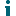To pair SpecterOps BloodHound Enterprise with On Demand Audit to help provide a comprehensive risk assessment and threat monitoring solution, you need to add a SpecterOps BloodHound configuration.
|
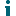
|
NOTE:
-
To manage a SpecterOps BloodHound Enterprise configuration, you must have the Can Manage SpecterOps BloodHound Configuration permission.
-
Once the configuration has been added, you can select the three vertical dots in the upper right-corner to refresh the configuration immediately, to edit the notification template, or to read more about the benefits of integrating with SpecterOps BloodHound Enterprise.
-
The configuration connection message details whether the connection the SpecterOps has been successful, and the status of the configuration. |
To add a configuration:
- From the Configuration tab, select Add BloodHound Enterprise or click the + icon.
-
Enter the SpecterOps BloodHound URL, the Permanent Authorization Token (PAT) Token ID, and Key pair.
-
Click Validate to validate the URL format (https://yourdomain.bloodhoundenterprise.io.), the Permanent Authorization Token (PAT) Token ID, and the Key pair.
-
Click Save.
Once the configuration has been added, you can select to edit the Tier Zero notification template to configure who will be notified when an alert is triggered.
To edit a configuration:
- From the Configuration tab, select the BloodHound Enterprise card, and choose Edit Configuration.
-
Edit the SpecterOps BloodHound URL, Permanent Authorization Token (PAT) Token ID, and Key pair as required.
-
Click Validate to validate the URL format (https://yourdomain.bloodhoundenterprise.io.), the Permanent Authorization Token (PAT) Token ID, and the Key pair.
-
Click Save.
To remove a configuration:
|
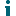
|
IMPORTANT: When you remove a configuration, SpecterOps BloodHound Enterprise information will no longer be added to events in On Demand Audit. |
-
From the Configuration tab, select the BloodHound Enterprise card, and choose REMOVE.
-
Click YES to remove the configuration.
Working with On Demand Audit
When you open On Demand Audit, the dashboard displays a visual summary of the most important metrics of the Microsoft 365 and Microsoft Entra activity in your organization. The information is updated in real time, allowing you to quickly gain valuable insights into the activity taking place in your organization. You can also refresh the data by selecting the refresh icon in the top right of the dashboard.
The dashboard displays:
The indicators at the top of the dashboard allow you to quickly see if there has been a change in risky activity over a specific period of time. A red sidebar indicates an increase in activity; while a green sidebar indicates a reduction.
You can then easily delve further into the details, by clicking the indicator to view an associated search.
|
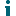
|
NOTE: The indicators are updated each time that you open the dashboard or refresh the view. |
The following indicators are available:
-
Cloud-only Microsoft Entra users created in the last 7 days
-
AD account lockouts in the last 24 hours
If you do not have a configured Change Auditor integration, the Microsoft Entra critical directory role changes in the last 7 days indicator displays instead.
-
Microsoft Entra risk events in the last 7 days
This indicator displays when you have an Microsoft Entra ID Premium (P2) license.
If you do not have the required license to audit risky events and Change Auditor integration is configured, the On-premises and Microsoft Entra failed sign-ins in the last 24 hours indicator displays instead.
If you do not have the required license to audit risky events and have not configured a Change Auditor integration, the Microsoft Entra failed sign-ins in the last 24 hours indicator displays.
- Microsoft 365 external user actions in the last 24 hours