression should be included in the scanning. When set to exclude, the regular expression should be excluded from the scanning. |
|
When set to include, the port range should be included in the scanning. When set to exclude, the port range should be excluded from the scanning. |
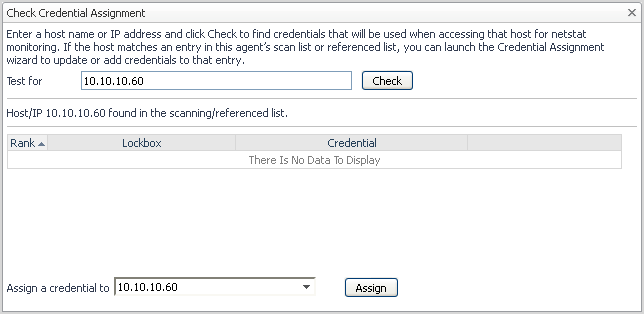
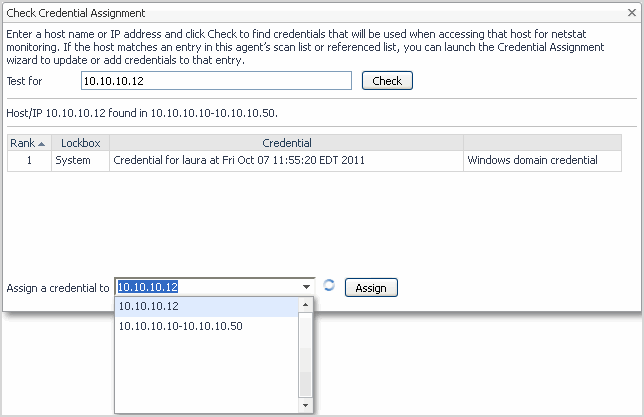
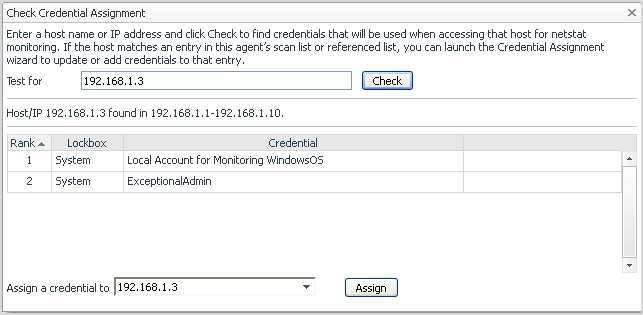
Checking credential assignment
Find the credentials that are used when accessing a select host for Netstat monitoring.
|
1 |
|
2 |
In the Test for field type the host name or the IP address for the host you want to verify, then click Check. |
|
• |
If the system finds no credentials defined for this host: Select the host in the Assign a credential to box, then click Assign. The Assign Credentials dialog box appears, with the host’s check box pre-selected. Assign an existing credential to the selected host, or create a new credential for it, by following the procedure presented in section Assigning credentials to select hosts . |
|
• |
To use the IP range’s credentials, select the range in the Assign a credential to box, then click Assign. The Assign Credentials dialog box appears, with the range’s check box pre-selected. Assign an existing credential to all hosts in this range, by following the procedure presented in section Assigning credentials to select hosts . |
|
• |
To create a new credential for that host, other than the one already defined for the range it is part of, select the host in the Assign a credential to box, then click Assign. The Assign Credentials dialog box appears, with the host listed under “Unconfigured List”. Create a new credential for this host by following the procedure presented in section Assigning credentials to select hosts . |
|
• |
If the system finds several credentials defined for this host, these credentials are presented in order of their rank in the results table. You can edit the rank in the Credential Management dashboard. To assign an existing credential to the selected host, or create a new credential for it, select the host in the Assign a credential to box, then click Assign. The Assign Credentials dialog box appears, with the check box for this host already pre-selected. Continue by following the procedure presented in section Assigning credentials to select hosts . |
Assigning credentials to select hosts
|
1 |
|
2 |
On the Assign Credentials dialog box, select the host or range of hosts to which you want to assign credentials by selecting their check boxes. |
|
3 |
To use the credentials for the Windows domain, select the Use Windows domain credentials check box. |
|
4 |
Click Assign Credentials. |