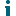The top of a Tier Zero Object Investigation page identifies the object being investigated, along with the following information:
-
the Severity of the Finding
-
the Finding Type (Tier Zero)
-
the Certification Status (Certified or Not Certified)
-
the Finding Status (Active or Inactive)
-
Last Updated (that is, the last time the Finding was detected)
NOTE: Last Updated displays a relative time. However, if you hover over the clock icon you can see an exact date and time. This field displays the signed-in user's local date and time.
-
options to certify the Tier Zero object, dismiss the Finding, and view history of the Finding.
What Happened?
This section indicates why a Finding was raised for the Tier Zero object, as well why the object is considered Tier Zero and the number of other Tier Zero objects that it impacts and is impacted by.
|
|
NOTE: If BloodHound Enterprise is the Tier Zero provider, it can return a maximum of 10,00 related objects for each category. |
The What Happened? section for Tier Zero also includes a series of links to help you complete your investigation, as described in the following table.
| Link | Description | ||
|---|---|---|---|
| View Details |
The properties of the Tier Zero object, including whether it was added by the system (Security Guardian or BloodHound Enterprise) or by a user, identifiers used for the object within Active Directory, the date the object was added and the date its information was last updated.
| ||
|
View Relationships
|
If BloodHound Enterprise is configured, this link enables you to log into BloodHound (if you have at least Read permissions) and view attack paths between the object being investigated and other AD objects.
| ||
| View Recent Activity | This link opens the Quick Search page in On Demand Audit, which lists event data for the selected object. | ||
| Escalate this Finding | |||
| Copy | This link allows you to copy the text of the Finding to the clipboard so that you can share it with others. | ||
| Send email | This link allows you to prepare and send an escalation email to recipients with whom you want to share the Finding. | ||
How Do I fix this?
This section provides recommendations for investigation and remediation.
|
|
NOTE: If BloodHound Enterprise is the Tier Zero provider, the View Relationships link to BloodHound Enterprise is also provided in this section. |