Introduction to Delegation and Policy Control
Quest Nova provides granular Delegation and Policy Control for Microsoft 365, enabling you to assign pre-defined roles and responsibilities to specific users, such as help desk operators, country-level administrators, or end-users. Nova also includes policy-based automation for authorization, service configuration and license assignment.
This guide is to help you get started with Delegation and Policy Control as an administrator. This includes:
·how to set up service accounts
·how to create Virtual Organizational Units (vOUs)
·how to create authorization, configuration and license policies, including helpful use cases
·overviews of the Manage and Manage Administration tabs
For a more in-depth guide on using Quest Nova, please click here to view the Nova technical documents. In the Quest Nova User Guide, you will see more information on:
·Custom PowerShell execution and delegation
·additional policy examples
·more actions for delegated administrators
|
|
CAUTION: DPC gives the ability to control license management, device management and other sensitive actions, so select your administrators and delegated administrators with care. |
It is recommended that you undertake Nova training before using the application to get a better understanding of the platform. To sign up to Nova learning, click here.
To access Delegation and Policy Control, you will need a subscription to Nova that includes support for management, and support will provision your organization during the on-boarding process.
Service Accounts for Nova DPC
Nova Delegation and Policy Control (DPC) uses service accounts to manage tenants and to perform actions on behalf of delegated administrators. Service accounts are also used to pull the data from the account to perform actions upon in DPC.
You can review and manage these accounts on the Manage Administration, then the Service Accounts page.
On the Service accounts tab, you can:
·Refresh: Update the list of service accounts for the tenant.
·Add: Add a service account to the tenant. Instructions on how to do that are below.
·Edit: Change the service account. You will need the account's credentials to access.
·Delete: Remove the service account from the tenant.
·Authorize Management: Learn more about this below.
There are two steps to configure and setup Nova DPC for the tenant. They are:
1.Allowing permissions for Nova DPC
Nova DPC requires an administrator to allow Microsoft permissions to retrieve data for the tenant. To do this:
1.On the Manage administration tab, click Service accounts.
2.Click Authorize Management.
3.Sign in using an administrative account.
4.Review the list of permissions. Once you are happy with this, click Accept. This will then take you back to Nova.
2.Adding a service account to the tenant
You then need to add the service account to pull the data from to perform actions on. To do this:
1.On the Manage administration tab, click Service accounts.
2.Select the tenant to add the service account to.
3.Enter the global administrative account's email to the Admin username box.
4.Enter the password of the global administrator.
5.Click Save. The service account will then be provisioned.
Pre-requisites for service accounts
·The service account needs to be a global administrator in the tenant. The global administrator account will also need to be mail enabled to receive an email invitation. A global administrator account is required as:
i.this allows for delegated actions to be completed by Nova users, without needing to grant these users full administrator permissions.
ii.an account with global administrator permissions are able to perform actions that may not be available via Microsoft Graph.
·Single Sign On (SSO) is the preferred method of signing in. This will need to be authorized in each tenant.
·Multi-factor authentication should not be enabled on the account (it is used to programmatically run PowerShell sessions, and therefore cannot be multi-factor authentication enabled). Application passwords are not supported for the service account.
·It must be free from any policies that would restrict its access in the tenant (for example, a Conditional Access Policy that limits basic authentication attempts from internal IP addresses only).
·It should be dedicated for use with Nova DPC.
|
|
NOTE: If the password of the service account is changed, it must also be changed in Nova DPC. |
Permissions
A list of the APIs/permissions required can be found here.
Roles in Nova DPC
Users of the Nova application can be assigned one or more roles. Each role provides functionality in the Nova application itself. Roles can be combined. The following is a list of the roles, and what they give access to:
Account Administrator
This gives access to be able to create and manage policies in Delegation and Policy Control. In addition, audit logs can be viewed to see how the policies have been used by delegated administrators. There are several other administrative functions which are shown in this screenshot:
Auth Policy Admin
This gives users the ability just to manage authorization policies within Nova. The option to get into Authorization Policies will be enabled in the Manage Administration menu.
Auth Policy administrators also have the ability to delegate certain subsets of custom PowerShell commands to selected users, which can be organized in an organization unit hierarchy. It is advised that Auth Policy Admins create dedicated organizational units exclusively for PowerShell scripts.
