Migrating Agents
|
1 |
Open the migration wizard by navigating to Dashboards > Databases > Support Dashboard > Databases Technical Support > Database Agents Migration > SQL Server. |
|
6 |
Click Next to migrate the agents. |
|
7 |
When migration has completed, click Finish to exit the Wizard. |
About Monitoring Extensions
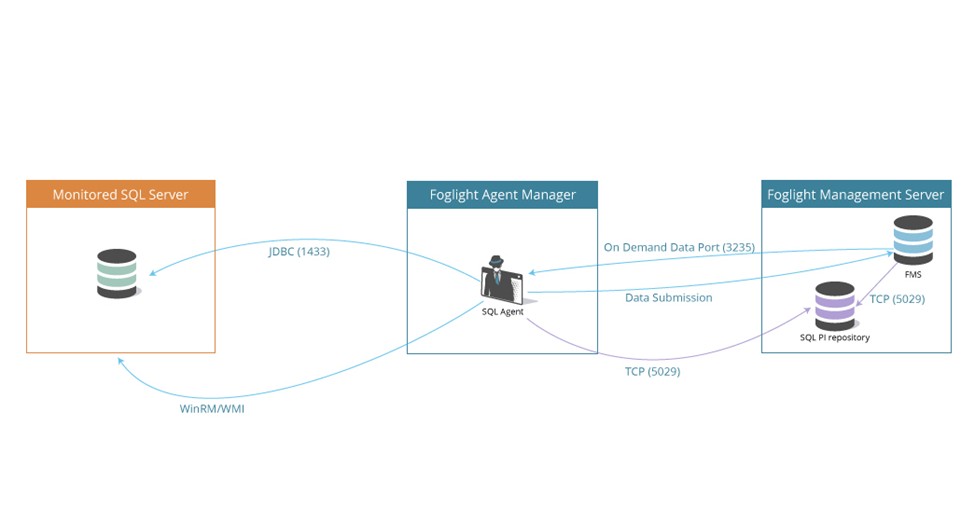
The communication architecture of Foglight for SQL Server is presented below.
Installing and Monitoring a Single SQL Server Instance
Foglight for SQL Server provides a graphic, intuitive method for creating and configuring multiple agents, which can be used instead of Foglight’s default method for creating agents and editing their properties using the Agent Administration dashboard (see About the Foglight for SQL Server Agent in the Foglight for SQL Server Reference Guide). Foglight for SQL Server allows running a wizard that provides a common entry point for adding and discovering all database instances within a user-specified range, and then configuring these instances for monitoring.
|
1 |
On the navigation panel, click Homes > Databases. |
|
2 |
|
a |
Click the Agent Manager Host link located in the bottom left corner of the dialog box. |
|
• |
Port — Optional. This field can be left empty, unless the TCP/IP connection port is not the default port: 1443. |
|
• |
Essential — Store and display only critical or fatal alarms. |
|
• |
Normal — Store and display most alarms — essential and best practices; only critical and fatal statistical alarms. |
|
• |
Tuning — Store and display all SQL Server alarms sent to Foglight. |
|
• |
Performance — Store and display only availability and SQL PI related alarms. |
|
7 |
Optional — In the Monitoring Extension pane, click the Click for Licensing Information link under SQL PI. You are prompted to contact Quest Sales for an add-on license to enable SQL Performance Investigator (PI). |
|
8 |
|
9 |
Optional — In the Monitoring Extensions pane, click Collect VM statistics. |
|
10 |
Click Monitor. |
|
11 |
When the installation completes successfully, the Monitoring Initialized Successfully dialog box appears. Click Add another Database or Finish to exit. |
Discovering Multiple Instances to Monitor
|
1 |
|
2 |
Click the Use this option to discover multiple SQL-Server instances link. The Select an Agent Manager dialog box appears. |
|
3 |
Choose an Agent Manager host, click Validate to validate the Agent Manager system resources, and then click Next. |
|
4 |
Click Add instances and select one of the following methods for adding instances: |
|
5 |
|
7 |
Click Set credentials to provide the instances' log in credentials and monitoring configuration. |
|
8 |
Follow the steps described in Installing and Monitoring a Single SQL Server Instance , starting with Step 5 to enter the monitoring credentials and enable the monitoring extensions for this instance. |
|
NOTE: To use stored credentials when enabling the Operating System monitoring extension, click the Operating System > Select from stored credentials link to open the Stored Credentials dialog box. Here you can review the log in credentials and authentication methods used for logging in to Foglight. Foglight stores encrypted credentials in lockboxes, which may be password-protected for added security. Database agents store all user log in credentials in a default lockbox called DB-Agent Lockbox. If credentials have already been entered in another lockbox, use the Lockbox list to select from that lockbox. |
|
9 |
Click Monitor |
|
• |
If the message is Insufficient database privileges, this issue can be resolved using the Insufficient Database Privileges dialog box that appears. For details, go to Step 10. |
|
• |
For all other messages, the Database Connection Failed dialog box appears. For details, go to Step 11. |
|
10 |
Click the text Insufficient Database Privileges. |
|
a |
Click Show details to view the error’s description. |
|
b |
Click Set credentials to display the dialog box used for entering the credentials, and enter the required changes. |