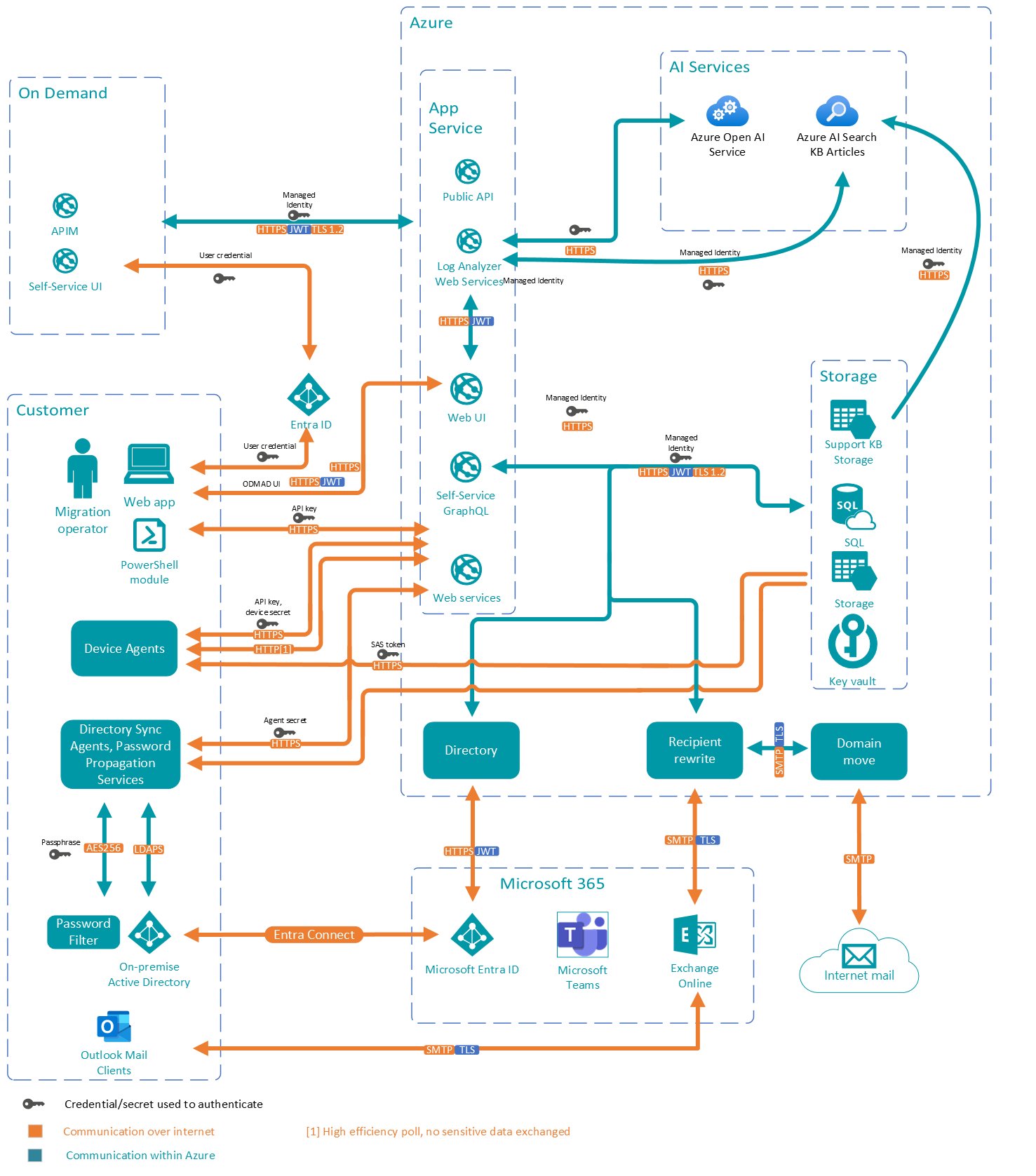
Customer data is further separated as customer related services are isolated from any other OS process by the Microsoft Service Fabric exclusive process model. See https://docs.microsoft.com/en-us/azure/service-fabric/service-fabric-hosting-model#exclusive-process-model for more information.