Follow these steps to create test objects in the source environment to validate the Password Sync workflow.
- Setup 2 Users in the source local environment and ensure it is part of the OU filter setup for the Local Environment.
- DisplayName: Lab1PWD1
- DisplayName: Lab1PWD2
Description: Matched User
- Setup a User in the target local environment it is part of the OU filter setup for the Local Environment.
- DisplayName: Lab1PWD2
- Setup a workstation in the target Active Directory environment for Password validation test.
Follow the below steps to perform Real Time Password Sync workflow and validation.
- Select the workflow configured and click on RUN.
- Allow the workflow execution to complete.
- Validate Lab1PWD1 from source local Active Directory will be created in target.
- Validate Lab1PWD2 from source local Active Directory will match to the existing Lab1PWD2 user in target. Source user’s description value will be added to the target user.
- Select the workflow configured and click on Run again. This is needed to read the newly created object into system, this will allow Directory Sync to update the Password for the user object.
- Make Password changes to both Lab1PWD1 and Lab1PWD2 users.
- Wait for about 1-2 minutes, navigate to the Environment page and select the source environment. Click on PASSWORD LOGS button and export the logs with default setting.
- Once the log is downloaded, open the log file, and confirm Directory Sync has read the Password changes from source environment. Below are the sample loggings:
33709,1502,Lab1-Local,"Read: Detected password change for object CN=Lab1PWD1,OU=Lab1Users,OU=Lab1CDS,DC=lab1,DC=leagueteam,DC=local",,9/29/2023 3:27:01 PM
33717,1502,Lab1-Local,"Read: Detected password change for object CN=Lab1PWD2,OU=Lab1Users,OU=Lab1CDS,DC=lab1,DC=leagueteam,DC=local",,9/29/2023 3:29:03 PM
- Select the target environment and click on PASSWORD LOGS button and export the log with default setting.
- Once the log is downloaded, open the log file and confirm Directory Sync has written the Password changes to target environment. Below are the sample loggings:
33711,1503,Lab2-Local,"Write: Using global catalog server from configured DCs list: Lab2-DC.Lab2.LeagueTeam.local, Domain=lab2.leagueteam.local",,9/29/2023 3:28:13 PM
33712,1503,Lab2-Local,Write: Connecting to Domain Controller using port: 389,,9/29/2023 3:28:13 PM
33713,1503,Lab2-Local,Write: Applying changeset 0ee87616-40d4-4640-a7d6-0cfcdaeff5a0,,9/29/2023 3:28:13 PM
33714,1503,Lab2-Local,"Write: LDAP Search DC=lab2,DC=leagueteam,DC=local
Server: Lab2-DC.Lab2.LeagueTeam.local (10.1.10.30) User: administrator@lab2.leagueteam.local
(distinguishedName=<GUID=c5afc6ec-40d6-4a1e-9226-73b00209dda6>)",,9/29/2023 3:28:14 PM
33715,1503,Lab2-Local,"Write: LDAP Search DC=lab2,DC=leagueteam,DC=local
Server: Lab2-DC.Lab2.LeagueTeam.local (10.1.10.30) User: administrator@lab2.leagueteam.local
(distinguishedName=<GUID=c5afc6ec-40d6-4a1e-9226-73b00209dda6>)",,9/29/2023 3:28:14 PM
33716,1503,Lab2-Local,Write: Finished applying changeset 0ee87616-40d4-4640-a7d6-0cfcdaeff5a0,,9/29/2023 3:28:14 PM
- Use the target workstation and log into the machine with target Lab1PWD1 user using the most recent password from the source environment. Verify the target user can be logged in and target environment.
- Use the target workstation and log into the machine with target Lab1PWD2 user using the most recent password from the source environment. Verify the target user can be logged in and target environment.
This list contains the common errors that may occur during Password Synchronization and troubleshooting steps we can use to address these errors.
Do I need to run my workflow to have my password changes synced?
Although Password Syncs does not require users to run the workflow if the source and target users are correctly matched by Directory Sync, it is necessary to run the workflow at least once to allow existing target users to be matched with the source users based on the matching rules you have defined. For users created by Directory Sync, running the workflow again will be required to have the new target user matched to the source user. Once users are correctly matched, Directory Sync will monitor the password changes and synced to the target without the need of running the workflow.
