| NOTE |
Domain controllers that are running on virtual machines in Amazon Web Services™ (AWS™) or Microsoft Azure® cannot be restored with the Bare Metal Active Directory® Recovery method because there is no way to boot such DCs from an ISO image. |
If you do not want to encrypt BMR backups, we recommend that you enable the Server Message Block (SMB) Encryption feature (SMB version 3.0 and higher ) on the network share to secure network connection. For more details on how to turn on SMB Encryption, see SMB security enhancements. Note that backed up domain controllers must support SMB Encryption as well.
The best practice is to store backups in the repository that is located in the same Active Directory® site due to faster network.
For Windows Server® 2008 R2, BMR backups that are stored on the Forest Recovery Console host are not supported.
The account that is used to access the BMR backups location must have Read and Write permissions for that location.
If the process of creating a Windows Server® 2008 R2 BMR backup completes with an error similar to "The sector size of the physical disk on which the virtual disk resides is not supported", make sure that the disk sector size on the target machine (NAS device or similar) is equal to 512 bytes. For instance, NetApp® ONTAP® operating system uses the following command: vserver cifs options modify -file-system-sector-size 512.
Active Directory® does not allow the use of a backup with an age that exceeds the Active Directory® tombstone lifetime (default is 180 days). But if there is a RMAD BMR backup that is older than 180 days and a more recent Active Directory® backup, you can successfully perform the restore operation.
When running a BMR project Verify Settings, it succeeds, but when running the actual restore task, the VMs are created, but after running for a while the VMs will blue screen and go into automatic repair mode.
This is caused by a known problem with the WinRe.wim file for Windows Server® 2019. The only workaround is to use the WinRe.wim from Windows Server® 2016.
The file can be found on the Windows Server® 2016 installation media. Load a Windows Server® 2016 distributive ISO then use the following command to mount install.wim (C:\MNT is empty folder to mount):
dism /mount-wim /wimfile:D:\sources\install.wim /index:1 /mountdir:C:\MNT /Readonly
Locate the file winre.win in C:\MNT\Windows\System32\Recovery\WinRe.wim.
Copy it to some place and unmount install.wim with:
dism /unmount-wim /mountdir:C:\MNT /discard
and unmount the distributive ISO.
When you obtain WinRe.wim copy it to the RMAD server and place it in the path:
C:\ProgramData\Quest\Recovery Manager for Active Directory\Cache\WinRe\10.0\WinRe.wim
and run your project again.
If you don't have a Windows Server® 2016 image or ISO, you may download one directly from Microsoft Evaluation Center Site.
Additional Information
The WinRe.wim file will be marked as a System and Hidden file by default so you may not be able to see this using Windows Explorer. To confirm the existence of this file, navigate to the folder described in the above and from an administrative command prompt, type in Dir -AH. This should then list files with hidden attributes to confirm the file exists and you can then copy via command prompt to the locations required.
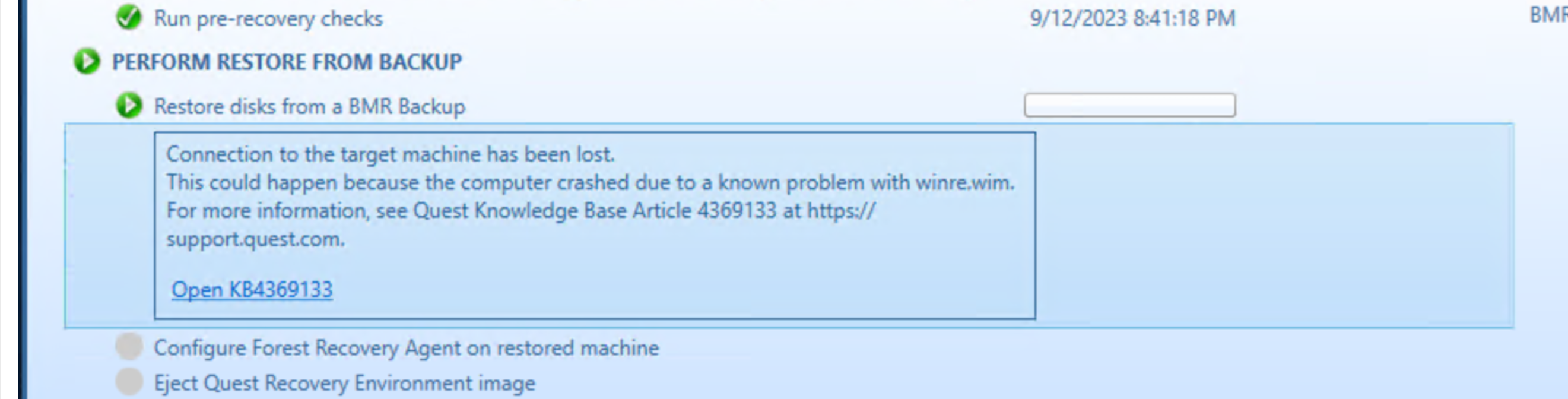
During, Perform restore from backup, if the RMAD console loses connection to the Forest Recovery Agent on the domain controller during the BMR recovery, a message will be presented and inform you to access Quest Knowledge Base article 4369133 and provides a link for more info.
The number of physical disks on the target computer must be equal to or exceed the number of critical disks on the source machine at the time the backup was created. A critical disk contains critical volumes (volumes that contain the operating system's state).
