© 2019 Quest Software Inc. ALL RIGHTS RESERVED.
This guide contains proprietary information protected by copyright. The software described in this guide is furnished under a software license or nondisclosure agreement. This software may be used or copied only in accordance with the terms of the applicable agreement. No part of this guide may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying and recording for any purpose other than the purchaser’s personal use without the written permission of Quest Software Inc.
The information in this document is provided in connection with Quest Software products. No license, express or implied, by estoppel or otherwise, to any intellectual property right is granted by this document or in connection with the sale of Quest Software products. EXCEPT AS SET FORTH IN THE TERMS AND CONDITIONS AS SPECIFIED IN THE LICENSE AGREEMENT FOR THIS PRODUCT, QUEST SOFTWARE ASSUMES NO LIABILITY WHATSOEVER AND DISCLAIMS ANY EXPRESS, IMPLIED OR STATUTORY WARRANTY RELATING TO ITS PRODUCTS INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, OR NON-INFRINGEMENT. IN NO EVENT SHALL QUEST SOFTWARE BE LIABLE FOR ANY DIRECT, INDIRECT, CONSEQUENTIAL, PUNITIVE, SPECIAL OR INCIDENTAL DAMAGES (INCLUDING, WITHOUT LIMITATION, DAMAGES FOR LOSS OF PROFITS, BUSINESS INTERRUPTION OR LOSS OF INFORMATION) ARISING OUT OF THE USE OR INABILITY TO USE THIS DOCUMENT, EVEN IF QUEST SOFTWARE HAS BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. Quest Software makes no representations or warranties with respect to the accuracy or completeness of the contents of this document and reserves the right to make changes to specifications and product descriptions at any time without notice. Quest Software does not make any commitment to update the information contained in this document..
If you have any questions regarding your potential use of this material, contact:
Quest Software Inc.
Attn: LEGAL Dept
4 Polaris Way
Aliso Viejo, CA 92656
Refer to our Web site (https://www.quest.com) for regional and international office information.
Patents
Quest Software is proud of our advanced technology. Patents and pending patents may apply to this product. For the most current information about applicable patents for this product, please visit our website at https://www.quest.com/legal.
Trademarks
Quest, the Quest logo, and Join the Innovation are trademarks and registered trademarks of Quest Software Inc. For a complete list of Quest marks, visit https://www.quest.com/legal/trademark-information.aspx. All other trademarks and registered trademarks are property of their respective owners.
Legend
|
|
Warning: A WARNING icon indicates a potential for property damage, personal injury, or death. |
|
|
Caution: A CAUTION icon indicates potential damage to hardware or loss of data if instructions are not followed. |
|
|
|
Desktop Authority Administrator Guide
Updated - December 2019
Software Version - 11.1
Quest Desktop Authority, the leading desktop management platform for Windows-based networks, significantly reduces total cost of desktop and application ownership by enabling administrators to proactively secure, manage, support and inventory desktops and applications from a central location. Desktop Authority centralizes control over desktop configurations, combining the functionality of logon scripting, group policies, user profiles and computer profiles into one comprehensive solution.
Desktop Authority is available in three versions, Desktop Authority Professional, Desktop Authority Standard and Desktop Authority Essentials. Desktop Authority Essentials is a scaled down version of Desktop Authority Professional. It does not include the following standard features included by default in the full version -- Software Management, USB/Port Security, Hardware and Software Inventory, Custom Reporting and the Desktop Authority Remote Management tool.
Desktop Authority Standard is a version of Desktop Authority that is geared towards enterprises who already use KACE Systems Management Appliance (SMA, previously known as K1000) or Microsoft's System Center Configuration Manager (SCCM) or other similar management tools. Since they provide tools for Software Distribution and Asset Management, Desktop Authority does not include its own built-in Software Distribution or Asset Management capabilities.
|
|
NOTE: Currently Desktop Authority Standard is the only version available to new customers for purchase. |
From a single server-based installation point, Desktop Authority assists administrators with the never-ending chore of configuring each desktop attached to the network. When a user logs on or off, their personalized configurations are applied to their environment. The Operating System and applications get "fine-tuned" to the specific user. Best of all, Desktop Authority does this without requiring you to reduce overall security, without maintaining separate security policies and without the need for a network administrator to visit each computer.
Desktop Authority allows administrators to centrally manage over 30 different categories of desktop settings including drive mappings, search paths, printer deployment, Windows Firewall ports, Internet configuration & proxy settings, Microsoft Office paths, service pack, Group Policy Templates, Security Policies, desktop shortcuts, automatic mail profile creation for Outlook/Exchange, file operations, registry settings and more.
Desktop Authority also attends to each computer in the enterprise. Using a computer based agent, each computer can be configured and inventoried, independent of the users that log on to the computer.
