Directory Sync
Environments
Prior to any migration of an Active Directory computer there are a few Directory Sync requirements to inventory your devices (computers). The first of which is your local on-premises environments or endpoints. To gain access to your devices from your on-premises Active Directory you must create and securely connect your Environments.
How do I add an Environment?
For complete details on how to add an environment, click here.
Workflows
The next required configuration for Directory Sync is to create a workflow that will inventory (read) your local on-premises Active Directory computers.
Directory Sync Agents
The final component required is to deploy at least one (1) Directory Sync agents that will be used to secure communicate and execute jobs against your Local Active Directory such a read or write.
How do I install a Directory Sync Agent?
For complete details on how to install an agent, click here.
Networking
Outbound Internet Access
By default, each computer being migrated will require outbound access to the public Internet to securely communicate with the On Demand Migration Active Directory services.
Important Tip: If your organization requires computers communicate externally using a web proxy see our .
Application Ports
Each computer being migrated will require the Active Directory device agent and this agent will communicate to the On Demand Migration Active Directory services, outbound over ports:
- 80
- 443
- 3030
Domain Controller Ports
Active Directory migrations also require a variety of Microsoft defined ports for communication between domain controllers. For a complete list of required ports, click here.
Important Tip: For complete port information, review the Service overview and network port requirements for Windows documentation from Microsoft Support.
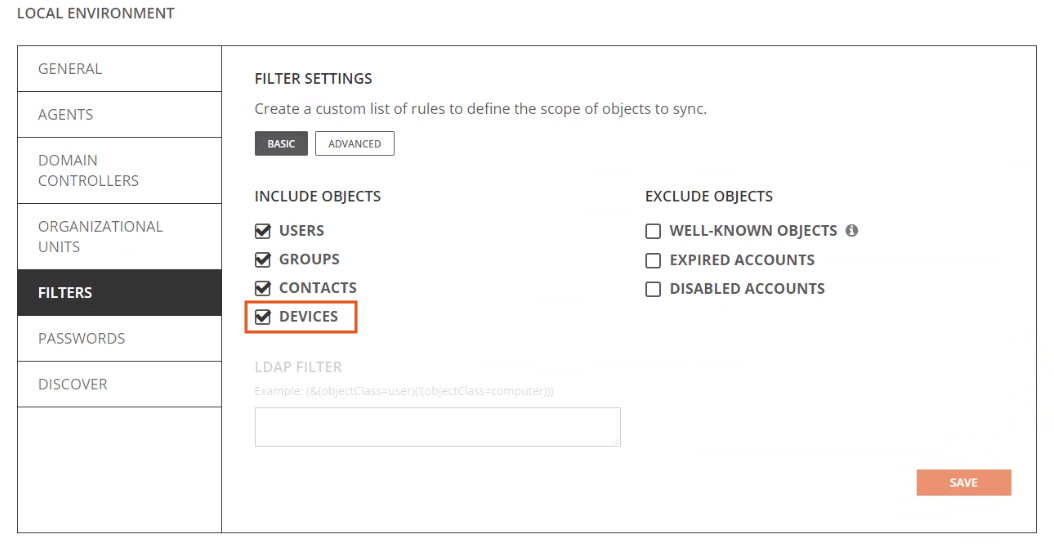
Devices
The following is required for any Active Directory Computer(s) (devices) that will be migrated.
Device Agents
Each Active Directory Computer that will be migrated must have an agent installed on the workstation to orchestrate local jobs that must occur to prepare and execute the workstation’s domain move.
Operating Systems
All computers or servers being migrated to the new domain must run one of the following operating systems:
- Windows 10
- Windows 11
- Windows Server 2016
- Windows Server 2019
- Windows Server 2022
- Windows Server 2025
|
|
NOTE: Entra ID Device Join is only supported for Windows 10 and 11. |
PowerShell
- All client operating systems must have at least PowerShell 2.0 installed.
.NET Framework
- All Devices must have .NET Framework 4.7.2 or newer installed. This will appear as ".NET 4.7.2 Extended" in the add/remove programs list.
- If not present, an appropriate version of .NET Framework will be installed during agent installation if an internet connection is available.
Remote Devices
To successfully migrate a remote employee’s remote device using the Offline Domain Join (ODJ) feature the Cache Credential action must be run to collect the user’s target credentials, so later you may cutover the device, while it is disconnected from the network.
The following is required:
Cached Credentials Action
- One-way external trust must be configured from the source domain to the target domain when the Cache Credential activity is processed
For more information about AD Trusts, check out this MS Press article about configuring trusts.
Network
• Network connectivity to both the source and target environments (Active Directory Domain Controllers) when the Cache Credential activity is processed
Important Tip: Offline domain join files must be created prior to running the Offline Domain Join process. A full explanation of Microsoft’s Djoin.exe utility and how to create these files can be found here.
How do I set up Offline Domain Join (ODJ)?
For complete details on how to set up ODJ, click here.
Web Proxy
Some organizations may require all computers communicating externally direct their traffic through a web proxy to centralize communications. Active Directory agents can be configured to use a web proxy for communication to the On Demand Migration Active Directory cloud services.
Proxy Server
- At least one (1) standard web proxy that supports http/TCP traffic.
Proxy Address
- The associated web proxy URL must be defined during configuration of the device agent.
Security
- If accessing the web proxy requires an additional username and password this will be required during configuration of the device agent.
Ports
All agents configured to use a web proxy will utilize the following outbound TCP ports:
- 80
- 443
|
|
NOTE: Agents configured to use a web proxy will not require UDP port 3030. For more information, see the Web Proxy Configuration under Architecture. |
Important Tip: Additional bandwidth overhead may occur when a web proxy is utilized to centralize all traffic.
Repositories
The following four Device Actions, when used, will require a defined storage share accessible from the device being migrated:
- Upload Logs
- Device Download
- Offline Domain Join
- Microsoft Entra ID Cutover
How do I configure repositories?
For complete details on how to configure repositories, click here.