This article was originally posted by ITNinja contributor Sven Hain. Given its continued relevance it is being included as part of the KACE knowledge base with minor modifications to meet the knowledge base standard.
Disclaimer: The following custom scripts and inventory rules are offered with no expressed or implied warranty and is to be used at your own risk. KACE does not guarantee the use of these unless designed by the KACE Professional Services team, nor does KACE guarantee the functionality or existence of these scripts and custom inventory rules in future versions of the KACE SMA.
This article is part of a series of articles to help create a Windows 10/11 inplace upgrade strategy.
This series will include the following articles:
1) KACE SMA - Windows 10 / Windows 11 inplace upgrade PreCheck - This article covers the upgrade precheck to detect upgrade issues or blocker in advance
Pre-requisites:
This precheck-script is used for Windows 10/11 inplace upgrades, similar to a detection schedule in KACE SMA Patch Management.
The prerequisite for this is that an unpacked Windows 10 or Windows 11 ISO is available on a network share. Alternatively, the unpacked ISO can also be copied to the local clients. This can be done through the KACE SMA file synchronization feature.
Find attached the custom script, report and custom inventory rule that will be used for this process. This script can be executed silently in the background on the clients. This allows you to scan the clients in advance of a build upgrade and see where you might need to take action to update software or drivers on your endpoints.
Steps to setup and run in-place pre-checks:
Instructions are written for Windows 10 upgrades but are applicable for Windows 11 as well.
After importing the script into your SMA you will find three dependencies:
Various tasks are performed in the script itself.
Among other things, it is checked whether the system has a lower Windows 10 Built version than 1903 in order to be eligible for an upgrade at all.
The log paths are then created, into which the logs from the PreCheck are stored.
In the third task the CMD file mentioned above is executed.
Note: Here you have to specify the path to your unzipped Windows 10 file. In the script this is "\\192.168.50.1\install$\WinX1903\. Authenticated users should have read permissions on this path. The second path is the log path, and this does not need to be changed.
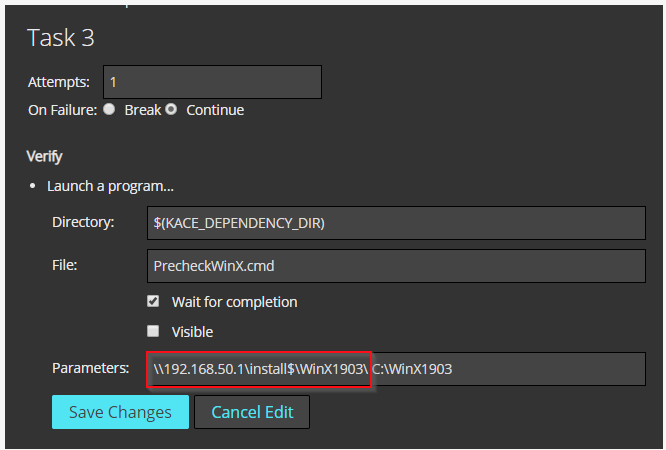
In the last task, the collected log files are packed with 7-ZIP and then uploaded to the SMA so that the log files can be accessed at any time from the SMA. In addition, the "WindowsSetupLogParser.vbs" is executed, which creates the file "WinSetupResults.log" at the end. We read this file with the imported Custom Inventory Rule so that the content is also available in the SMA.
As soon as the data is available in the SMA, a report can also be generated, which gives us a quick and easy overview of which scanned clients would successfully install the inplace upgrade or where there might still be problems.