Desktop Authority uses its patented Validation Logic technology to determine how each desktop will be configured. The Validation Logic technology is based on over 20 validation types including the class of computer (such as desktop or portable), client operating system, group membership, Active Directory sites, OUs, and registry and file properties. Selection can be enhanced further using AND/OR expressions to combine multiple Validation Logic rules. Custom validation types can also be defined to allow configuration by desktop attributes list, Asset Tags or hardware configuration.
|
|
Note: Not available in Desktop Authority Essentials. |
MSI packages contain all necessary files an application needs in order for it to be installed using Microsoft's Windows Installer. Desktop Authority manages a repository of Microsoft Windows Installer (MSI) packages. Packages can be deployed to and/or removed from specified desktops based on User and/or Computer specifications.
|
|
Note: Not available in Desktop Authority Essentials |
The myriad of portable storage mediums today make it essential for corporations to prohibit or monitor the use of certain devices on the company network. These devices can be very harmful to a corporation. Confidential data can easily be copied to any portable device, viruses can be introduced to the network and spread corporate wide and illegal software can be copied to the company network.
Since most portable devices are small in size it is simple for any employee to use these devices regardless of a written or verbal company policy. The user's ability to use these devices and/or transfer data to and from these devices must be restricted. The USB/Port Security object will do just this.
Users and/or groups of users can be restricted from using certain types of removable storage devices. Desktop Authority's USB/Port Security object will protect the company network against unauthorized usage of devices such as MP3 players, PDAs, WiFi and more.
The USB/Port Security Option can help to free the enterprise of unwanted removable storage devices, easily and quickly.
In larger organizations there are typically multiple levels of administrators, with junior ones assigned to specific geographical locations or restricted administration tasks. Desktop Authority’s new architecture allows Super Users to restrict other administrators to only view, change, and add or delete a limited set of configuration objects. By defining roles and applying those roles to users or groups at the profile level, SuperUsers can ensure that administration of Desktop Authority follows enterprise security boundaries.
|
|
Note: Not available in Desktop Authority Essentials. |
Desktop Authority profiles and their configurations are stored in an SQL database, along with information about the managed desktop. Built-in and custom reporting puts vital information at the fingertips of administrators, including reports on hardware and software inventory, and user activity.
Comprehensive Reporting includes built-in and custom reporting on Hardware/Software Inventory, User Activity and Desktop Authority configuration.
Desktop Authority uses several components to facilitate the configuration of desktops and servers. These components include the Desktop Authority Manager, Configuration and Reporting databases, Server Processes and the Desktop Agent. These components all work together to provide an efficient, scalable, and secure desktop management system.
Figure 1: Overview the Desktop Authority system

The Desktop Authority Manager is the central console from which configuration profiles, services and reports are managed by the Network Administrator. The Manager also provides the ability to remotely manage client computers over the local area network or Internet.
Once configuration data is saved and ready to be configured on client computers, the data is published to the NETLOGON and the Device Policy Master shares. This is done using replication. The replication process updates the replication targets for all target servers specified in the Server Manager object. Data is extracted from the DACONFIGURATION database and written to configuration files in the replication shares. The data is used to configure user based settings when a user logs in to each client machine. Computer based settings are configured and executed on each client, by the local Computer Management agent. The agent is deployed to each client using Smart Client Provisioning (Logon and/or GPO Based deployment).
The Desktop Authority Manager Service is the business logic layer for the Manager. It manages communications between the Manager and the SQL databases, DACONFIGURATION and DAREPORTING.
The DA Administrative service enables Desktop Authority to perform tasks that require administrative rights without sacrificing user-level security at the workstation. This service helps Desktop Authority perform these specialized tasks by insuring that the client configuration files are correctly signed.
The Update Service is used for file distribution purposes by Desktop Authority, but is only needed when the Software Distribution feature is in use. The service can be installed on one or more servers within a domain.
Desktop Authority may be installed to a Domain Controller, however it is strongly suggested that Desktop Authority be installed to a Member Server. The installation server is known as the Operations Master. The Operations service is hosted on the Operations Master. This service manages and supports the ETLProcessor and ReportScheduler plugins. This service is installed once per domain on the Operations Master.
Desktop Authority can install Microsoft SQL Server 2014 Express Edition on the Operations Master server or use an existing SQL Server 2008, 2008 R2, 2012, 2014, 2016, 2017 or 2019 instance. Within this SQL instance there are two databases created. They are DACONFIGURATION and DAREPORTING. The DACONFIGURATION database is used to store product configuration data. The DAREPORTING database stores a copy of the profile configuration data, hardware and software inventory, user activity and other essential data that is collected for reporting purposes (not available for Desktop Authority Essentials).
There are two ways in which Desktop Authority can deploy the necessary client files to machines that will be managed by Desktop Authority. Desktop Authority uses Smart Client Provisioning which encompasses both GPO-based Deployment and Logon-based Deployment. Smart Client Provisioning dynamically chooses from the best of several deployment approaches at runtime. The specific technique used depends on the client environment, and the obstacles present in that environment. Click here for more detailed information on Smart Client Provisioning.
