How to estimate the required SQL server disk space
How SQL Server Autogrow affects Change Auditor
How to query an archive database
To query an archive (6.x) database, you need to:
|
2 |
|
3 |
On the Manage Connection Profiles dialog, select Add to start the Connection wizard. |
|
4 |
|
6 |
On the last page of the wizard, name your profile and select Finish to save it. |
|
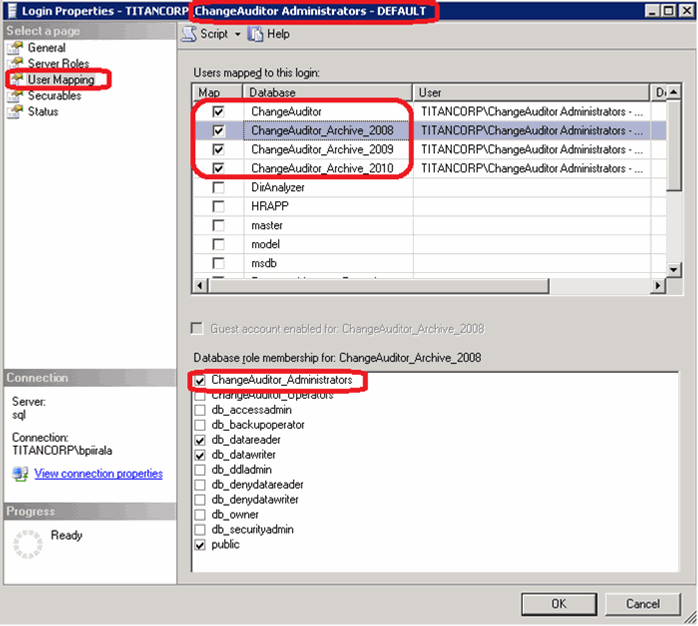
For more information about adding accounts to the Change Auditor database role, see the Change Auditor Installation Guide. |
Account exclusions best practices
Other trusted user accounts can be manually excluded from auditing. If you find that trusted accounts are generating large numbers of unwanted audit events, or if Exchange Server utilization is unusually high when such accounts are active and Change Auditor is running, Quest recommends that you exclude the accounts as described here to reduce overhead and improve performance of the agent.
|
1 |
Select View | Administration to open the Administration Tasks tab. |
|
2 |
Click Auditing. |
|
3 |
Select Excluded Accounts (under the Configuration heading) to open the Excluded Accounts Auditing page. |
|
4 |
Click Add to start the Excluded Accounts wizard. |
|
• |
Template Name — enter a descriptive name for the template. For example, Exclude BlackBerry Service Account. |
|
• |
Facility/Event Class list (middle pane) — scroll and locate the Exchange Mailbox Monitoring events. Select one of these events, click Add, and select Add All Events in Facility. |
|
NOTE: Using the Add All Events in Facility option is important because excluding the entire facility allows Change Auditor to ignore all Exchange activity for this account, reducing CPU utilization in the Exchange store or client access service. Excluding some or all individual mailbox monitoring events using the Add This Event option disables those events, but does not reduce utilization. |
|
6 |
|
7 |
Click the down-arrow on the Finish button and select Finish and Assign to Agent Configuration to assign the template to the configuration that applies to the agents on the Exchange Servers hosting the Exchange Server Mailbox role (Exchange 2013 and higher). |
|
9 |
Click OK to save the changes and close the dialog. |
|
10 |
On the Agent Configuration page, confirm that each Exchange Server agent has Auditing in the Exclude Account column. |
|
11 |
After confirming that your Excluded Account template is assigned to the correct agent configuration and is enabled, open the Deployment page (View | Deployment) to deploy an agent to the Exchange Servers. |