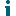Investigating Hygiene and Detected Indicators
-
vulnerabilities are detected when a Security Guardian Assessment is run
AND/OR
-
critical activity anomalies are detected by On Demand Audit.
|
|
NOTE:Hygiene indicates that objects are susceptible to an adversary attack. Detected indicates that an action took place that could possibly be an adversary attack.
|
The top of an Investigation page identifies the object being investigated, along with the following information:
-
the Severity of the Finding
-
the Finding Type (Hygiene, Detected TTP, Detected Anomaly)
-
the Finding Status (Active or Inactive)
-
MITRE ATT&CK TTP (if applicable)
NOTE: Up to three TTPs may be returned for the finding. If "+ [number]" is shown to the right of the displayed TTP, hover over the
icon to view the additional values.
-
the number of Affected Objects
-
Last Updated (that is, the last time the Finding was detected)
NOTE: Last Updated displays a relative time. However, you can hover over the clock icon to see an exact date and time (which displays the local date and time of the signed-in user).
-
options to dismiss the Finding and view history of the Finding.
What Happened?/What Is Wrong?
The What Happened? (for Detected Indicators) or What Is Wrong? (for Hygiene) page provides a description of the Finding and lists the objects that are affected. The following information is included for each object:
-
Object Name (with a link that allows you to display object details)
exception: If an Object Type is trustedDomain, Container or dnsZone, object details cannot be displayed from the Investigation page and the Object Name link will be disabled.
-
Principal Name (which is searchable)
-
Object Type
-
First Discovered date and time
NOTE: This field displays the signed-in user's local date and time.
-
Certification Status, which may be
-
Certified or Not Certified (for Tier Zero or Privileged objects)
OR
-
Not Tier Zero
NOTE: A status of "Status Not Available" may occur if the object has been deleted from Active Directory/Entra ID or the Object ID cannot otherwise be identified.
-
This section also includes a series of links to help you complete your investigation, as described in the following table.
| Link | Description | ||
|---|---|---|---|
| For Selected Objects in the list | |||
|
Object Name (for a single object) |
The properties of the object, including whether or not it is Tier Zero/Privileged, identifiers used for the object within Active Directory or Entra ID, the date the object was added and the date its information was last updated.
| ||
| Mute Object button | See Muting Findings for Hygiene and Detected Indicators. | ||
|
View Activity button (for a single object) |
This link opens the Quick Search page in On Demand Audit, which lists event data for the object being investigated. | ||
|
View Assessment button (for a single object) |
If the indicator was raised by a Security Guardian Assessment, this link opens the Assessment Results Vulnerability Detail page that includes the selected object.
| ||
| View critical activity link | If the indicator was raised by an On Demand Audit critical activity event, this link opens Critical Activity event details in On Demand Audit. | ||
| Escalate this Finding | |||
| Copy | This link allows you to copy the text of the Finding to the clipboard so that you can share it with others. | ||
| Send email | This link allows you to prepare and send an escalation email to recipients with whom you want to share the Finding. | ||
How Do I fix this?
This section provides the recommended remediation.