The order of system partitions must be the same on the target disk as on the source one.
The physical disks on the target computer must be of the same size as the critical disks or larger.
If a source machine with the legacy BIOS firmware has physical disks of different sizes, it is critical to have the same physical disks order on the target machine. For example, if a source has two disks - disk 0 (90 GB), disk 1 (40 GB), the target should have the same 90-40 order.
The firmware on the target computer must be compatible with the configuration of the source disks.
If the physical disks on the source computer have the GPT partition style, the target computer must have UEFI firmware and must be booted in the UEFI mode.
If the physical disks on the source computer have the MBR partition style, then the target machine should be booted in the BIOS-compatibility mode (or just legacy BIOS mode).
| Source partition style | BIOS (Target firmware) | UEFI (Target firmware) |
|---|---|---|
| GPT | Incompatible | Compatible |
| MBR | Compatible | Compatible (legacy BIOS-compatibility mode) |
It is recommended that you encrypt your Bare Metal Recovery backup by selecting the Encrypt and protect backups with password option (by default, this option is disabled) on the Backup tab in the collection properties. For details, see Creating BMR and Active Directory backups. In this case, not only the backup data stored on the remote share is encrypted, but the data transferred over the network during the backup operation is encrypted as well.
If Active Directory® backup encryption is enabled, the RMAD BMR backup will be encrypted by BitLocker. Recovery Manager for Active Directory uses a virtual hard disk encrypted by BitLocker as a container for the backup (256-bit AES encryption).
An encryption key for the backup is derived from the backup password and is not tied to a TPM chip (if any). This means that the encrypted RMAD BMR can be used on another machine, without or with another TPM chip. Only a backup password is required.
The BitLocker Drive Encryption feature should be installed on all backed up domain controllers and on the Forest Recovery Console machine to support encrypted BMR backups. But note that the BitLocker feature does not encrypt DC drives automatically. After the feature is installed, it is required to reboot the machine.
| NOTE |
After disaster recovery, volumes on the restored machine will not be BitLocker-protected. You must enable the BitLocker protection again, if required. |
To enable backup encryption, see Enabling backup encryption.
To restore the Active Directory data in case of failure, you must occasionally create a BMR backup for at least one domain controller in each domain in your environment along with the Active Directory® data backup.
What should you do?
Decide on a Backup Location For BMR backups, the best practice in an enterprise environment is to deploy a dedicated backup server performing the role of an SMB repository with high disk I/O throughput to cope with the amount of backup data. You need to specify custom access credentials for the share to access the backup data even when Active Directory® is unavailable.
Create Backups The backup schedule is defined by customer based on the available resources and desired level of protection.
Bare Metal Recovery (BMR) Backup It is recommended to prepare a BMR backup for a forest recovery because it can be restored to different hardware instances. The best practice is to create BMR backups only once a week to minimize the required storage space. Now only system critical volumes are included in a BMR backup by default. If you need to include additional volumes, see Creating BMR and Active Directory® backups.
Active Directory Backup Standard Active Directory backup includes Active Directory-specific data, e,g. Active Directory data, registry, etc. It is recommended to create Active Directory® backup daily. In case of critical failures (such as DC hardware failure or malware) it will be possible to fully restore the domain with the combination of the most recent BMR backups and latest Active Directory® Backups.
For details on how to create backups, see Creating BMR and Active Directory backups.
Recovery Manager for Active Directory (RMAD) has the option to convert a Windows Server Backup to a RMAD BMR backup. Note that а Windows Server Backup cannot be converted to an encrypted backup.
Note: Such a converted BMR backup will have some minor limitations comparing to the DRE BMR backups. DRE BMR backups have an extra metadata information about source DC, which is not a part of a native Windows Server Backup BMR backups.
To convert a Windows Server Backup and then register the resulting backup, use the following command:
PS C:\> Convert-RMADBackup \\backup_srv01\wsb\WindowsImageBackup \\backup_srv01\backups\dc1.vhdx | Add-RMADBackup
For Windows Server Backups, you have to specify the full path to the WindowsImageBackup folder.
For more details about RMAD PowerShell® Help, see the Management Shell Guide supplied with this release of the product.
In case of critical failures, the Bare Metal Active Directory® Recovery method lets you fully restore the domain with the combination of the most recent RMAD BMR backup and the latest Active Directory backup. For details about the backup creation, see Creating backups.
Standard Active Directory® backup includes Active Directory® specific data, e,g. Active Directory® data, registry, etc. It is recommended to create an Active Directory® backup daily.
To enable restore of Active Directory® data from the latest standard Active Directory® backup, select the Restore from Active Directory Backup option on the General tab. For information about all available options, see General tab.
When Recovery Manager for Active Directory recovers the network settings, it connects to the first available network adapter.
In case of NIC teaming, there are two possible scenarios:
Recovery Manager for Active Directory restores the system to the new hardware where network adapters have different MAC addresses.
In this case, Recovery Manager for Active Directory will configure some adapter with IP settings (either original or custom), and the operating system will disable NIC teaming because it will not be able to identify teamed NICs. So, the network will work with applied settings, but without teaming.
The domain controller is restored to the same server.
NIC teaming is supported in case of RMAD bare metal recovery to the same machine.