Autopilot Classic
This role is most appropriate to assign to a delegated administrator. This gives access to be able to perform allowed actions against users, mailboxes, groups, contacts and Microsoft Teams. What the user will be able to do is governed by the policies which are applied to them and were configured by someone with at least the Account Administrator role.
Config Policy Admin
This gives users the ability just to manage configuration policies within Nova. The option to get into Configuration Policies will be enabled in the Manage Administration menu.
IT Administrators
This gives a user the ability to use Nova, but restricts them from changing the configuration or security of Nova itself.
License Admin
This gives people the ability to create and maintain License Policies. The option will be available on the Manage Administration menu.
Organizational Unit Admin
This gives users the ability to maintain virtual organizational units. The Tenants option will be available on the Manage Administration menu.
System Administrator
This role gives access to the Tenant Management System, and does not give any direct access to the Nova application (unless it is combined with other roles).
Examples of combining roles
If a user needs to be able to create authorization policies, and perform actions on customer tenants (such as password resets, maintaining groups, adding Microsoft Teams etc.), then they should be assigned these roles:
·Account Administrator
·Autopilot Classic
If someone needs to be able to access reporting data, and perform actions on customer tenants (such as password resets, maintaining groups, adding Microsoft Teams, and so on) then they should be assigned these roles:
·Autopilot Classic
·Radar Classic
Granting Account Administrator
The following should be considered when assigning roles
·The Account Administrator roles does not work on it is own. It needs to be combined with the Autopilot Classic role.
Virtual Organizational Units
A virtual organizational unit (vOU) is a manually built dynamic list of users tailored to group users by a specific attribute. For example, vOUs can be built to group users by their location, department, company or another attribute. These help administrators to group users to assign authorization, configuration and license policies to them.
If you are familiar with on-premises Microsoft Entra ID, then you will already be familiar with organizational units. The problem is that Microsoft Entra ID and Microsoft 365 do not have this concept. These users are stored in a flat list, which can make working with multiple geographies and multiple departments much more difficult. Nova has modified this premise, redefined as 'virtual organizational units'. You can create a hierarchy of these just like you would in an on premises Microsoft Entra ID environment.
|
|
NOTE: These organizational units are exclusive to Nova, and are not pulled into Microsoft Entra ID. |
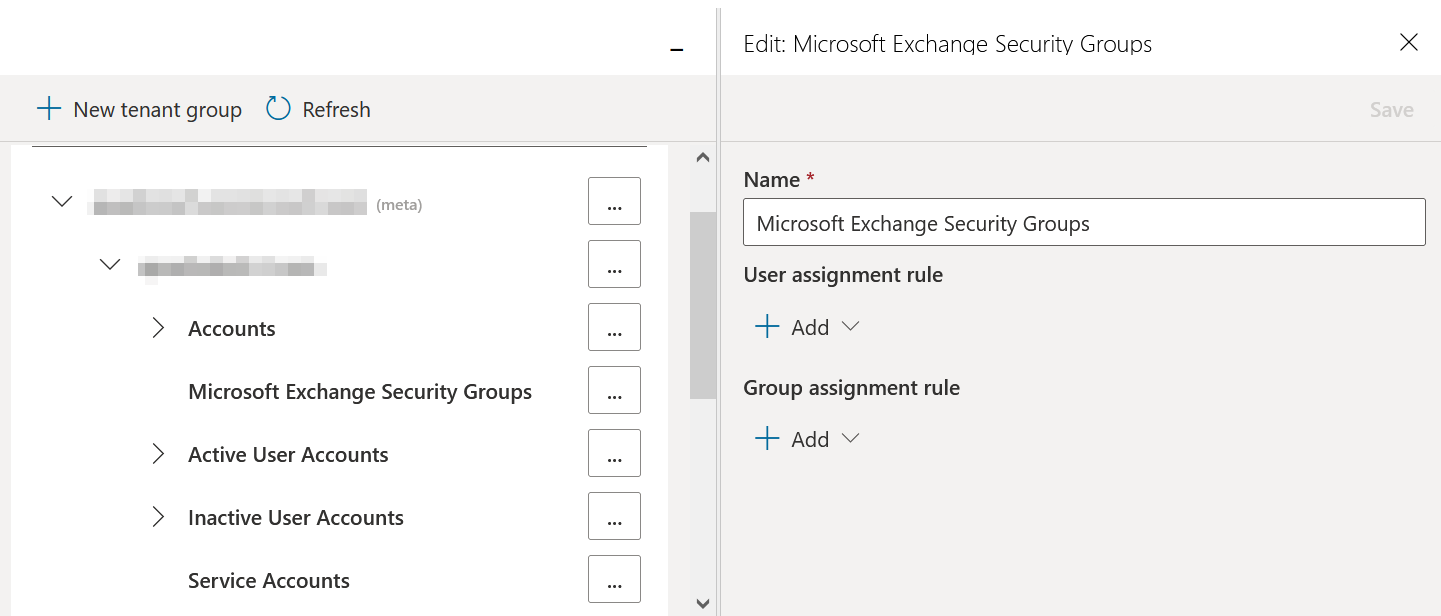
Creating a new Virtual Organizational Unit
Follow the steps below to set up a virtual organizational unit.
