Usage of backup access credentials
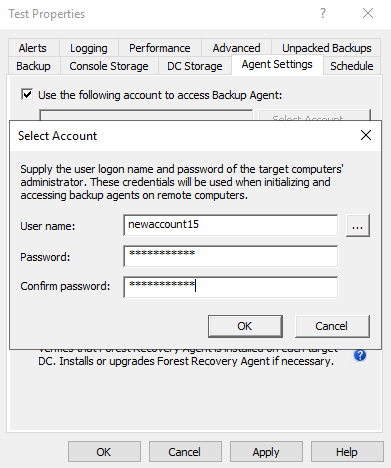
Recovery Manager for Active Directory uses the same credentials to access backup files on the remote share and to connect to Backup Agent. These credentials are specified on the Agent Settings tab of the collection properties (option "Use the following account to access Backup Agent").
If you need to specify a separate account to access the backup storage, use the option Use the following account to access the backup storage on the DC Storage tab.
When no credentials are specified in the collection properties, the Recovery Manager Console uses the account under which it is running to access the backup storage and Backup Agent.
To specify separate credentials to access the remote backup location and Backup Agent
-
Create a computer collection in Recovery Manager for Active Directory Console.
-
Right-click the computer collection, and then click Properties to open the Computer Collection Properties dialog box.
-
On the Agent Settings tab, select the option Use the following account to access Backup Agent and specify account credentials.
-
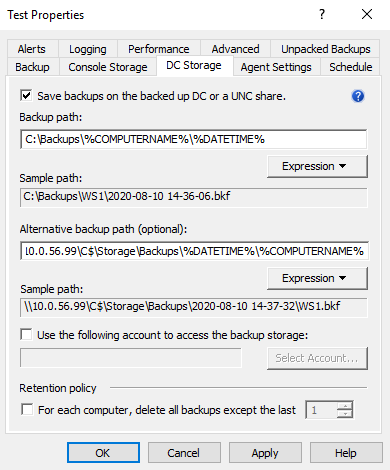
On the DC Storage tab, select the option Save backups on the DC being backed up or a UNC share and enter the backup path. You need to specify path to the remote share in the following format (%DATETIME% variable is required ):
\\<share name>\<backup folder>\%COMPUTERNAME%\%DATETIME%
| IMPORTANT |
According to the Forest Recovery best practices, the RMAD Active Directory backup should be stored on a domain controller. At the same time, the Alternative backup path option allows you to store the same Active Directory backup on remote backup storage. This can be useful if the DC is destroyed and you want to restore it from a BMR backup and the latest Active Directory backup. The retention policy is applied to both backup paths. So, if you set it to 10, and you have both paths configured - it means that there will be 5 backups on DC and 5 backups on the remote storage. |
- To specify a separate account for the backup storage, select the Use the following account to access the backup storage option and specify account credentials.
| NOTE |
This account is used to access both backup locations. Currently, separate access accounts are not supported. |
Using the Backup Wizard
You can start the Backup Wizard by selecting the console tree root, and then clicking Create Backup on the Action menu.
On the What to Back Up page, the wizard prompts you to specify what domain controllers or AD LDS (ADAM) hosts you want to back up. You can back up specific domain controllers or all computers that are in a specific container, such as an Active Directory domain or organizational unit.
On the Where to Store Backups page, the wizard prompts you to specify the path and name format for backup files. You can type the path and name manually, click Browse to locate a folder, and use the Expression button to have the path and name include macros enabling the automatic creation of separate subfolders and files for different backups.
On the When to Back Up page, the wizard asks you whether you want to schedule the backup creation operation. You can click Now if you want to start the operation immediately. Otherwise, you click Later and configure backup scheduling. If you choose to create backups without scheduling, you can optionally have the wizard create and retain a Computer Collection for the computers and containers you have selected. Later, you may use that collection to schedule backups. If you choose to schedule backups, the wizard creates a Computer Collection for the computers and containers you have selected, and schedules a backup creation task for that collection.
On the Computer Collection Name page, you can specify a name and description for the Computer Collection to be created.
By clicking the Advanced button on the Completed the Backup Wizard window, you can display the Properties dialog box to make changes to backup options. If you do not modify those options, the defaults are used. Default options are specified using the Collection Defaults command, which appears on the Action menu when you select the Computer Collections node in the console tree.
Retrying backup creation
Recovery Manager for Active Directory allows you to retry selected backup sessions. You can retry the creation of backups for individual computers or for all computers with a particular backup creation result. Any backup session can be retried regardless of its result.
To retry a backup session
-
In the Recovery Manager Console tree, click Sessions.
-
In the details pane, click the backup session to retry, and then click Retry Backup on the Action menu.
-
In the Retry Backup dialog box, select one of the following options:
-
Computers where errors or warnings occurred. Retries backup for the computers reported with errors or warnings.
-
Computers where errors occurred. Retries backup for the computers reported with errors.
-
All computers. Retries backup for all computers in the selected session, regardless of the previous backup results.
-
-
Click OK and then click Yes.
To retry backups for individual computers
-
In the Recovery Manager Console tree, expand the Sessions node and select a session.
-
In the details pane, select computers.
-
On the Action menu, click Retry Backup.
-
Click Yes to start the backup creation.
