Virtual Machine Automation
|
3 |
|
4 |
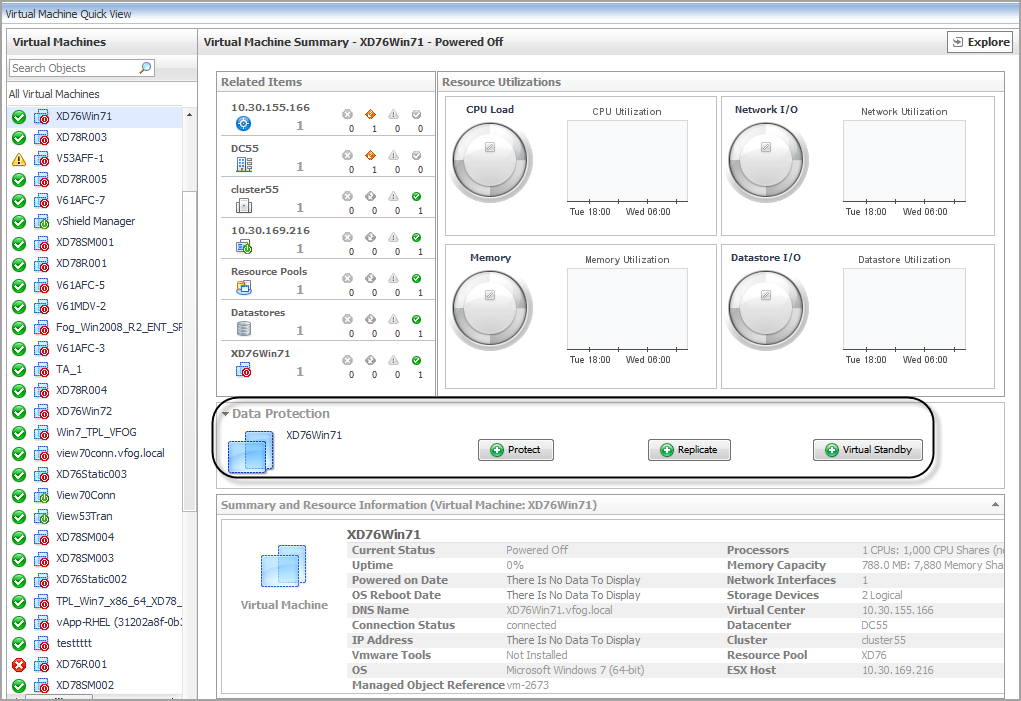
Select a Virtual Machine from the Monitoring > Virtual Machine Quick View > Virtual Machines tree view. |
The VROOM Virtual Machine Automation includes the following three options:
|
• |
|
• |
|
• |
Automation of VM Protection
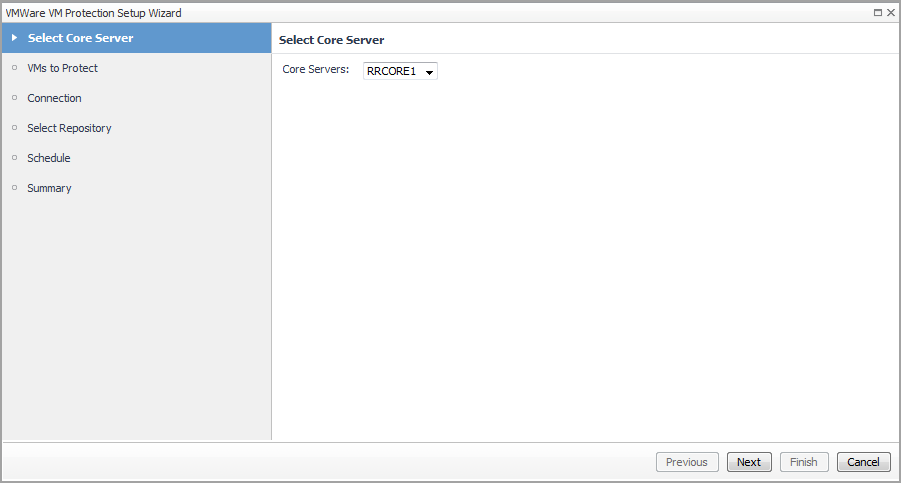
The VMware VM Protection Setup Wizard guides you through the procedure for identifying virtual machines that you want to protect. This wizard also enables you to customize the schedule for performing the protection automation.
