Running a search
Once an event is captured, you can view all available event data through searches. You can use custom searches based on your own criteria or built in searches that are configured to meet the most common requests. See Creating a custom search and Using built in searches.
|
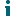
|
NOTE: Custom user-built searches are identified by the following icon to the left of the search.

|
To run a previously saved or built in search
- Select the Searches tab.
- Locate the required search in the list of categories.
- To run the search, simply click it or highlight it and click the run (arrow) icon.
From here you can:
Using built in searches
Built-in searches provide quick access to important configuration change details from multiple perspectives. These are shared searches.
While you cannot modify a built-in search directly, you can create a new search based on it and customize the settings to meet your requirements. See Creating a search from an existing search.
The following built in searches are available:
- All Events category
- All events in the past 24 hours
- All events in the past 7 days
To run a built in search
- Select the Searches tab.
- Locate the search in the required category.
- Highlight the search and click the arrow icon to run it.
From here you can:
Active Directory Built in searches
If you have a Change Auditor installation registered with On Demand, you will have access to the following Active Directory built-in searches:
- AD all account lockout events in the past 7 days
-
AD all adminCount attribute changed events in the past 30 days
- AD all attribute changes in the past 7 days
- AD all computer events in the past 7 days
- AD all domain controller events in the past 7 days
- AD all events in the past 24 hours
- AD all events in the past 7 days
- AD all events including ActiveRoles/GPOADmin initiator in the past 7 days
- AD all forest configuration events in the past 7 days
-
AD all inheritance settings changed events in the past 30 days
- AD all objects deleted in the past 7 days
- AD all OU events in the past 7 days
- AD all replication events in the past 7 days
- AD all schema configuration events in the past 7 days
- AD all security changes in the last 30 days
-
AD all sIDHistory attribute changed events in the past 30 days
-
AD all high severity sIDHistory attribute changed events in the past 30 days
- AD all site events in the past 7 days
- AD all user events in the past 7 days
- AD computers added in the past 30 days
- AD computers disabled in the past 30 days
- AD computers enabled in the past 30 days
- AD computers moved in the past 30 days
- AD computers removed in the past 30 days
- AD computers renamed in the past 30 days
- AD critical group membership changes in the past 30 days
- AD group added in the past 30 days
- AD group deleted in the past 30 days
- AD group member added changes in the past 30 days
- AD group member removed changes in the past 30 days
- AD group moved in the past 30 days
- AD group nested member added changes in the past 30 days
- AD group nested member removed changes in the past 30 days
- AD group renamed in the past 30 days
-
AD irregular domain controller registration events in the past 30 days
- AD irregular domain replication detected events in the past 30 days
- AD user ServicePrincipalName attribute changes in the past 30 days
- AD users added in the past 30 days
- AD users added to group in the past 30 days
- AD users deleted in the past 30 days
- AD users disabled in the past 30 days
- AD users enabled in the past 30 days
- AD users locked out in the past 30 days
- AD users moved in the past 30 days
- AD users removed from group in the past 30 days
- AD users renamed in the past 30 days
- AD users unlocked in the past 30 days
See Change Auditor Integration for details on adding on-premises event data to your On Demand deployment.
Active Directory Federation Services built in searches
Audit provides the following Active Directory Federation Services built in searches:
-
AD FS All claims provider trust events in the past 30 days
- AD FS All relying party trust events in the past 30 days
- AD FS All endpoint events in the past 30 days
-
AD FS All authentication method changes in the past 30 days
-
AD FS All server farm events in the past 30 days
-
AD FS Authentication method registered and unregistered events in the past 30 days