Managing information system security is a priority for every organization. In fact, the level of security provided by software vendors has become a differentiating factor for IT purchase decisions. Quest strives to meet standards designed to provide its customers with their desired level of security as it relates to privacy, confidentiality, integrity, and availability.
This document describes the security features of On Demand Migration for SharePoint. This includes access control, protection of customer data, secure network communication, and cryptographic standards.
Use On Demand Migration for SharePoint to migrate Microsoft SharePoint site collections, and the sites, lists, list items, document libraries, and documents contained in the site collections, between Office 365 tenancies.
Most of these services are delivered via Microsoft Azure cloud services.
The following schema shows the key components of the On Demand Migration for SharePoint configuration.
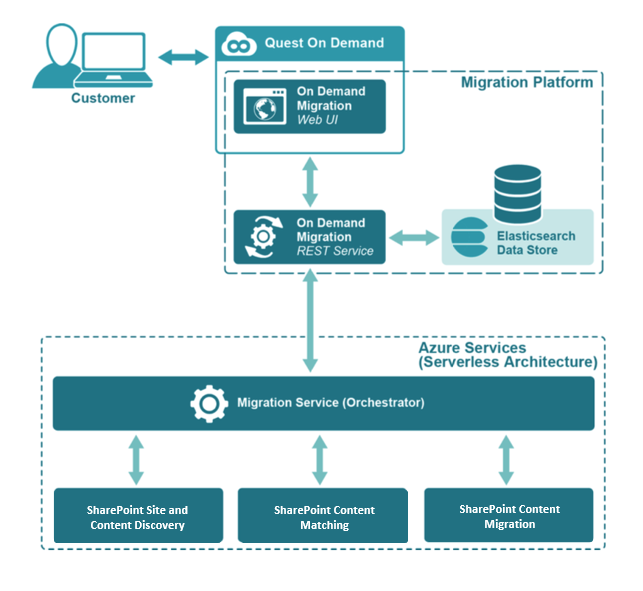
Authentication is required when you log on to On Demand. Authorization is the consent required to create and access an On Demand organization.
User access to On Demand Migration for SharePoint is authenticated with Microsoft Entra ID. Authenticating with Microsoft Entra ID offers inherent granular control and enables centralized configuration management. This method permits the configuration of advanced security layers using your own conditional access policies, including Multi-Factor Authentication (MFA), integration with Okta Inc., and other applications compatible with the Microsoft Authentication Library (MSAL).

The process of registering
A Microsoft Entra ID access token (constrained to the Quest On Demand application) is obtained when the user navigates through the authentication process. This Microsoft Entra ID access token has a lifetime limit of 10 minutes after which it is automatically refreshed if the user is actively using the application. The user is automatically logged out following a period of inactivity. If the user token is revoked in Microsoft Entra ID, the user will continue to have access to On Demand until the token expires after 10 minutes. User access to the On Demand organization can be also revoked within On Demand by an On Demand Organization Administrator, resulting in access loss after token expiry.
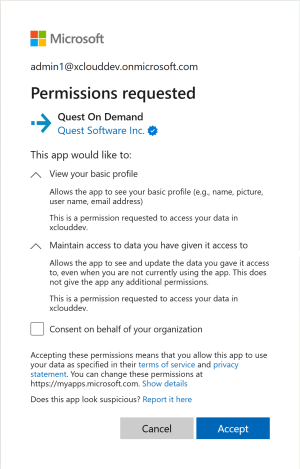
As part of the login process with Microsoft Entra ID, users must consent to the set of minimal permissions required by the Quest On Demand application. By default, all users are allowed to consent to applications for permissions that do not require administrator consent. This behavior might be deactivated in some Microsoft Entra ID tenants and may require tenant administrators to enable user consent flow for the Quest On Demand application.
The base consents required by Quest On Demand is shown below.
|
NOTE:
|