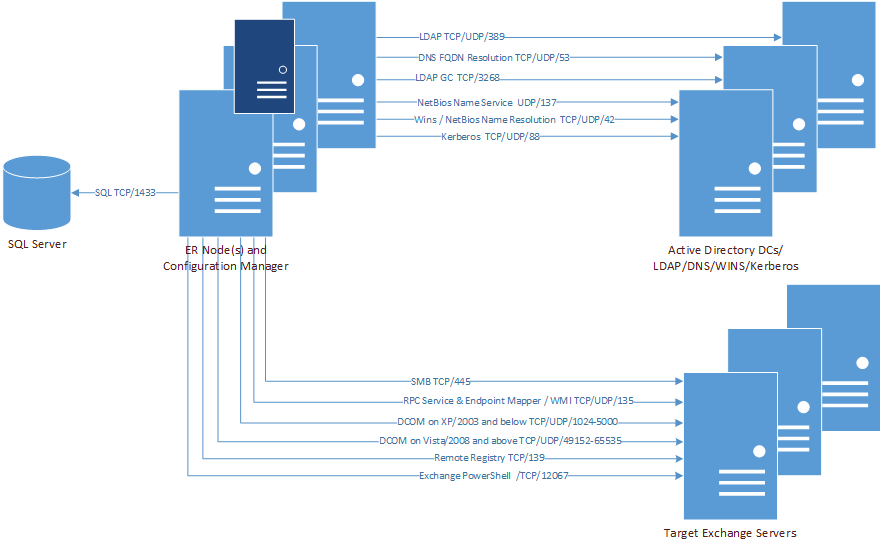
For the Enterprise Reporter components to communicate, some ports must be open.
The following figure shows the ports that are used by the various Enterprise Reporter components.
*For more information on ports used when creating a discovery, see Table 17.
**For more information on ports used during data collections, see Table 18.
The following table shows the ports used by all of the Enterprise Reporter components.
The following table outlines the ports used by all of the Enterprise Reporter discoveries.
|
X* |
|||||||||||||||
|
X* |
|||||||||||||||
|
DCOM on Vista/2008 and above |
|||||||||||||||
*Exchange 2013 and higher
The following figures outline the ports used by the Enterprise Reporter discoveries.
Additional ports for Azure and Microsoft 365 discoveries to be set on the Node:
Additional port for Exchange discovery to be set on the Node:
These ports need to be set on Active Roles server and Enterprise Reporter server:
|
Start | Control Panel | System and Security | Windows Defender Firewall Scroll down and select Allow an app or feature through Windows Defender Firewall Select File and Print Sharing and Windows Management Instrumentation (WMI) (if not already selected) The check box in the Domain column will be selected. Click OK.. | |
|
Start | Control Panel | System and Security | Windows Defender Firewall Scroll down and select Allow an app through Windows Firewall Select Windows Management Instrumentation (WMI) and File and Print Sharing (if not already selected) The check box in the Domain column will be selected. Click OK. | |
|
Start | Control Panel |System and Security Select Allow an app through Windows Firewall Select Windows Management Instrumentation (WMI) and File and Print Sharing The check box in the Domain column will be selected. Click OK. | |
|
Start | Control Panel | System and Security Select Allow an app through Windows Firewall. Select Windows Management Instrumentation (WMI). Click OK. | |
|
Start | Control Panel | System and Security | Windows Firewall. Select Allow a program or feature through Windows Firewall. Select Windows Management Instrumentation (WMI). Click OK. | |
|
Start | Control Panel | Windows Firewall. Select Allow a program through Windows Firewall. Select the Exceptions tab. Scroll down and select Windows Management Instrumentation (WMI) and click OK. | |
|
In the center on the Task Bar, select Search and type Windows Defender Firewall Select Allow a program or feature through Windows Firewall. Select File and Printer Sharing and Windows Management Instrumentation (WMI). The checkbox in the Domain column will be selected. Click OK. Start the Remote Registry service and set it to Automatic. This step is required to collect data such as installed software, event logs, and security policies. | |
|
In the lower left hand corned of the screen right click and select Control Panel. Select System and Security | Windows Firewall. Select Allow a program or feature through Windows Firewall. Select File and Printer Sharing and Windows Management Instrumentation (WMI). Click OK. Start the Remote Registry service and set it to Automatic. | |
|
Start | Control Panel | System and Security | Windows Firewall. Select Allow a program or feature through Windows Firewall. Select File and Printer Sharing and Windows Management Instrumentation (WMI). Click OK. Start the Remote Registry service and set it to Automatic. | |
|
Start | Control Panel | Security | Windows Firewall. Select Allow a program or feature through Windows Firewall. Select the Exceptions tab. Select File and Printer Sharing and Windows Management Instrumentation (WMI). Click OK. | |
|
Start | Control Panel | Security Center| Windows Firewall. Select the Exceptions tab. Select File and Printer Sharing. Click OK. |
The Enterprise Reporter server requires a database to store configuration specifications and the information that will be collected from your network environment. Before you install Enterprise Reporter, determine where you will set up your database. It should reside on a SQL Server® that is accessible from the computer running the Enterprise Reporter server. For more information, see SQL Server supported versions .
|
• |
|
• |
The simplest way to configure the database is to allow Enterprise Reporter to set up the database following installation. You need to know the SQL Server® on which you want to create the database, and you can use either Windows® or SQL Server® credentials to connect to your SQL Server®.
|
NOTE: In order to create the database, the currently logged in account must have appropriate rights (including SysAdmin rights) on the SQL Server®, or you must use appropriate SQL credentials.
|
|
• |
|
• |
There are parameters that you can set when creating an Enterprise Reporter database:
These groups provide access to the appropriate tables in the Enterprise Reporter database and are used to allow Windows authentication on the SQL Server. For more information, see Security Groups in Enterprise Reporter .
A corresponding SQL login and role is created for each group.
|
• |