-
Title
How to configure Security Policies elements -
Description
How to configure Security Policies elements -
Resolution
The Security Policies object allows user security settings to be centrally configured. Security policies can be set for individual users or computers and is accessed via Client Configuration | Profiles | Computer/User | Security Policies.
Security Policies are registry settings. Deleting a Security Policy element will not remove the setting from the user's machine. When a Policy is enabled, it remains in effect until you specifically disable it or select the "Clear all existing security policies" option located in the General object. Once you configure the security policy to be disabled using either of these two methods, the user must log on one more time so that Desktop Authority may apply the "disabled" setting to the computer.
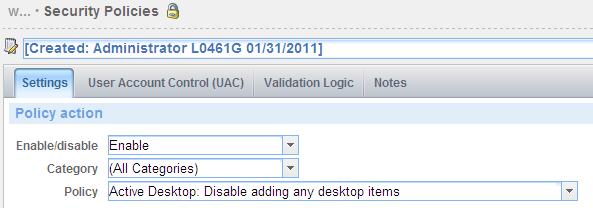
Settings
Policy action
Enable/disable: Select Enable or Disable from the list to enable or disable a security policy.
Category: Select a specific policy area from the Category list for a security policy to be set. The available categories are: (All Policies), Active Desktop, Computer, Explorer, Internet Explorer, Network, System and WinOldApp. (All Policies) will display policies for all categories. WinOldApp provides policy settings for MS-DOS applications.
Selecting a policy category will filter the policy selection list below the category.
Policy: Select a policy from the list. This list is filtered based on the policy category chosen. To see all policies, select the (All Policies) category.
User Account Control (UAC)
Select the User Account Control (UAC) tab for Security Policy settings pertaining to UAC.
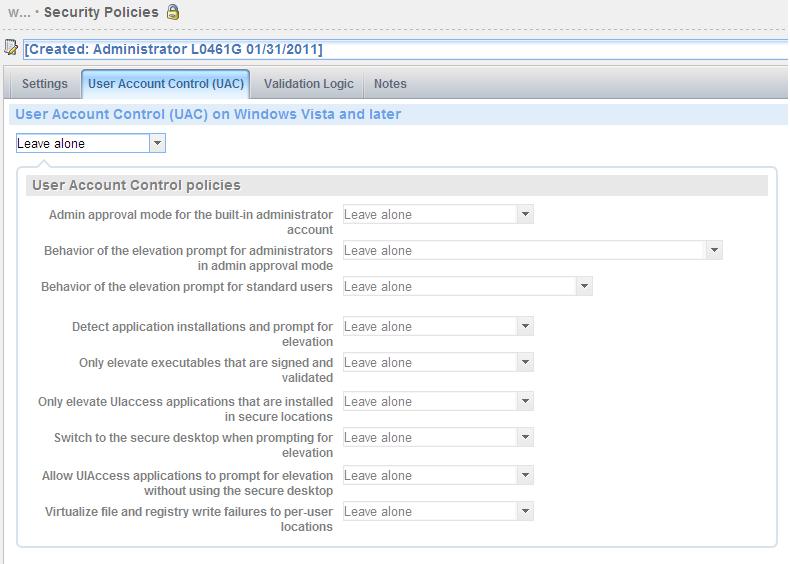
User Account Control (UAC) on Windows Vista and later
This setting determines the behavior of all UAC security policies on the target system. Select Enable from the drop list to use UAC policies throughout the target system. Select Disable from the drop list to disallow the use of UAC policies. Select Leave Alone to preserve the system's current UAC settings. By default, UAC policies are enabled on Windows Vista and later operating systems.
UAC changes on Windows Server 2008 and above may require a reboot before the change will take effect.
Windows Security Center will notify the user that the overall security of the system has been compromised if UAC security policies are disabled.
User Account Control Polices
Admin approval mode for the built-in administrator account
By default the Built-in Administrator account will run all applications with full administrative privileges. Enable this option to prompt the Built-in Administrator with the consent dialog. From this dialog the administrator can then choose to permit or deny the action. Disable this option to allow the Built-in Administrator to run all applications with full administrative privileges. Select the Leave Alone option to preserve the system's current setting.