1.In the left menu, select Manage Administration, then Tenants.
2.Then, either:
oClick the ellipsis button (...) next to a tenant and select New.
oOr, create a virtual organizational unit that's nested under an existing one by expanding the tenant, finding the organizational unit you will create one under, clicking the ellipsis button (...) next to it, and selecting New.
3.Enter a name for the new organizational unit and click Save.
Adding a User or Group to a Virtual Organizational Unit
Complete the steps below to add a user or group to a virtual organizational unit.
1.In the left menu, select Manage Administration, then Tenants.
2.Expand organizational units until you find the one to which you will add a new user or group.
3.Click the desired organizational unit's ellipses (...) button and:
a.if you would like to add one or multiple users, click Users.
b.if you would like to add one or multiple groups, click Groups.
4.Select the checkbox next to the desired user or group and click the Move button.
5.Expand the tree until you find the desired target organizational unit, and then select it and click Save.
Viewing Users and Groups Assigned to a Virtual Organizational Unit
Follow the steps below to see a list of users and groups currently assigned to a virtual organizational unit.
1.In the left menu, select Manage Administration, then Tenants.
2.Expand the organizational units until you find the one whose users you want to see.
3.Click the desired organizational unit is ellipses button (...) and select Users & Groups to see a list of users and groups that were added to the group within Nova.
|
|
NOTE: You can see other objects as well, such as mailboxes and contacts. |
User Assignment Rule
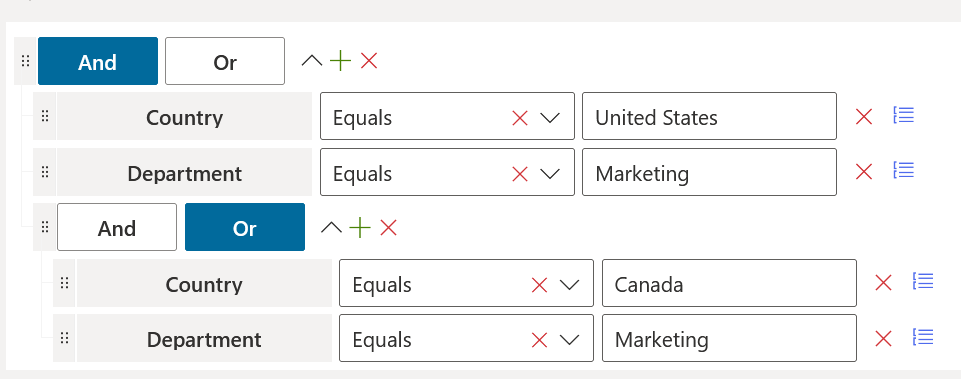
The user assignment rule automatically adds users to a vOU based on one or more properties already assigned to those users. For example, you can set up a policy that adds United Kingdom users operating in Sales. Below are the steps to do that:
1.Go to your vOU and click on the ellipses button, then click Edit.
2.Under User assignment rule, click Add, then Group.
3.Click the + icon, then Property.
4.Click Choose property, then from the drop down menu, click Country.
5.For Choose operator, click Equals, then type United Kingdom into the text field.
6.Click the + icon again, and select Property.
7.Click Choose property, then from the drop down menu, click Department.
8.For Choose operator, select Equals, then type Sales in the text field.
9.Click Save.
