Registered forest
To register a forest, add the forest to Access Explorer. See Adding forests. When you add a forest, you must provide a service account with sufficient permissions to perform all Access Explorer configuration tasks. If the application needs to resolve a SID or expand group membership from that forest, it will use the associated service account.
When you add a managed domain and the associated Active Directory® forest is not yet registered, the Security Explorer Server will automatically add the forest and use the domain service account credentials as the forest credentials.
Managed computer
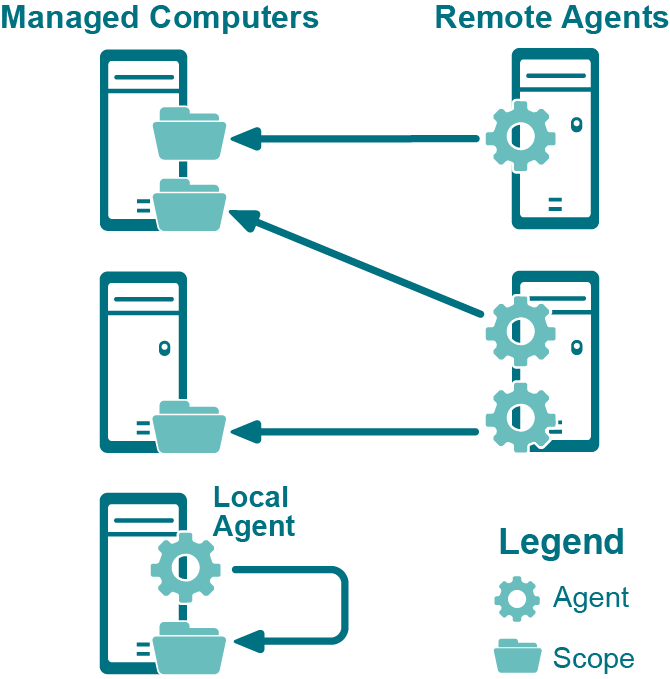
A managed computer is any network object that can host resources such as files, folders, and shares. Currently supported resources include Windows® computers, Windows® clusters, and certain network attached storage (NAS) devices. When the user adds a managed computer, Configuration Manager deploys an Access Explorer agent to scan that computer. The agent may be installed on the computer (local agent) or it may be installed on another computer (remote agent). Detailed access information is maintained on the agent computer, only sending general access information to the server.
Access Explorer agent
The indexing of only explicit permissions is done for the following reasons:
A local agent does an immediate scan as soon as it is added. Remote agents only scan according to a schedule, but if you want the agent to scan as soon as it is added you can enable the Immediately scan on agent restart or scope change option. This option is cleared by default.
Scopes
|
• |
Scopes tab of the Agent Properties. |
Figure 1 depicts the possible deployment scenarios for Access Explorer agents and managed computers in remote and local installations.