Behavior of the elevation prompt for administrators in admin approval mode
The elevation prompt is a dialog that is used to prompt the administrator for permission to continue, or to prompt the user for credentials in order for the requested elevation of permissions to continue. This option allows the behavior of the elevation prompt to be set for administrators. Select a setting, Leave Alone, Elevate without prompting, Prompt for credentials and Prompt for consent, from the drop list.
Select the Leave Alone option to preserve the system's current setting, which by default is Prompt for Consent.
The Elevate without prompting option will allow an operation that requires permission elevation to continue with prompting for consent or credentials.
The Prompt for credentials option prompts the administrator with the elevation prompt dialog. The user is required to enter their user name and password. The request will continue with the applicable privileges. When UAC is enabled, this is the default setting.
The Prompt for consent option forces the elevation prompt dialog to pop up when there is an attempt to perform an administrative task. This dialog consists of a Permit and Deny selection. Permit will allow the operation to continue with the user's highest available privilege. The operation cannot continue if Deny is selected. This is the default selection when UAC is enabled.
The Prompt for consent from non-windows binaries (Win 7) option forces the elevation prompt dialog to pop up when there is an attempt to perform an operation for a non-Microsoft application. The user is prompted to select either Permit or Deny. If the user selects Permit, the operation continues with the user's highest available privilege. The operation cannot continue if Deny is selected.
Behavior of the elevation prompt for standard users
The elevation prompt is a dialog that is used to prompt the administrator for permission to continue, or to prompt the user for credentials in order for the requested elevation of permissions to continue. This option allows the behavior of the elevation prompt to be set for standard users. Select a setting, Leave Alone, Elevate without prompting, Prompt for credentials and Prompt for consent, from the drop list.
The Prompt for credentials option prompts the user with the elevation prompt dialog. The user is required to enter their user name and password. The request will continue with the applicable privileges.
The Automatically deny elevation requests option will return an access denied error message to the user when an operation is attempted that requires elevation of privileges.
Select the Leave Alone option to preserve the system's current setting.
Detect application installations and prompt for elevation
This setting determines the behavior of application installation. Select Enable from the drop list to pop up the elevation prompt dialog based on the configured elevation prompt behavior. Select Disable from the drop list to not trigger installer detection. Select Leave Alone to preserve the system's current settings.
Only elevate executables that are signed and validated
This setting will enforce PKI signature checks on any interactive application that requests elevation of privilege. Enterprise administrators can control the admin application allowed list through the population of certificates in the local computers Trusted Publisher Store. Select Enable to enforce the PKI certificate validation of an application before it is allowed to run. Select Disable to not enforce PKI certificate chain validation before an application is allowed to run. Select Leave Alone to preserve the system's current settings.
Only elevate UIAccess applications that are installed in secure locations
This setting will enforce the requirement that applications that request execution with a User Interface Accessibility integrity level must reside in a secure location on the file system. Select Enable to launch the application only if it resides in a secure location. Select Disable to launch the application regardless of whether it resides in a secure location or not. Select Leave Alone to preserve the system's current settings.
Switch to the secure desktop when prompting for elevation
When prompting for elevation permissions, the system can process the request on the interactive user’s desktop or on the Secure Desktop. Select Enable to process elevation requests on the secure desktop. Select Disable to process elevation requests on the interactive user’s desktop. Select Leave Alone to preserve the system's current settings. By default, this setting is Enabled on Windows Vista workstations.
Allow UIAccess applications to prompt for elevation without using the secure desktop
This setting allows User Interface Accessibility programs to not automatically disable the secure desktop for elevation prompts. Instead, the prompts will appear on the interactive user's desktop instead of the secure desktop. By default, this setting is Disabled in Windows.
Virtualize file and registry write failures to per-user locations
This setting enables the redirection of legacy application write failures to defined locations in the registry and file system. Select Enable to facilitate the runtime redirection of application write failures to a specific user location. Select Disable to allow applications that write data to protected locations to fail as they did in prior versions of Windows. Select Leave Alone to preserve the system's current settings. This is the default setting.
Validation Logic
Select the Validation Logic tab to set the validation rules for this element.
Notes
Select the Notes tab to create any additional notes needed to document the profile element.
Description
When adding or modifying a profile object element, the description appears above the settings tab. Enter a description to annotate the element. The default value for new profile elements can be changed by going to the system Preferences.