Users with these attributes already assigned will now be automatically assigned to this vOU.
Another example is creating a vOU for the marketing department assigned in the United States or Canada. Applying the steps above in this scenario, the rule should look like the image below:
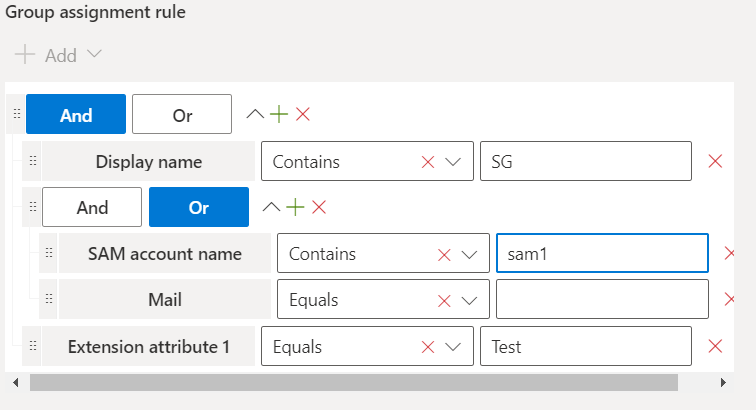
Group Assignment Rule
Administrators also have the ability to automatically assign group management delegation based on properties of the group or group owner. This allows you to delegate responsibilities to localized IT support without granting them excessive access to your tenant(s).
To automate group management delegation:
1.From the Nova dashboard, go to Manage Administration, then Tenants.
2.Click on the ellipsis next to your desired tenant, and click New.
3.Click Add under Group Assignment Rule.
From here, provide your required group and/or properties, then save your organizational unit with this group assignment rule. View the image below for an example.
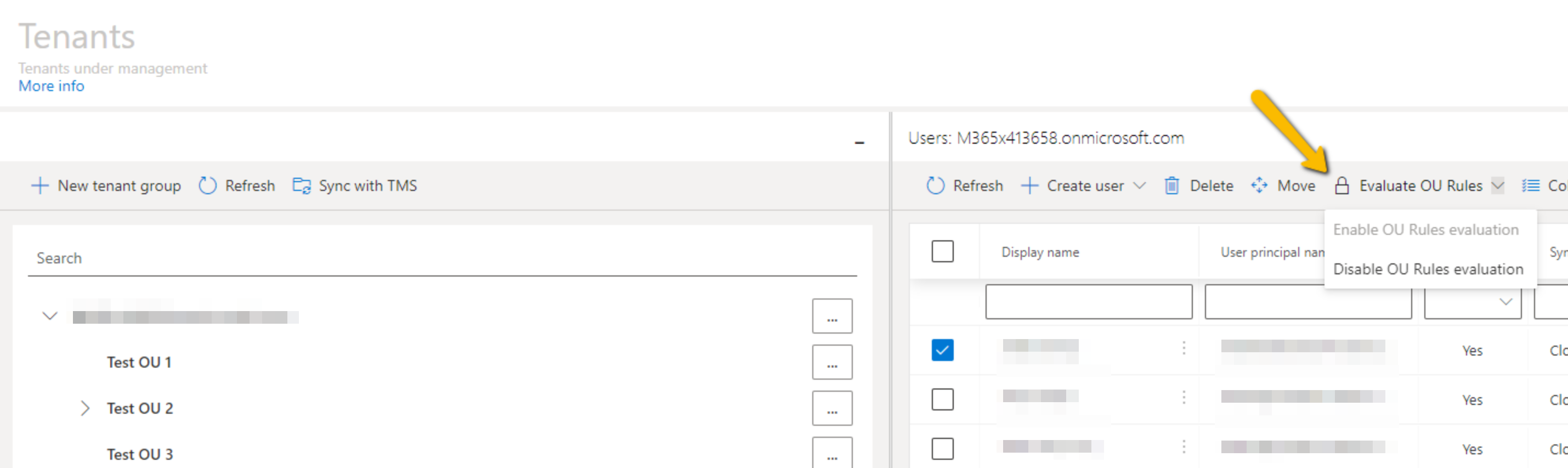
You can also enable or disable OU rules for each user by selecting the user from your chosen tenant, then selecting Evaluate OU Rules, then either enabling or disabling these rules.