Enabling backup encryption
Recovery Manager for Active Directory allows you to protect your backups by encrypting them. You can enable the backup encryption in the Defaults dialog box for the Computer Collections node or a Computer Collection (Computer Collection properties), as well as in the Backup Wizard.
To enable backup encryption
-
Do one of the following:
-
Right-click the Computer Collections node, and then click Collection Defaults.
-
Right-click the Computer Collection, and then click Properties.
-
Click Advanced on the Completing the Backup Wizard page.
-
-
In the Properties dialog box, click the Backup tab.
-
On the Backup tab, select the Encrypt and protect backups with password check box.
-
In the Set Password dialog box, type and confirm by retyping a password, and then click OK.
A password can contain any combination of letters, numerals, spaces, and symbols. Passwords are case sensitive, so if you vary the capitalization when you assign the password, you must type the same capitalization when entering the password. You can change the backup protection password later by clicking Set Password on the Backup tab. Write the password down and keep it in a secure place. If you lose the password, you cannot restore data from that backup since Recovery Manager for Active Directory asks you to type the password.
Active Directory backup encryption:
- Recovery Manager for Active Directory uses Microsoft's implementation of the AES 256 algorithm from RSA, Inc. (Microsoft RSA Base Provider), with the maximal (normally, 128-bit) cipher strength.
- If you specify a DC storage or UNC share for encrypted backups (DC Storage tab): A Backup Agent writes a backup directly to the storage to an encrypted temporary file. This temporary file is local or remote depending on the storage type. Data is encrypted in memory during a backup process. When the backup is done, the temporary file is renamed to the *.bkf file.
- If you specify a console storage for encrypted backups (Console Storage tab): A Backup Agent writes a backup via RPC connection to the storage on the Recovery Manager Console machine, data is encrypted in memory.
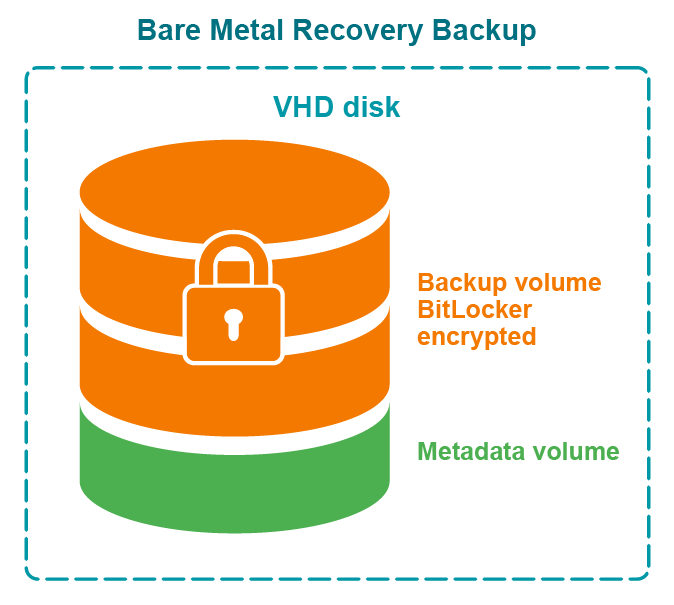
Bare Metal Recovery backup encryption:
- The specified password is used to generate a passphrase with which the backup is encrypted. The password cannot be used directly to unlock the backup container *.vhd(x) file.
- Recovery Manager for Active Directory uses a virtual hard disk encrypted with BitLocker as a container for the backup (256-bit AES encryption). Only backup volume is encrypted on the VHD disk.
- Data is encrypted in transport by the BitLocker engine on the DC being backed up.
NOTE:
-
Backup encryption does not depend on Active Directory in any way.
-
Recovery Manager for Active Directory does not send unencrypted data over the wire.
The BitLocker Drive Encryption feature should be installed on all backed up domain controllers and on the Forest Recovery Console machine to support encrypted BMR backups. But note that the BitLocker feature does not encrypt DC drives automatically.
Figure: Encrypted BMR backup
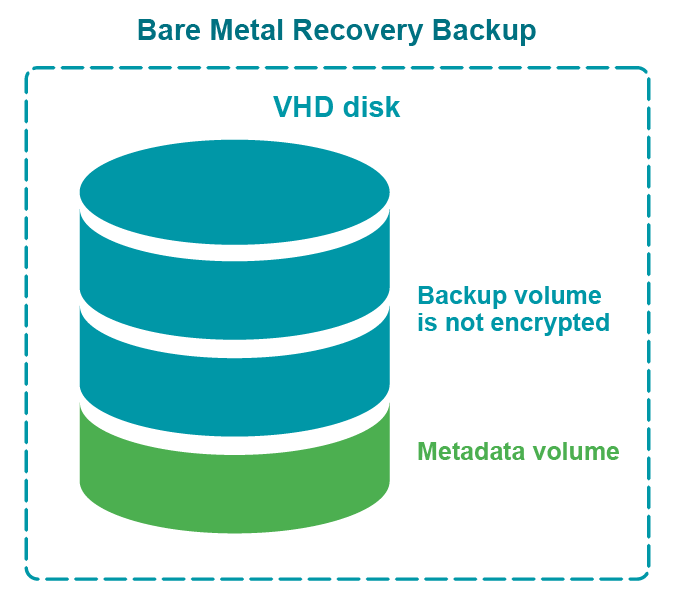
Figure: Not encrypted BMR backup