The PostNightlyJobScript is run after every nightly job on the Core. It contains the parameter $JobClassName, which helps to handle those child jobs separately.
# receiving parameters from Nightlyjob
param([System.String]$JobClassMethod , [object]$NightlyAttachabilityJobRequest,
[object]$RollupJobRequest, [object]$Agents, [object]$ChecksumCheckJobRequest, [object]$TransferJobRequest,
[int]$LatestEpochSeenByCore, [object]$TakeSnapshotResponse)
# building path to Core's Common.Contracts.dll and loading this assembly
$regLM = [Microsoft.Win32.Registry]::LocalMachine
$regLM = $regLM.OpenSubKey('SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\AppRecovery Core 5')
$regVal = $regLM.GetValue('InstallLocation')
$regVal = $regVal + 'CoreService\Common.Contracts.dll'
[System.Reflection.Assembly]::LoadFrom($regVal) | out-null
$regVal2 = $regLM.GetValue('InstallLocation')
$regVal2= $regVal2 + 'CoreService\Core.Contracts.dll'
[System.Reflection.Assembly]::LoadFrom($regVal2) | out-null
# Nightlyjob has four child jobs: NightlyAttachability Job, Rollup Job,
# Checksum Check Job and Log Truncation Job. All of them are triggering the script,
# and $JobClassMethod (contains job name that calls the script) helps to handle those
# child jobs separately
switch ($JobClassMethod) {
# working with NightlyAttachability Job
NightlyAttachabilityJob {
$NightlyAttachabilityJobRequestObject = $NightlyAttachabilityJobRequest -as
[Replay.Core.Contracts.Sql.NightlyAttachabilityJobRequest];
echo 'Nightly Attachability job results:';
if($NightlyAttachabilityJobRequestObject -eq $null) {
echo 'NightlyAttachabilityJobRequestObject parameter is null';
}
else {
echo 'AgentIds:' $NightlyAttachabilityJobRequestObject.AgentIds;
echo 'IsNightlyJob:' $NightlyAttachabilityJobRequestObject.IsNightlyJob;
}
break;
}
# working with Rollup Job
RollupJob {
$RollupJobRequestObject = $RollupJobRequest -as
[Replay.Core.Contracts.Rollup.RollupJobRequest];
echo 'Rollup job results:';
if($RollupJobRequestObject -eq $null) {
echo 'RollupJobRequestObject parameter is null';
}
else {
echo 'AgentIds:' $RollupJobRequestObject.AgentIds;
echo 'IsNightlyJob:' $RollupJobRequestObject.IsNightlyJob;
}
$AgentsCollection = $Agents -as "System.Collections.Generic.List``1[System.Guid]"
if($AgentsCollection -eq $null) {
echo 'AgentsCollection parameter is null';
}
else {
echo 'Agents GUIDs:'
foreach ($a in $AgentsCollection) {
echo $a
}
}
break;
}
# working with Checksum Check Job
ChecksumCheckJob {
$ChecksumCheckJobRequestObject = $ChecksumCheckJobRequest -as
[Replay.Core.Contracts.Exchange.ChecksumChecks.ChecksumCheckJobRequest];
echo 'Exchange checksumcheck job results:';
if($ChecksumCheckJobRequestObject -eq $null) {
echo 'ChecksumCheckJobRequestObject parameter is null';
}
else {
echo 'RecoveryPointId:' $ChecksumCheckJobRequestObject.RecoveryPointId;
echo 'AgentIds:' $ChecksumCheckJobRequestObject.AgentIds;
echo 'IsNightlyJob:' $ChecksumCheckJobRequestObject.IsNightlyJob;
}
break;
}
# working with Log Truncation Job
TransferJob {
$TransferJobRequestObject = $TransferJobRequest -as
[Replay.Core.Contracts.Transfer.TransferJobRequest];
echo 'Transfer job results:';
if($TransferJobRequestObject -eq $null) {
echo 'TransferJobRequestObject parameter is null';
}
else {
echo 'TransferConfiguration:' $TransferJobRequestObject.TransferConfiguration;
echo 'StorageConfiguration:' $TransferJobRequestObject.StorageConfiguration;
}
echo 'LatestEpochSeenByCore:' $LatestEpochSeenByCore;
$TakeSnapshotResponseObject = $TakeSnapshotResponse -as
[Replay.Agent.Contracts.Transfer.TakeSnapshotResponse];
if($TakeSnapshotResponseObject -eq $null) {
echo 'TakeSnapshotResponseObject parameter is null';
}
else {
echo 'ID of this transfer session:' $TakeSnapshotResponseObject.SnapshotSetId;
echo 'Volumes:' $TakeSnapshotResponseObject.VolumeSnapshots;
}
break;
}
}Bourne shell (sh) is a shell language or command-line interpreter for Unix-based operating systems. Bourne shell is used in Rapid Recovery with Linux to customize environments and specify certain operations to occur in a predetermined sequence. The .sh is the file extension and naming convention for Bourne shell files.
Bourne Again Shell (Bash) is a similar shell language that implements the same grammar, parameter, and variable expansion, redirection and quoting. Bash also uses the same .sh file extension. The information here applies equally to Bash.
Using pre- and post-transfer, pre- and post-snapshot, and post-export script hooks, you can perform system operations before and after a transfer or snapshot, or after virtual export. For example, you may want to disable a certain cronjob while a transfer is occurring and enable it once the transfer has finished. As another example, you may need to run commands to flush application-specific data to disk. The contents are written to a temporary file and run using exec. The script then runs using the interpreter defined in the first line of the script, for example, (#!/usr/bin/env bash). If the specified interpreter is not available, the script uses the default shell defined in the $SHELL environment variable.
