InTrust is a powerful framework for enterprise log management, provision of regulations compliance and IT data analytics.
InTrust focuses on logs, which make up the bulk of IT data in the enterprise. The log-oriented approach helps you achieve the following:
InTrust has many components, but not all of them are needed for most scenarios. The extended components are few, accessible and easy to deploy; yet they cover the most common log management needs and incorporate impressive InTrust expertise.
The remaining components help manage rare logs, implement specialized scenarios and provide advanced capabilities such as reporting powered by SQL Server Reporting Services and real-time monitoring with alerts and automated response.
The other components you can set up are also built around InTrust Server but geared for a different workflow and style of configuration. These components form an extended InTrust deployment.
The following terms are important for understanding the basics of InTrust.
An InTrust server is a computer where the InTrust Server component is set up. It processes requests from client applications such as Repository Viewer and InTrust Deployment Manager, performs the operations they request and handles the configuration.
The repository is the primary type of data store in InTrust. Repositories are intended for long-term archiving of data in a compressed format. For fast access to the data they contain, repositories have indexes, which are maintained by the InTrust server.
Repositories are normally file-based, but in extended deployments you also have the option of associating a repository with an appliance.
The same repository can be used for both real-time gathering and scheduled task-based gathering; the only restriction is that the same data from the same computers must not be gathered using both methods at once.
An InTrust organization is a group of InTrust servers with a shared configuration, for which a SQL Server database is used.
An InTrust organization provides the following:
An InTrust agent is an application which is usually automatically installed by InTrust Server on target computers to locally perform audit data gathering and, in extended deployments, real-time monitoring. Alternatively, you install and uninstall agents explicitly using InTrust Deployment Manager (or InTrust Manager). However, you can install InTrust agents manually (for example, if the target computer is behind a firewall or in an untrusted domain). In addition, a Windows Installer package for the InTrust agent makes it possible to manage agent installations using Group Policy.
During its operation an agent communicates with InTrust Server over the TCP protocol. In complex environments, agents require only one open port to allow incoming traffic to the InTrust server address.
|
|
Note: For extended deployments, consider the following:
|
If an agent cannot connect to the InTrust Server for the certain time period (for example, if the InTrust server was removed), it is “retired” (uninstalled) automatically.
The following diagram summarizes the points made in the Introduction to InTrust topic and shows where the components fit in the big picture. The roles of the users shown here are pure examples. Of course, each of them can benefit from all of the client applications.
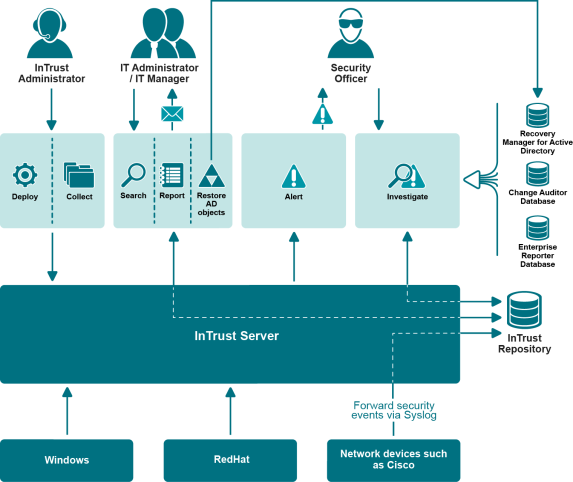
Note that the diagram shows InTrust deployment. For a representation of an extended deployment, see Technical Insight.
This is a breakdown of how InTrust handles heterogeneous audit data. Instead of "log", the broader term "data source" is used, because some of the valuable transient data that InTrust can watch is not strictly logs.
The real-time gathering feature is part of full AeCDSuiteLauncher suite .
The task-based gathering and real-time monitoring features come with the extended deployment.
64-bit architecture:
32-bit architecture:
| Data sources | Real-time gathering | Task-based gathering | Real-time monitoring |
|---|---|---|---|
| Windows event logs (such as Application or Security log) | Yes | Yes | Yes |
| User session events captured by the InTrust agent for superior user activity tracking | Yes | Yes | Yes |
| Text logs of any format | No | Yes | No |
| Windows Security Log events collected by Microsoft System Center Operations Manager 2007 and 2012 Audit Collection Services | No | Yes | No |
| Data sources | Real-time gathering | Task-based gathering | Real-time monitoring |
|---|---|---|---|
| Linux Syslog | No | Yes | Yes |
| Text logs of any format | No | Yes | No |
| Configuration files (modifications) | No | Yes | Yes |
| Data sources | Real-time gathering | Task-based gathering | Real-time monitoring |
|---|---|---|---|
| Linux Syslog | No | Yes | Yes |
| Text logs of any format | No | Yes | No |
| Configuration files (modifications) | No | Yes | Yes |
Ubuntu Linux 18.04
| Data sources | Real-time gathering | Task-based gathering | Real-time monitoring |
|---|---|---|---|
| Linux Syslog | No | Yes | Yes |
| Text logs of any format | No | Yes | No |
| Configuration files (modifications) | No | Yes | Yes |
| Data source | Real-time gathering | Task-based gathering | Real-time monitoring |
|---|---|---|---|
| VMware vCenter, ESX and ESXi events | No | Yes | No |
Trend Micro InterScan Web Security Virtual Appliance 6.5
| Data source | Real-time gathering | Task-based gathering | Real-time monitoring |
|---|---|---|---|
| Syslog messages forwarded from virtual appliances to Linux hosts | No | Yes | Yes |