When a customer signs up for On Demand, they select the region in which to run their On Demand organization. All computation is performed, and all data is stored in the selected region. The currently supported regions can be found here: https://regions.quest-on-demand.com/.
Mail messages intended for processing by Address Rewrite Service servers are temporary stored at Azure Virtual Machine disks before being delivered to recipients. The data are encrypted at rest.
Windows Azure Storage, including the Blobs, Tables, and Queues storage structures, are replicated three times in the same datacenter for resiliency against hardware failure. The data is replicated across different fault domains to increase availability. All replication datacenters reside within the geographic boundaries of the selected region.
See this Microsoft reference for more details: https://docs.microsoft.com/en-us/azure/storage/common/storage-redundancy
The most sensitive customer data processed by On Demand Migration is the Microsoft Entra ID and Office 365 data including users, groups and contacts and their associated properties, content of emails and OneDrive for Business. On Demand Migration does not store or deal with end-user passwords of Microsoft Entra ID objects.
To ensure that customer data is kept separate during processing, the following policies are strictly applied in On Demand Migration:
More information about Azure queues, tables, and blobs:
A common concern related to cloud-based services is the prevention of commingling of data that belongs to different customers. On Demand Migration has architected its solution to specifically prevent such data commingling by logically separating customer data stores.
Customer data are differentiated using a Customer Organization Identifier. The Customer Organization Identifier is a unique identifier obtained from the Quest On Demand Core that is created when the customer signs up with the application.
This identifier is used throughout the solution to ensure strict data separation of customers' data in Elasticsearch storage and during processing. A separate Elasticsearch server instance is used for each customer.
When domain coexistence is turned on, separate Azure Virtual Machines, Network Security Groups and inbound IP address are used as an outgoing mail transfer agent for each migration project.
Internal network communication within Azure includes:
The following scheme shows the communication configuration between key components of On Demand Migration.
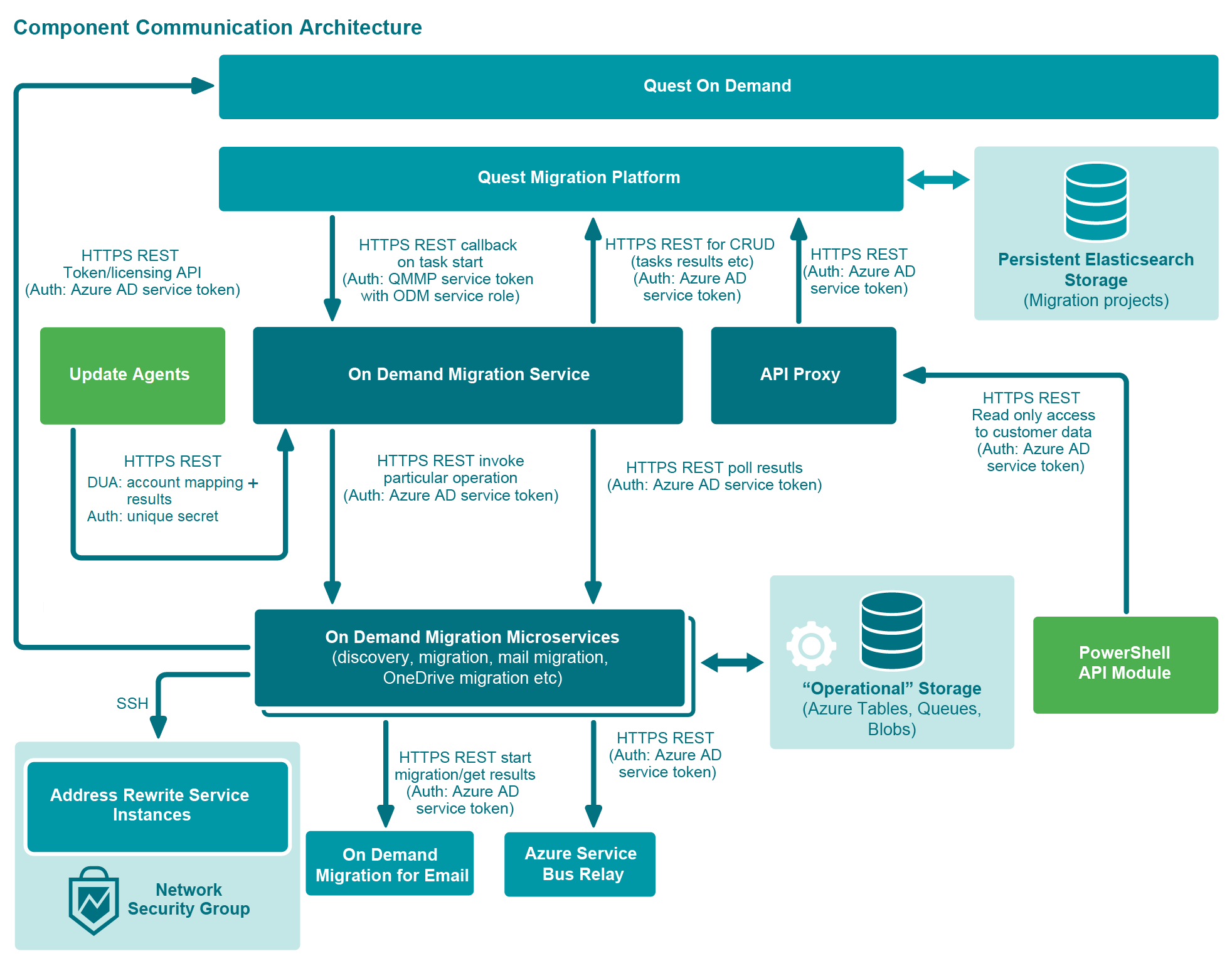
Figure: Component Communication Architecture
The network communication is secured with HTTPS and is not visible to the external public internet.
Inter-service communication uses OAuth authentication using a Quest Microsoft Entra ID service account with the rights to access the services. No backend services of On Demand Migration can be used by end-users.
On Demand Services accepts the following network communication from outside Azure:
All external communication is secured with HTTPS.
The On Demand Migration user interface uses OAuth authentication with JWT token issued to a logged in user.
All requests from Desktop Update Agents (DUA) deployed on customer’s workstations are signed with the certificate, issued by On Demand Migration. The certificate is deployed (either automatically or manually) by customer’s IT specialist to each workstation’s certificate store. The certificate can be revoked at any time by generating a new one using On Demand Migration interface.
Communication between DUA and On Demand Migration is secured with HTTPS/TLS 1.2 and secret-based authentication.
PowerShell cmdlets used by Quest Support are using Microsoft Entra ID authentication to access the On Demand Migration service. The user of the PowerShell API should be a Quest Microsoft Entra ID member with the appropriate role assigned.
There are no unsecured HTTP calls within On Demand Migration.