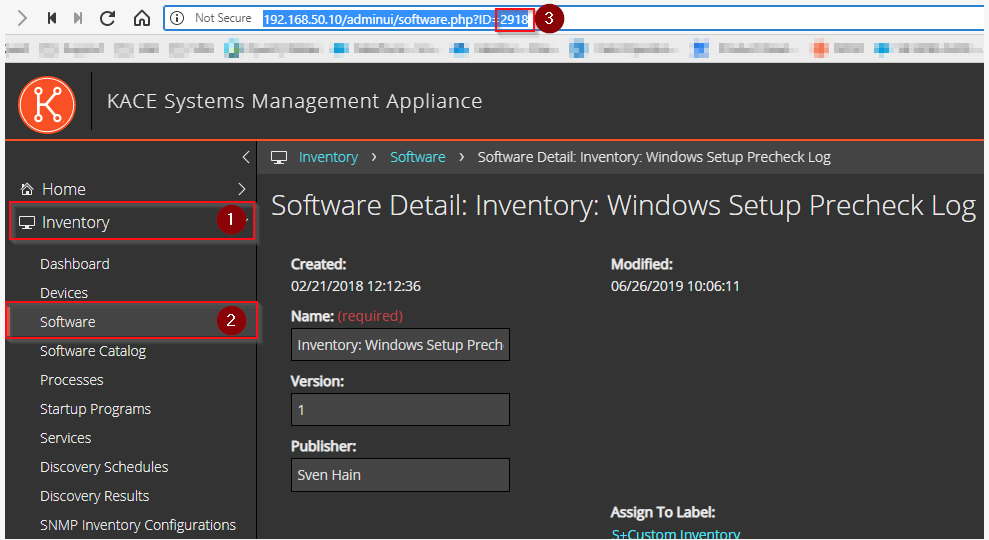
Note: The ID of the Custom Inventory Rule is stored in the report, which is probably different for you. If so you have to change the report as follows.
First you must copy the ID. Navigate to "Inventory / Software" and click on "Inventory: Windows Setup Precheck Log". Now click into the address bar of your browser and copy out the ID. It is important that you open your SMA with https://SMA/adminui, otherwise you won't see the complete address line in your browser.
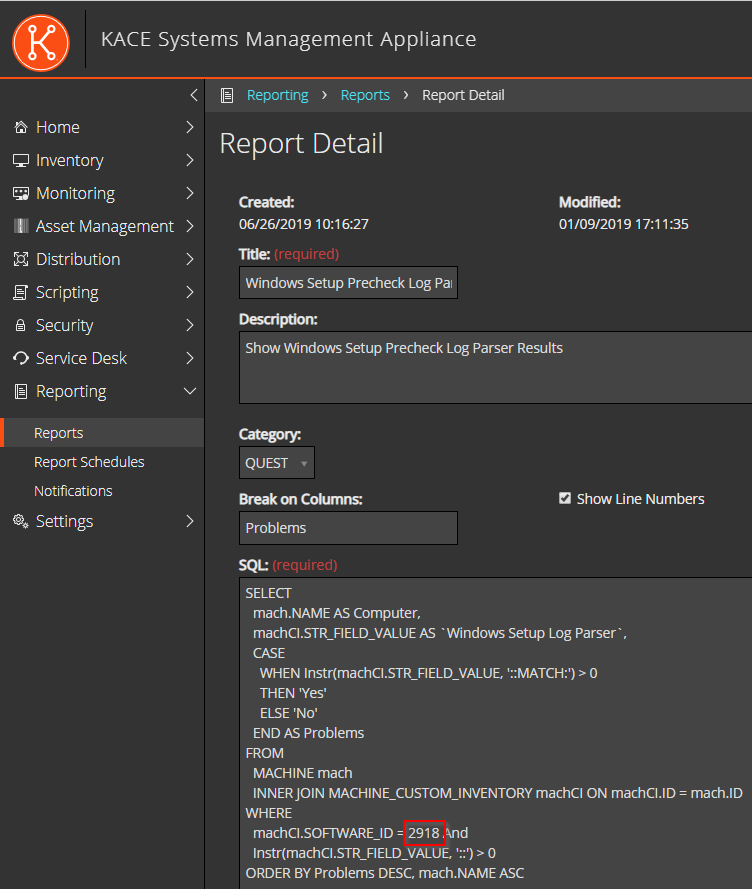
The query must then be adjusted in the "Windows Setup Precheck Log Parser Results" report. Navigate to "Reporting" and search for "Windows Setup Precheck Log Parser Results". After a click on the report, you will see the SQL Query. There you have to paste the previously copied ID.