|
3 |
|
4 |
Select a Virtual Machine that you want to protect from the Monitoring > Virtual Machine Quick View > Virtual Machines tree view. |
|
5 |
|
6 |
|
7 |
In the VMs to Protect step, select VMs from the left vCenter table, click >> to move selected VMs to the right table, and then click Next. |
|
8 |
|
9 |
In the Select Repository step, select a repository from the Core Repositories drop-down list, and then click Next. |
|
10 |
|
• |
Default protection: The automation will be performed hourly for all volumes. |
|
• |
Periods: The automation will be performed on specified weekdays or weekends. |
|
• |
Daily protection time: The automation will be performed on a daily basis. |
|
11 |
Automation of VM Replication
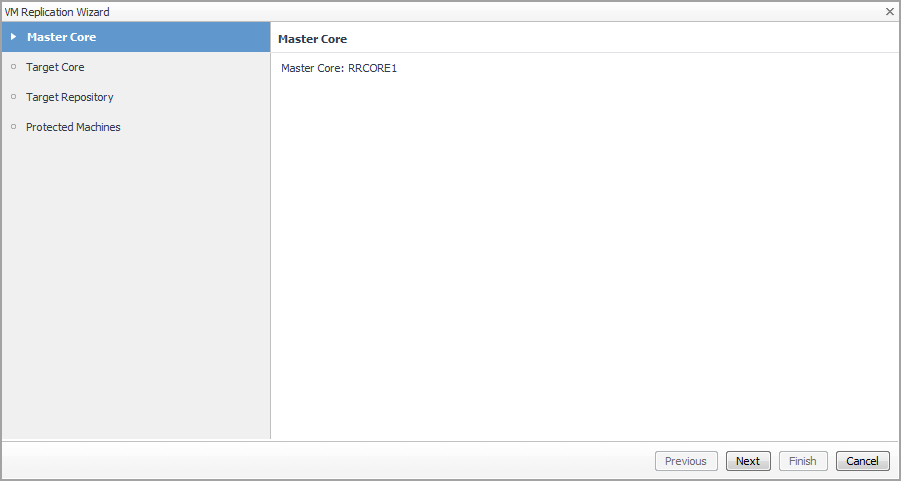
The replicate is the process of copying recovery points from one Rapid Recovery Core and transmitting them to another Rapid Recovery Core for disaster recovery purposes. The process requires a paired source-target relationship between two or more cores. The VM Replication Wizard guides you through the procedure for identifying virtual machines that you want to replicate.
|
3 |
|
4 |
Select a Virtual Machine that you want to protect from the Monitoring > Virtual Machine Quick View > Virtual Machines tree view. |
|
5 |
|
6 |
|
7 |
|
NOTE: If there is no available target Core, go to Rapid Recovery Console > Replication and add a target Core in the selected Master Core manually. |
|
8 |
|
9 |
In the Protected Machines step, select other virtual machines that you want to replicated as needed, and then click Finish. |
Automation of VM Standby
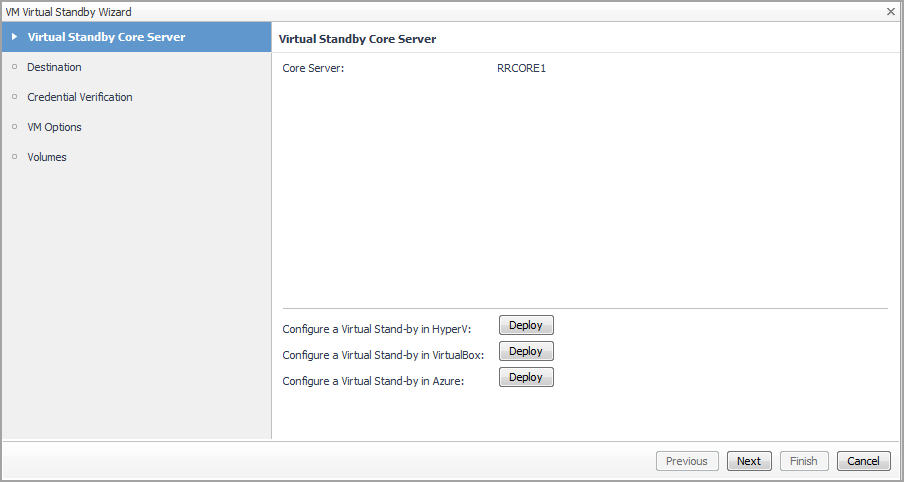
The VM Virtual Standby Wizard guides you through the procedure for performing a virtual standby of continual export of recovery point data from a protected machine to a virtual machine in any supported VM format.
|
3 |
|
4 |
Select a Virtual Machine that you want to protect from the Monitoring > Virtual Machine Quick View > Virtual Machines tree view. |
|
5 |
|
6 |
|
7 |
|
8 |
In the Credential Verification step, select new credential or an existing credential, and then click Next. |
|
9 |
|
10 |
|
11 |