You can substitute and use any interpreter. For example, on the #! line of the script, you can replace “bash” with “zsh” (Z shell), “tcsh” (tee shell), and so on, based on your preference.
You can add available objects from the TransferPrescript parameter or add your own commands to the PreTransferScript.sh and PostTransfer.sh scripts to customize them.
Only PreTransferScript and PostTransferScript receive parameters. The snapshot and export scripts do not.
This section describes the scripts that administrators can use at designated occurrences in Rapid Recovery for Windows and Linux. It includes the following topics:
Rapid Recovery provides the ability to run Bourne shell, Bash, and other shell scripts on a protected Linux machine before and after a transfer. The following scripts are supported for Linux machines protected with the Rapid Recovery Agent software.
|
|
NOTE: If a script is not executable, the transfer job fails. |
To use these scripts, ensure that they reside in the /opt/apprecovery/scripts/ directory.
For context, the following diagram shows the difference in timing for running pre- and post-transfer and snapshot scripts.
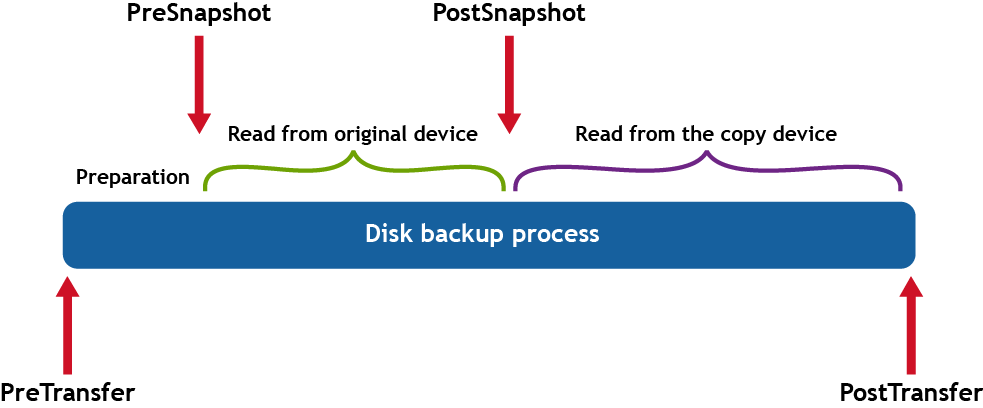
The following parameters are supported on Linux for transfer scripts. For more information, see Sample shell scripts.
The following parameters are supported on Linux for post transfer scripts.
You can test the scripts you want to run by using the editor for the script (.sh) files.
|
|
NOTE: If the pre- or post- script fails, the job also fails. Information about the job is available in the /var/log/apprecovery/apprecovery.log file. Successful scripts return the exit code 0. |
The parameters for shell scripting in Rapid Recovery are described in the following tables.
The following table presents the available objects for the TransferPrescript parameter.
| Method | Description |
|---|---|
| public VolumeNameCollection VolumeNames (get; set; ) | Gets or sets the collection of volume names for transfer.
VolumeNames is a data structure that contains the following data:
|
| public ShadowCopyType ShadowCopyType { get; set; } | Gets or sets the type of copying for transfer. ShadowCopyType is an enumeration with values. The available values are:
|
| public string Key { get; set; } | The Key method generates a pseudorandom (but not cryptographically secure) key, which can be used as a one-time password to authenticate transfer requests. |
| public bool ForceBaseImage { get; set; } | Gets or sets the value indicating whether the transfer was a forced base image capture. |
| public bool IsLogTruncation { get; set; } | Gets or sets the value indicating whether logging is being truncated. |
| public uint LatestEpochSeenByCore { get; set; } | Gets or sets latest epoch value.
The LatestEpochSeenByCore method is the ordinal number of the most recent snapshot taken by the Core. This is the 'epoch number' assigned by the filter driver to this particular snapshot at the moment it was taken with VSS. |
The following table presents the available objects for the TransferPostscript parameter.
| Method | Description |
|---|---|
| public VolumeNameCollection VolumeNames (get; set; ) | Gets or sets the collection of volume names for transfer.
VolumeNames is a data structure that contains the following data:
|
| public ShadowCopyType ShadowCopyType { get; set; } | Gets or sets the type of copying for transfer.ShadowCopyType is an enumeration with values. The available values are:
|
| public string Key { get; set; } | The Key method generates a pseudorandom (but not cryptographically secure) key, which can be used as a one-time password to authenticate transfer requests. |
| public bool ForceBaseImage { get; set; } | Gets or sets the value indicating whether the transfer was a forced base image capture. |
| public bool IsLogTruncation { get; set; } | Gets or sets the value indicating whether logging is being truncated. |
| public uint LatestEpochSeenByCore { get; set; } | Gets or sets latest epoch value.
The LatestEpochSeenByCore method is the ordinal number of the most recent snapshot taken by the Core. This is the 'epoch number' assigned by the filter driver to this particular snapshot at the moment it was taken with VSS. |
This section describes the sample shell scripts available for administrative users to run on protected machines.
|
|
Caution: The sample scripts provided in this document function as they exist when run by qualified administrators. Take precautions when modifying functioning scripts to retain working versions. Any modifications to the script samples included here, or any scripts you create, are considered customization, which is not typically covered by Quest Support. |
|
|
NOTE: Protected machines use the 'exec' shell command to launch the script. You can indicate which interpreter should run the script by defining that information in the first line of the script. If you do not specify the interpreter, the default shell interprets the script. If you choose something other than the default shell, you must ensure that the specified interpreter is available on all protected machines. All sample shell scripts in this document are tested and run successfully as Bourne shell or Bash scripts. |
The sample scripts for protected machines include: