After you have taken all the necessary configuration steps on the target Linux hosts, the InTrust server takes over all auditing and real-time monitoring operations. Linux auditing and real-time monitoring is similar to working with any other system supported by InTrust. Use the InTrust Manager console to set up audit data gathering and monitoring.
There is only one important difference that refers to active scheduling of the InTrust tasks. For information see the warning note below.
|
|
Caution: An active schedule on an InTrust task is required to make the agent cache events. If the schedule is disabled, no events are stored. The "IWSVA through Oracle Linux Syslog" data source uses event caching, so it is recommended that you use at least one task for the cache-enabled data sources that run regularly. If you want to gather data only on demand, you must still enable the schedule for your task or tasks, but set it to a point in the future or in the past. |
The other operations do not have special requirements, and you can perform them as described in the Auditing Guide and Real-Time Monitoring Guide.
The "IWSVA through Oracle Linux Syslog" data source represents InterScan Web Security Syslog audit trails. It analyzes the flow of data forwarded to the Syslog daemon and makes meaningful event records from the data.
The data source uses a list of regular expressions. When the data source is working, it applies the expressions, in the order specified, to each message. The order of the regular expressions matters because message processing stops as soon as the message matches one of the expressions. During parsing, pairs of parentheses are used in regular expressions to break messages up into numbered fields.
|
|
Caution: It is not recommended that you modify predefined regular expressions in the data source. However, you can experiment with a copy of the predefined data source if necessary. Do not include a lot of complex regular expressions in the data source, because that may slow down Syslog processing significantly. |
After you have set up the Syslog daemon, as described in Syslog Configuration, and adjusted the gathering settings in InTrust, as described in InTrust Configuration, configure forwarding of InterScan Web Security Virtual Appliance logs to the Linux host. The Linux host with an installed InTrust agent will act as a Syslog listener.
For information on how to configure the logs to be sent to the Syslog server, refer to InterScan Web Security Virtual Appliance documentation.
For these scenarios to work, first include the necessary Linux host or hosts in the "IWSVA hosts" site.
After you have made sure that InTrust collects virtual appliance logs to the repository, you can view the logs in InTrust Repository Viewer. Suppose you want to focus on URL access. For that purpose, you can create a custom Repository Viewer search folder which includes event ID 555 from the and use the Who field from Normalized Strings as well as any other filter parameters as follows:
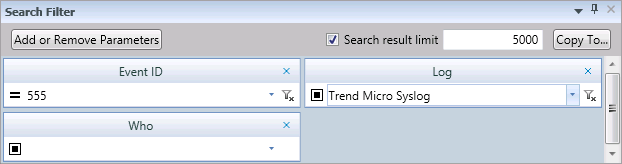
Now you can track URL access by these users. Click Go to view available events. You can configure the configure the layout of the result grid as necessary. For more details, see Searching for Events in Repository Viewer.
In this scenario, you configure InTrust to raise alerts whenever a virtual appliance detects a virus. Take the following steps in InTrust Manager:
After this, the specified recipients will get email notifications every time the virtual appliance sends a virus detection message to the monitored Linux host, and InTrust will trigger alerts, which you can view and manage in Monitoring Console.
This topic lists Trend Micro InterScan Web Security Virtual Appliance events that InTrust recognizes during task-based gathering and real-time monitoring.
Original ID: EVT_VIRUS_FOUND | LOG_CRIT
InTrust event ID: 547
Fields:
|
Field name |
Field description |
Insertion string |
|---|---|---|
|
tk_username |
User ID (client IP address) |
6 |
|
tk_date_field |
Date and time |
7 |
|
tk_protocol |
Protocol |
8 |
|
tk_url |
URL |
9 |
|
tk_malicious_entity |
Types of malware |
10 |
|
tk_file_name |
File name |
11 |
|
tk_entity_name |
Detected malware name |
12 |
|
tk_action |
Processing |
13 |
|
tk_scan_type |
Scan type |
14 |
|
tk_blocked_by |
[unused] |
15 |
|
tk_rule_name |
Rule (policy) name |
16 |
|
tk_opp_id |
[unused] |
17 |
|
tk_group_name |
Group name (if LDAP is available) |
18 |
|
tk_category |
Category |
19 |
|
tk_uid |
Internal ID |
20 |
Original ID: EVT_SPYWARE_FOUND | LOG_CRIT
InTrust event ID: 548
Fields: same as for Virus Found
Original ID: EVT_DLP_FOUND | LOG_CRIT
InTrust event ID: 549
Fields:
|
Field name |
Field description |
Insertion string |
|---|---|---|
|
tk_username |
User ID (client IP address) |
6 |
|
tk_date_field |
Date and time |
7 |
|
tk_entity_name |
Template name |
12 |
|
tk_rule_name |
Rule (policy) name |
16 |
|
tk_group_name |
Group name (if LDAP is available) |
18 |
|
tk_scan_type |
Scan type |
14 |
|
tk_action |
Processing |
13 |
|
tk_protocol |
Protocol |
8 |
|
tk_url |
URL |
9 |
|
tk_malicious_entity |
Matched content |
10 |
|
tk_file_name |
File name |
11 |
|
tk_uid |
Internal ID |
20 |
Original ID: EVT_C&C_CALLBACK_FOUND | LOG_CRIT
InTrust event ID: 550
Fields:
|
Field name |
Field description |
Insertion string |
|---|---|---|
|
tk_username |
User ID (client IP address) |
6 |
|
tk_date_field |
Date and time |
7 |
|
tk_protocol |
Protocol |
8 |
|
tk_url |
URL |
9 |
|
tk_domain |
Domain |
15 |
|
tk_device_name |
Device name (host name) |
11 |
|
tk_rule_name |
Rule (policy) name |
16 |
|
tk_group_name |
Group name (if LDAP is available) |
18 |
|
tk_client_ip |
Client IP address |
13 |
|
tk_server_ip |
Server IP address |
14 |
|
tk_destination_port |
Destination port |
12 |
|
tk_ccca_source |
Detection source:
|
17 |
|
tk_risk_level |
Risk level:
|
19 |
|
tk_filter_action |
Filtering action:
|
21 |
Original ID: EVT_URL_BLOCKING | LOG_CRIT
InTrust event ID: 551
Fields:
|
Field name |
Field description |
Insertion string |
|---|---|---|
|
tk_username |
User ID (client IP address) |
6 |
|
tk_date_field |
Date and time |
7 |
|
tk_protocol |
Protocol |
8 |
|
tk_url |
URL |
9 |
|
tk_malicious_entity |
[unused] |
10 |
|
tk_file_name |
File name |
11 |
|
tk_entity_name |
[unused] |
12 |
|
tk_action |
[unused] |
13 |
|
tk_scan_type |
Search type |
14 |
|
tk_blocked_by |
Reason for blocking |
15 |
|
tk_rule_name |
Rule (policy) name |
16 |
|
tk_opp_id |
[unused] |
17 |
|
tk_group_name |
Group name (if LDAP is available) |
18 |
|
tk_category |
Category |
19 |
|
tk_uid |
Internal ID |
20 |
|
tk_filter_action |
Filtering action:
|
21 |
Original ID: EVT_URL_MONITORING | LOG_CRIT
InTrust event ID: 552
Fields: same as for URL Blocking
Original ID: EVT_URL_WARNING | LOG_CRIT
InTrust event ID: 553
Fields: same as for URL Blocking
Original ID: EVT_URL_WARN_AND_CONTINUING | LOG_CRIT
InTrust event ID: 554
Fields: same as for URL Blocking
Original ID: EVT_URL_ACCESS_TRACKING | LOG_INFO
InTrust event ID: 555
Fields:
|
Field name |
Field description |
Insertion string |
|---|---|---|
|
tk_username |
User ID (client IP address) |
6 |
|
tk_url |
URL |
9 |
|
tk_size |
File size |
10 |
|
tk_date_field |
Date |
7 |
|
tk_protocol |
Protocol |
8 |
|
tk_mime_content |
MIME content type |
17 |
|
tk_server |
Server (host name) |
12 |
|
tk_client_ip |
Client IP address |
13 |
|
tk_server_ip |
Server IP address |
14 |
|
tk_domain |
Domain |
15 |
|
tk_path |
Path |
16 |
|
tk_file_name |
File name |
11 |
|
tk_operation |
Request method |
18 |
|
tk_uid |
Internal identification ID |
20 |
|
tk_category |
Category ID For details about category mapping, |
19 |
|
tk_category_type |
Category type
|
21 |
Original ID: EVT_FTP_GET | LOG_INFO
InTrust event ID: 556
Fields: same as for URL Access Tracking
Original ID: EVT_FTP_PUT | LOG_INFO
InTrust event ID: 557
Fields: same as for URL Access Tracking
Original ID: EVT_APP_CONTROL_BLOCK | LOG_CRIT
InTrust event ID: 558
Fields:
|
Field name |
Field description |
Insertion string |
|---|---|---|
|
tk_username |
User ID (client IP address) |
6 |
|
tk_date_field |
Date and time |
7 |
|
tk_category |
Category |
19 |
|
tk_protocol |
Application name |
8 |
|
tk_rule_name |
Rule (policy) name |
16 |
|
tk_group_name |
Group name (if LDAP is available) |
18 |
|
tk_client_ip |
Client IP address |
13 |
Original ID: EVT_PERFORMANCE | LOG_INFO
InTrust event ID: 559
Fields:
|
Field name |
Field description |
Insertion string |
|---|---|---|
|
tk_server |
Server (host name) |
12 |
|
tk_date_field |
Date and time |
7 |
|
tk_metric_id |
Measured metric |
8 |
|
tk_metric_value |
Measured value |
9 |
Original ID: EVT_SYSEVENT_AU_SUCC | LOG_INFO
InTrust event ID: 560
Fields:
|
Field name |
Field description |
Insertion string |
|---|---|---|
|
tk_server |
Server (host name) |
12 |
|
tk_date_field |
Date and time |
7 |
|
tk_source |
Event source |
9 |
|
tk_description |
Description |
8 |
Original ID: EVT_SYSEVENT_AU_FAIL | LOG_xxx
InTrust event ID: 561
Fields: same as for System Information Event (Success)
Original ID: EVT_AUDITING | LOG_WARNING
InTrust event ID: 562
Fields:
|
Field name |
Field description |
Insertion string |
|---|---|---|
|
tk_user |
User login |
6 |
|
tk_date_field |
Date and time |
7 |
|
tk_description |
Description |
8 |