Configuring Windows Event Log Monitor agent properties
For more information about the Windows Agent, see the Managing Infrastructure User and Reference Guide.
This agent includes the following groups of agent properties:
For a configuration example, see WindowsEventLogMonitor configuration example.
Monitored Hosts
The Monitored Host properties specify the hosts whose log files you want to monitor with this the agent.
|
• |
Hosts: A list specifying the hosts monitored by the agent instance. Typically you want a cloned list that is associated with a specific agent instance. Each entry in the list includes the following columns: |
|
• |
Host: The name of the monitored host or its IP address. |
|
• |
Host name override: The host name under which this host’s data is stored in the data model. This property is optional. |
|
• |
Network Operation Timeout (seconds): The maximum amount of time in seconds given to the agent for each phase of a collection attempt. This includes uploading the native executable, scanning for log entries, and retrieving log content. |
|
• |
Collect System ID: This property indicates to the agent whether or not to collect a unique system ID from this system. This is not desirable when monitoring Hyper-V systems, as some Hyper-V systems use the same ID for multiple systems, preventing them from being unique. |
|
• |
Remote Collector Executable: The name of the agent native executable on the remote monitored host. This property is optional. If not specified, a random name is used. Configure this property only if you need to set a specific name for the executable so that you can write a sudo rule for it, or to have it uploaded to a non-default directory. In that case, provide a complete a full path name along with the file name. |
|
• |
Maximum Record Match Count Per Log File: The maximum number of records the agent reads per log file. Setting this value to a reasonable number of records (for example, 200) allows you to control the amount of time and resources the agent spends to read monitored logs during a single collection interval, and to prevent bottlenecks during data collection. If you do not want to specify a limit, type -1. |
|
• |
Backlog of Events (seconds): The length of time in the past to start collecting data from until the present moment, if not already processed. Specifying a reasonable amount of time using this property (for example, 3,600 seconds or one hour) allows you to bring in historical data, providing a point of reference for future collections. |
|
• |
Max Logs Processing Time (seconds): The amount of time in seconds given to the agent for a data collection attempt. Setting this value to a reasonable number of seconds (for example, 120) allows you to control the amount of time the agent spends to read monitored logs during a single collection interval, and to prevent bottlenecks during data collection. |
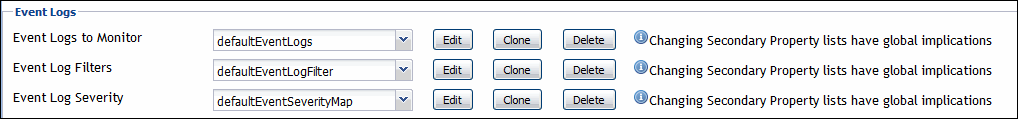
Event Logs
The Event Logs properties allow you to specify the Windows Event Logs and the type of records you want to monitor.