Why does Directory Sync generate password read log in the target Active Directory when I have Password Sync enabled from Source to Target?
Directory Sync needs to read the target user password hash into system so it can compare with the source user password hash to determine if it was changed and synced.
I see BTPass folder being created under ADMIN$, does the new Modern Password Sync utilize BTPass folder?
BTPass folder is only required when using Legacy Password Sync, the modern Password Sync utilizes the Password Filter Plugin installed on the domain controller to synchronize the password.
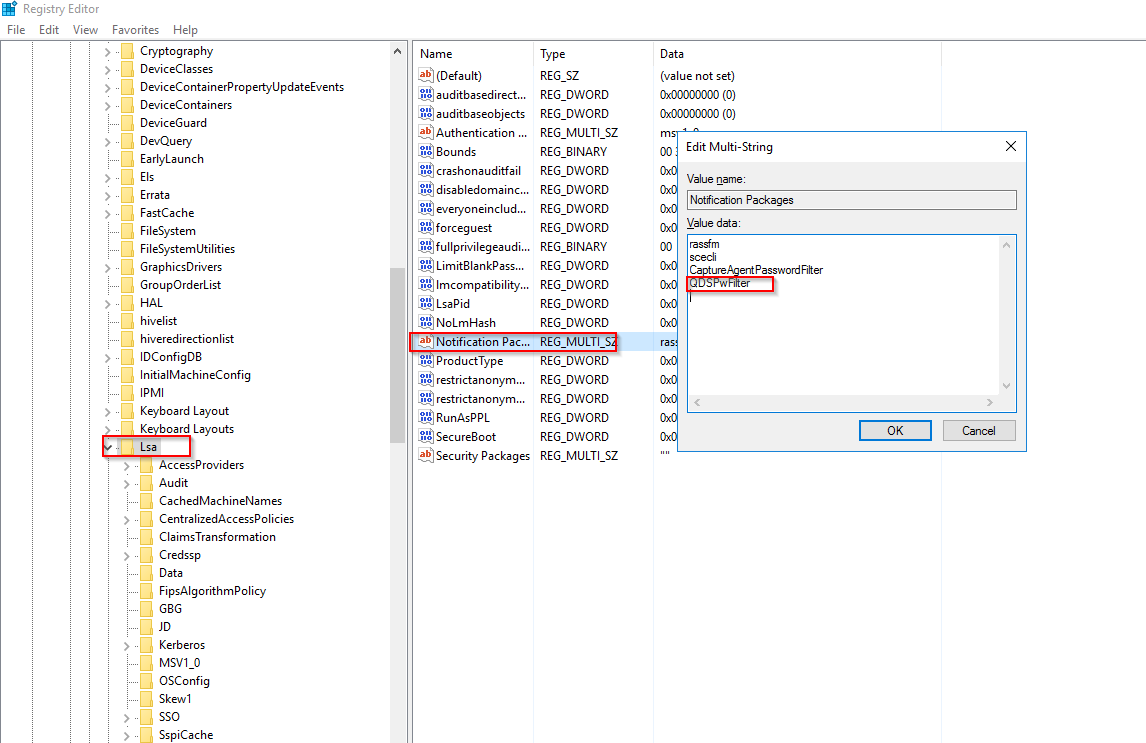
How can I validate if the Password Filter Plugin is running on my Domain Controller?
Password Filter will run automatically when the Domain Controller starts, we can validate the auto-startup setting via “HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa” under “Notification Packages” key. We should see “QDSPwFilter” registered. (See below sample screenshot)
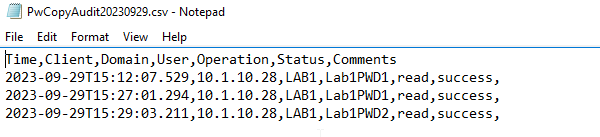
Does the Password Sync generate audit logs when reading and writing the password hash?
Password Audit logs are stored under “C:\ProgramData\Quest\PwCopy” on the Domain Controller. Below is a sample screenshot of the audit log.
Can I set up a workflow that only performs password sync for existing users and not sync any other attributes?