The following is an example of the report:
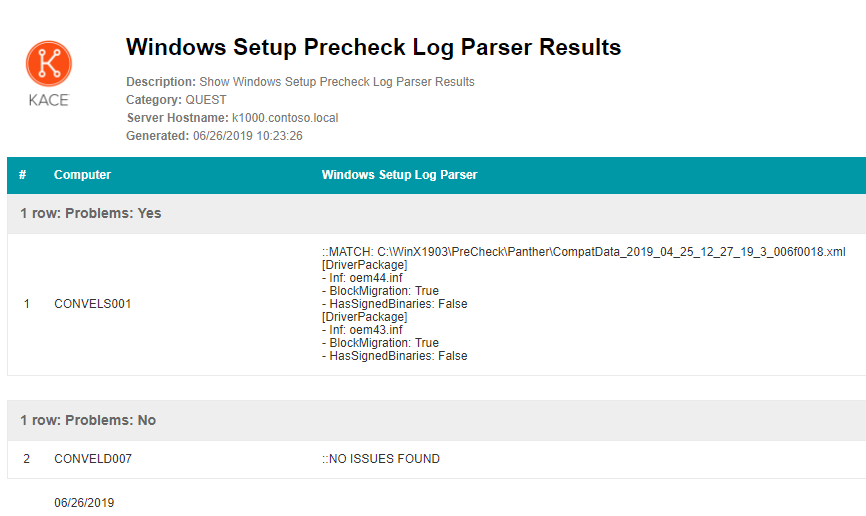
In the following two examples how the WinSetupResult.log file can look like.
::MATCH: C:\WinX1903\PreCheck\Panther\CompatData_2019_04_25_12_27_19_3_006f0018.xml
[DriverPackage]
- Inf: oem44.inf
- BlockMigration: True
- HasSignedBinaries: False
[DriverPackage]
- Inf: oem43.inf
- BlockMigration: True
- HasSignedBinaries: False
Note: With such file contents, you need to navigate to "C:\Windows\INF" to see which drivers might block an upgrade. In this example it is the "Microsoft Windows XPS Document Writer" and the "Microsoft Windows Print to PDF" driver which would not block the inplace upgrade.
::MATCH: C:\WinX1903\PreCheck\Panther\CompatData_2019_04_26_13_25_01_3_006f0018.xml
[HardwareItem]
- HardwareType: Generic
[CompatibilityInfo]
- BlockingType: Hard
- Message: Your PC has hardware that is not yet ready for this version of Windows 10. No action is required. This version of Windows 10 is automatically offered by Windows Update once the problem is resolved.
- Title: This PC cannot be upgraded to Windows 10.
[DriverPackage]
- Inf: oem1.inf
- BlockMigration: True
- HasSignedBinaries: False
[DriverPackage]
- Inf: oem0.inf
- BlockMigration: True
- HasSignedBinaries: False
::MATCH: C:\WinX1903\PreCheck\Panther\CompatData_2019_04_26_13_25_01_3_006f0018.xml
[HardwareItem]
- HardwareType: Generic
[CompatibilityInfo]
- BlockingType: Hard
- Message: Your PC has hardware that is not yet ready for this version of Windows 10. No action is required. This version of Windows 10 is automatically offered by Windows Update once the problem is resolved.
- Title: This PC cannot be upgraded to Windows 10.
[DriverPackage]
- Inf: oem1.inf
- BlockMigration: True
- HasSignedBinaries: False
[DriverPackage]
- Inf: oem0.inf
- BlockMigration: True
- HasSignedBinaries: False
There are several hardware drivers installed that are not compatible with the 1903 build, and these would need to be updated before the upgrade can be performed. However, this evaluation may also include applications that might block the upgrade. Usually antivirus programs are detected that should be updated first before the inplace upgrade is performed.