|
• |
Event Logs to Monitor: A list specifying the types of Windows Event Logs monitored by this agent. Each entry in the list includes the following column: |
|
• |
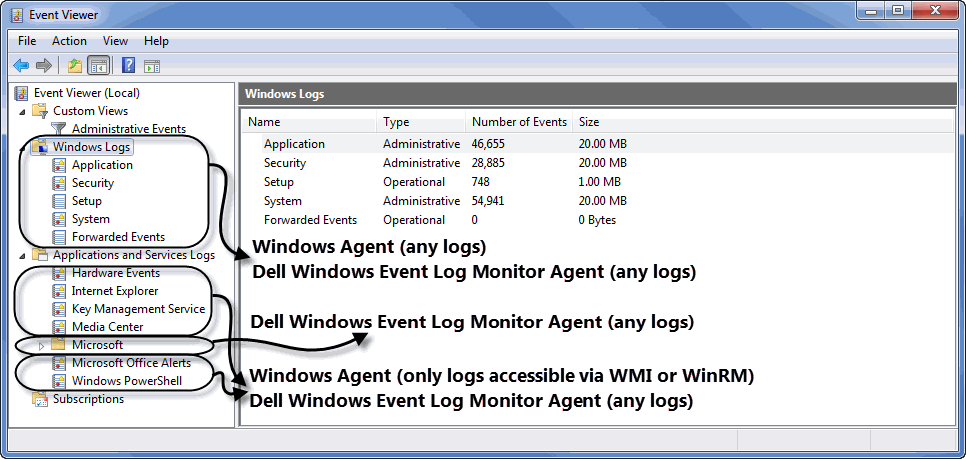
Event Log Name: The name of the Windows Event Log whose files you want to monitor with this agent. This value must be identical to the Full Name value, seen in the Log Properties dialog box. To find out an event log name, in the Event Viewer, right-click a Windows Log, choose Properties from the shortcut menu, and look for the Full Name property in the dialog box that appears. |
|
• |
Event Log Filters: A list specifying the types of Windows Event Log entries that you want to monitor with this agent. Using this list you can configure the agent to include and exclude specific entries from its collections using Include and Exclude commands, as required. By default, the agent does not collect any data unless configured to do so. For example, instructing the agent to exclude certain log types from its collections, without specifying which types of log items to include, prevents the agent from collecting any data from Windows Event Logs. |
|
NOTE: For log filters that signify “any” (that is, you do not want to filter on this property), the User, Source, Category, and Event Description properties should all have a value of “*”, and the EventID property should have a value of “0”. |
|
• |
Include/Exclude: Instructs the agent to include or exclude certain types of logs from its collections. |
|
• |
Type: The Windows severity level: *(All), Information, Warning, Error, Success Audit, or Failure Audit. For more information about these levels, see your Windows documentation. |
|
• |
User: The name of the user who initiated the Windows Event. |
|
• |
Source: The name of the Windows Event Log to which the event is published. |
|
• |
|
• |
EventID: The Windows Event ID. For more information about Windows Event IDs, see your Windows documentation. |
|
• |
Event Description: The description of the Windows event. |
|
• |
Tags: The tag associated with the record, as specified in the agent properties. |
|
• |
Event Throttle Count: When set, this ensures that one event in every count (the event log entry occurrence that the filter applies to) is submitted to the Management Server. If the count is one or less, then every event log entry occurrence is submitted and no throttling is done. The default is zero ‘0’. |
|
• |
Event Throttle Duration (seconds): This value represents the duration in seconds for the throttle count to be applied. When set, the throttle count is applied within a duration. After the duration expires, the throttling restarts from the beginning regardless of the current throttle state. If the count is one or less, then only one event log entry the filter matches is submitted within the specified duration. If the count is larger than one, then only one in every count (the event log entry occurrence that the filter matches) is submitted, and the agent starts counting pattern matches from zero after the duration. The default value is zero '0', which means the duration is not applied. |
|
NOTE: The Event Throttle Count and Event Throttle Duration (seconds) properties only apply to INCLUDE-type filters (and not EXCLUDE-type filters), since throttling is necessary only if a message is being included (and submitted). |
|
• |
Event Log Severity: A mapping that specifies how Windows Event Log severities relate to Foglight severity levels. A default agent installation includes a complete mapping. You can make changes to it when configuring Windows Event Log Monitor Agent instances, if required. |
Record Transformations
The Record Transformations properties allow you to transform any log message before it is sent to the Management Server. This could be used to add extra information or to remove sensitive information from a log record.
|
• |
Record Transformations: A list of record transformations that the agents must use in conjunction with the match patterns to convert any log messages. When no transformation is specified, the log record is transmitted to the Management Server without changes. |
|
• |
RegEx Record Transformation Pattern: A regular expression that the agent uses to look for specific text in the collected log record. |
|
• |
Record Transformation: The replacement text that the agent uses in the log record to be transmitted to the Management Server. |