Yes, you may set up a workflow template and only include the ‘unicodePwd’ attribute in the template. Alternately, you can set up a workflow that only performs Read and Match operation. Once a matching record is created for the source and target user, Directory Sync will sync across passwords when changes are detected for the source users.
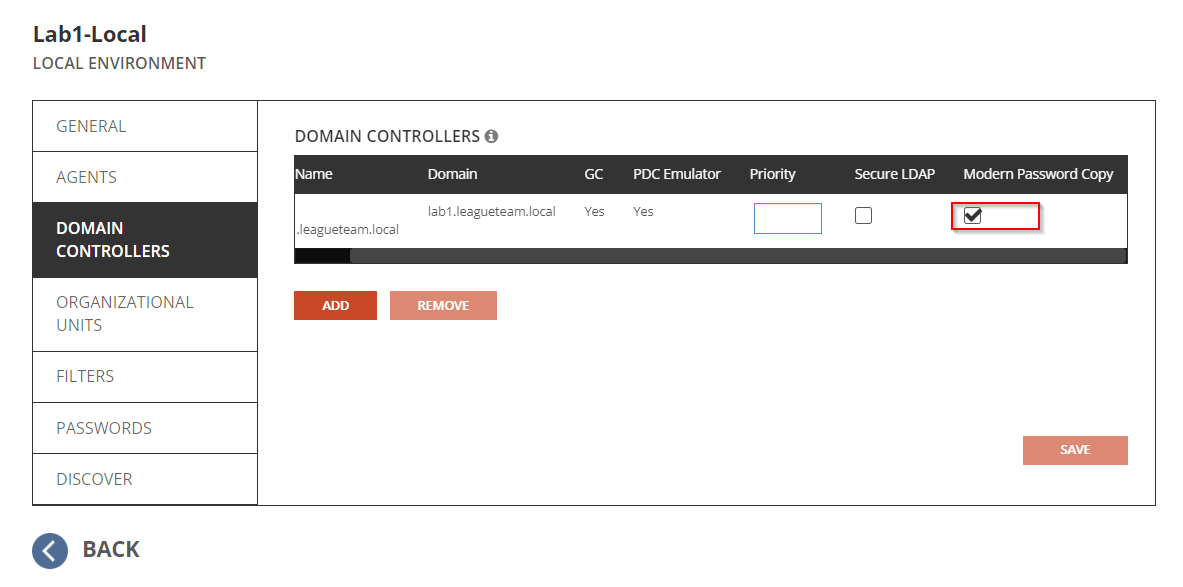
How can I tell if I have Modern Password Sync configured?
The modern Password Sync requires the Password Filter configured on the Domain Controller as a separate installation, and the Modern Password Copy option must be enabled in the Environment setting under Domain Controller Tab.
I have the legacy Password Sync configured, do I need to upgrade to the modern Password Sync right away?
The Modern Password Sync introduces compatibility with Domain Controllers featuring Advanced LSA Protection. If the Active Directory environment has Advance LSA Protection enabled, you should start using the Modern Password Sync to perform Password Synchronization. The legacy Password Sync will continue to work for the environment without Advance LSA Protection enabled. There is planning to retire the Legacy Password Sync in the future, we will provide additional details when the retirement date is available.
I have a multi-domain forest setup for my Active Directory, do I have to install the password filter on all the domain controllers?
In a multi-domain forest setup, at least one domain controller per domain should be configured with Password Filter Plugin and the domain controller should be selected in the Domain Controllers tab under Directory Sync Environment setting page.
I have RC4 disabled in my Active Directory, will the Modern Password Sync service support when RC4 is disabled?
The product team is working on an add-on Password Propagation Service in addition to the Modern Password Sync Service. With Password Propagation Service, RC4 limitation will be addressed, and Password Propagation Service is scheduled to release Q1, 2024.
Which files/folder do we need to whitelist if my Anti-Virus application is blocking the Password Copy?
The following folder/file should be whitelisted after Password Filter is configured on the Domain Controller(s).
- C:\ProgramData\Quest\PwCopy. This folder contains the local audit logs for the Password Copy.
- C:\Windows\System32\QDSPwFilter.dll. This is the Password Filter configured on the Domain Controller(s).