4.6 Service Account Requirements
Migrator Pro for Active Directory requires the following user account permissions and privileges to support Active Directory migrations:
-
One service account with read/write access to all organizational units (OUs) containing user, group, and computer objects in the source Active Directory to be migrated to the target environment.
-
One service account with administrative rights on the target domain(s)
-
If administrative rights cannot be granted, the service account requires the following rights:
-
The ability to create and modify user objects in the desired OUs in the target Active Directory environment.
-
Read Permissions to the configuration container in Active Directory
-
User credentials with the delegated migrateSIDHistory extended right.
-
-
-
A service account in each source and target domain with the ability to modify computer objects and add computers to the domain.
4.7 SQL Server Reporting Services (SSRS) Account Requirements
4.7 SQL Server Reporting Services (SSRS) Account Requirements
Migrator Pro for Active Directory's Reporting feature requires credentials in the following places:
-
Content credential: Credential for accessing the report server content.
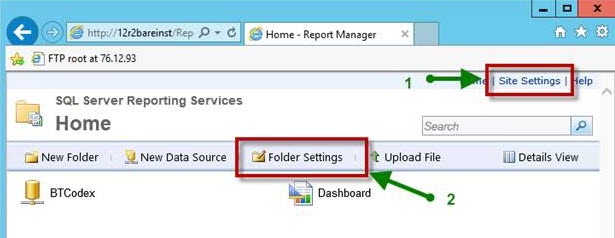
You must set the securities in two different places in the SSRS ‘Report Manager’ web interface (http://<servername>/Reports) to connect to the report server and upload reports from the installation program.
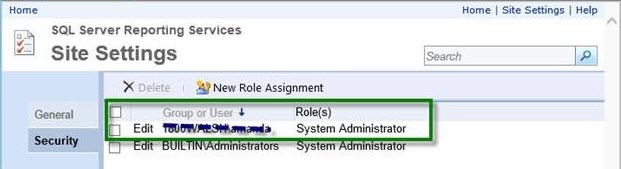
In the Site Settings, you MUST enable the ‘System Administrator’ role during installation. After installation is complete, you may change this user’s role to ‘System User’ if desired.
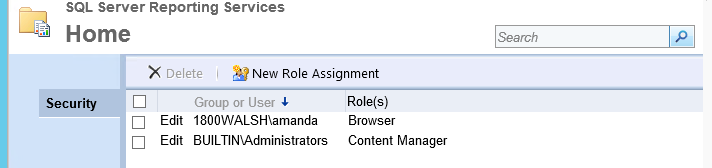
In the Folder Settings, you must add the same user with (at least) ‘Browser’ permission.
-
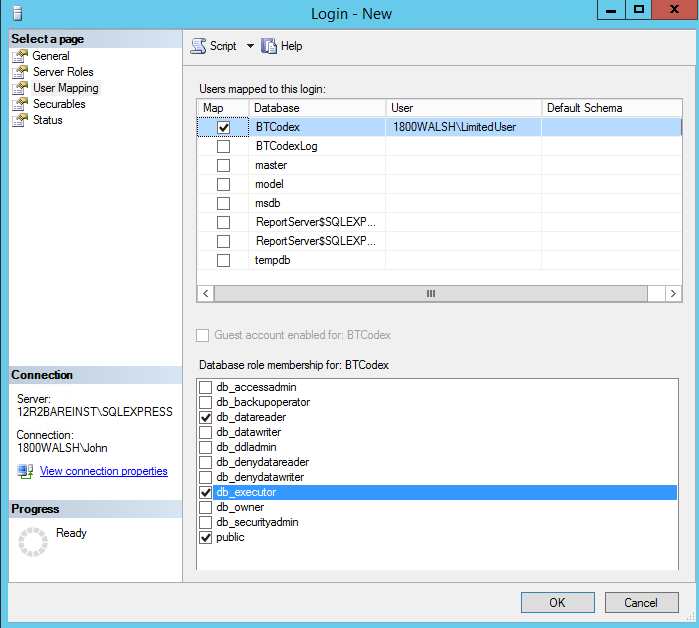
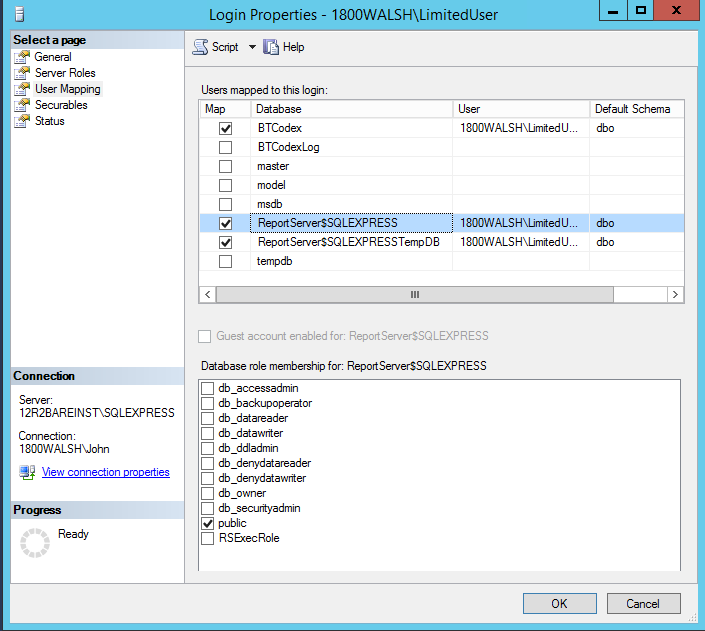
Data Source Credential: The Data Source is used to access queries in the ADM database. These credentials and roles are set in the SQL server with SSMS
The user must have public, db_reader, and db_executor roles on the ADM database.
The user must have the public role on the report server and report server temp databases.
4.8 DNS SRV Record Requirement
In each source domain, a SRV DNS record must be created to enable autodiscover for Migrator Pro for Active Directory agents.
-
To enable autodiscover when HTTPS is desired
-
Record Name: _btadm._https.SourceDomainName.Local
-
Weight and Priority: 0
-
Port Number: 443
-
-
To enable autodiscover when HTTP is desired
-
Record Name: _btadm._http.SourceDomainName.Local
-
Weight and Priority: 0
-
Port Number: 80
-
4.9 Offline Domain Join (ODJ) Requirements
In order to successfully facilitate the new Cached Credentials job (which supports the Offline Domain Join feature) a one-way external trust must be configured from the source domain to the target domain.
The devices that the ODJ process is being run on must have network connectivity to BOTH the source and target environments at the same time in order to have the Cached Credentials function work properly.
Offline domain join files must be created prior to running the Offline Domain Join process. A full explanation of Microsoft’s Djoin.exe utility and how to create these files can be found here:
https://technet.microsoft.com/en-us/library/offline-domain-join-djoin-step-by-step%28v=ws.10%29.aspx