Introduction
On Demand Migration Active Directory supports device migrations to Microsoft Entra ID from Domain Joined, Hybrid Domain Joined, and Entra Joined workstations running Windows 10 or Windows 11 while preserving the User Profiles and File/Folder Security Permissions.
This step-by-step guide walks you through how to configure a Project to perform device migration to Microsoft Entra ID using On Demand Migration for Active Directory. For device migrations using other On Demand products, please see the guide for your product: On Demand Migration Active Directory Express or On Demand Migration Entra ID for Devices.
Topics
This guide covers the following topics:
-
Microsoft Entra ID Device Join Requirements
-
Environment preparation
-
Prepare the Provisioning Package
-
Configure and synchronize your objects between source On-Premises Active Directory and target Microsoft Entra Tenant
-
Configure Device Migration Project
-
Perform Device Microsoft Entra ID Join migration
-
Validate the device post Microsoft Entra ID Join
-
Frequently Asked Questions
Requirements
General
-
Client is licensed for On Demand Migration Active Directory and Directory Sync
-
Client is licensed for On Demand Migration Azure Device Migration Add-on
-
One Global Administrator Account for each Microsoft 365 tenant
-
One Domain Administrator Account for each On-Premises Active Directory attached to the tenant
-
One dedicated server to install the Directory Sync agent
-
Permissions to download and install Directory Sync agent

The local agent must meet the following minimum hardware requirements:
-
At least one (1) Windows Server 2012 R2, 2016 or 2019
-
Additional Windows servers may be deployed; limit of 5.
-
CPU: 4 Cores
-
Memory: 4GB Free
-
Disk: 40GB Free Disk Space excluding Operating System

The local agent must meet the following minimum software requirements:
-
Windows Server 2012 R2, 2016 or 2019
-
.NET 4.7.2. NOTE: .NET will automatically be installed if needed.
-
TLS 1.2 or higher
Domain and Forest Functional Levels
All AD Functional Levels supported by Microsoft for a Microsoft Windows Server operating system listed below are supported for migration from/to Domain controllers running on that same Operating System. For example, Windows Server 2016 functional levels are supported on Windows Server 2022, Windows Server 2019, and Windows Server 2016. For full details see Microsoft’s documentation of Active Directory Domain Services Functional Levels in Windows Server on Microsoft Learn.
-
NOTE: Windows Server 2003 functional levels are supported only on Windows Server 2016, Windows Server 2012 R2, and Windows Server 2012. That is, Microsoft does not support Windows Server 2003 functional levels on Windows Server 2019 or Windows Server 2022.
-
NOTE: Microsoft's lifecycle for Windows Server 2012 ends extended support on October 10, 2023. Customers should be planning to move their Domain Controllers off of Windows Server 2012 and Windows Server 2012 R2 by that date.
-
Directory Sync web interface uses TCP port 443 (HTTPS).
-
Agent web connections use port 443 to Directory Sync host application.
-
DCs use TCP ports 139, 389 (UDP), 445, and 3268.
-
SID History functionality uses TCP ports 135, 137-139, 389 (UDP), 445, 1027, 3268, and 49152-65535. (Optional)
Local Active Directory Account (Optional, required for Hybrid Tenant)
-
Agent installer will prompt for a domain account with permission to read and write on-premises Active Directory.
-
An agent intended to sync all domains in a forest must have rights to all domains and objects used in workflows.
Microsoft Entra ID Application Account
-
An account with Global Administrator Role is required to grant permissions and establish connection when adding a Cloud Environment.
Microsoft Entra ID PowerShell Accounts
-
Three (3) PowerShell accounts are automatically created to read and update objects in the cloud. To do this, an OAuth token is used from the account used to add the Cloud Environment.
-
These PowerShell accounts do not require any Microsoft 365 licenses.
Environment Preparation
Environment Preparation
This section will review the environment setup that will be used to perform Microsoft Entra ID Device Join. To facilitate the migration, please confirm you have the following:
-
A source environment that is either on premise Active Directory or a Hybrid Microsoft Entra tenant including a local on-premises Active Directory with Microsoft Entra Connectconfigured.
-
A source environment that is Microsoft Entra ID only tenant.
-
A target environment that is either an Microsoft Entra ID Only tenant or is a Hybrid Microsoft Entra tenant including a local on-premises Active Directory with Microsoft Entra Connectconfigured.
-
A file share that is accessible by the workstation, the file share will be used to store the provisioning package which is needed to perform the Microsoft Entra ID Join. Later in this guide, we will review how to create the provisioning package using Windows Configuration Designer (WCD).
-
A Windows Workstation running Windows 10 (Build 1709 or later), or Windows 11.
Device Microsoft Entra ID Join status
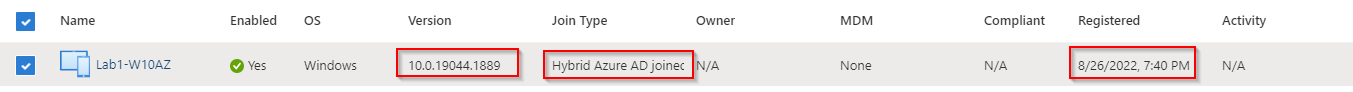
Microsoft Entra ID Portal Device View