Computer Management objects are executed on each client by the Computer Management agent. The Computer Management agent is a service that is deployed to each client as a part of the Smart Client Provisioning process. The agent service interprets the Computer Management object settings and executes them at the appropriate startup, shutdown, refresh and scheduled events.
As each user logs on to the network and is authenticated, the user's logon script is executed. Desktop Authority is launched via a logon script named SLOGIC. This script must be defined as the user’s logon script in order for a client to execute Desktop Authority. The logon script performs initializations and launches the Desktop Authority engine. Desktop Authority User Management configurations can be executed at logon, refresh and logoff events.
Once the logon script performs its initial checks, the Desktop engine is launched. The engine will initiate the configuration of objects and elements. First, the Global Options are applied, user defined variables are processed and Pre-Engine custom scripts are executed. If configured, the USB/Port Security and MSI Packages components are launched on the client.
From here, clients are configured with the settings defined in the Manager. Once these settings are complete the engine will execute post-engine custom scripts. Finally, when the logon script completes, reporting data is collected, including hardware and software inventory, and the client desktop is loaded.
Upon logoff, the Desktop engine is again launched. This time any configuration elements found to validate for Logoff timing and for the user and/or computer, will execute. During logoff there is an optional visual indicator that can display to let the user know that something is happening.
A Dynamic Variable represents an area in memory that is reserved to hold a specific value. The value of the variable is dynamic in that the value will differ based on the current user. These variables are used to hold temporary values during the execution of a logon or custom script. All Desktop Authority dynamic variables are prefixed with a dollar ($) sign. The rules for defining new dynamic variables follow the KiXtart guidelines. More information on KiXtart can be found at www.kixtart.org/.
There are two categories of Dynamic Variables: Predefined and Custom. Predefined dynamic variables are ones that are defined by Desktop Authority. Custom Scripts may override the value of these variables. Desktop Authority can also make use of User Defined Custom dynamic variables.
In the Desktop Authority Manager, predefined dynamic variables are used to aid in the creation of configuration elements. The great thing about these variables is that since their values change based on the current user/computer, a single configuration entry can be used for all users/computers. You can be assured that at runtime when the logon script is executed, the predefined dynamic variable will contain the documented value based on the current user/computer.
For example, the predefined dynamic variable $UserId can be used to denote the logon id of the current user. At runtime when the logon script is executed, the $UserId variable will contain the UserID of the user currently logging on to the network.
Dynamic variables can be used throughout the Manager by typing the name of the variable into the desired field or by pressing the F2 key when the cursor is in any entry box. Pressing F2 will display a dialog box similar to the following, allowing the selection of a predefined variable from a visual list.
To select a variable, select it in the list and click Insert or double-click the variable. The selected variable will be inserted into the field at the current cursor position. Click the Info link at the right side of the list to get more information about a dynamic variable.
Dynamic variables can also be used in custom scripts. When writing a custom script there is no popup list of valid predefined dynamic variables.
Click here for a complete list of predefined variables.
Example usage:
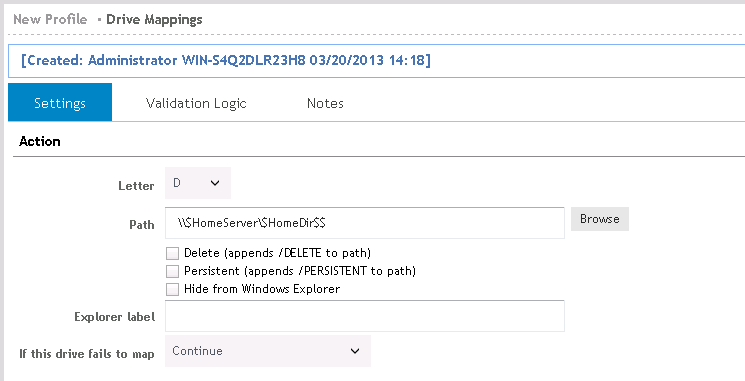
One of the most commonly used places for using Predefined Dynamic Variables is in the Drive mappings object. Use the $HomeServer and $HomeDir variables to map a home drive for your users.
Figure 2: Example usage of Dynamic Variable
Custom Dynamic Variables can be pre-defined for use in the Manager as well as in Custom Scripts. To use your custom dynamic variables in the Manager, simply add the variable definition to the Definitions tab of either the Global Options or the Profile dialogs. Defining a variable within Global Options makes the variable available everywhere, regardless of which profiles are processed on the client. Variables defined in the profile’s Definitions tab are available only if the profile in which the variable is defined is processed on the client. To add a custom variable, simply click Edit on the Definitions tab.
Example usage:
Instead of using the internal dynamic variable for the wallpaper file, a custom Dynamic Variable can be created. Modify either the Global Options or Profile Definitions file. Add a new custom variable called $customwallpaper. Other code can be wrapped around this definition to determine which group (department) the user belongs to. On the Display object, enter $customwallpaper in the Wallpaper file box. When the logon script is executed, the $customwallpaper variable is evaluated and set for each user.