The Quest® Rapid Recovery team works diligently to respond to customer feedback and make continual improvements to the product. With that goal in mind, the following changes have been implemented for release 6.3 related to Command Line Management utility (cmdutil.exe), Rapid Recovery PowerShell module, and sample scripts.
The following Rapid Recovery Command Line Management utility (cmdutil) commands have been added to this release:
The following Rapid Recovery PowerShell module cmdlets have been added to this release:
The following changes have been made to this document:
The following information is deprecated.
Rapid Recovery consists of several software components. Key components relevant to this topic include the following:
Figure 1: Rapid Recovery Command Line Management provides command line functions
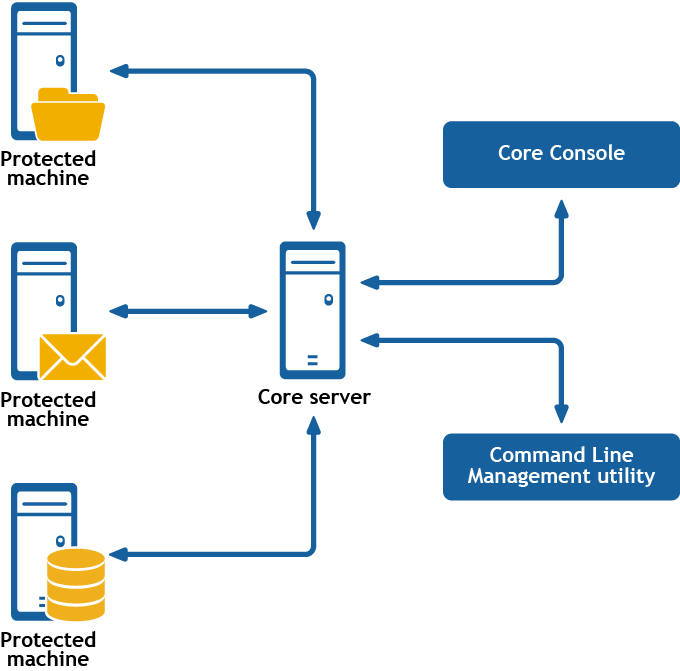
Rapid Recovery Command Line Management is a Windows command line utility that lets users interact with the Rapid Recovery Core server. It offers some of the same functions that the Rapid Recovery Core Console graphic user interface provides. For example, Rapid Recovery Command Line Management utility can mount recovery points or force a snapshot.
The Rapid Recovery Command Line Management utility is embedded in every installation of the Rapid Recovery Core. To open the Command Line Management utility for a default installation, open the Command Prompt (right-click and select the Run as Administrator option), and then change the directory to the path C:\Program Files\AppRecovery\Core\CoreService\, which is the location of the cmdutil.exe file. From this directory, you can pass action flags to the Rapid Recovery Command Line Management utility through a selection of command options and qualifiers to perform limited management functions.
To run any cmdutil command in the module, at the command prompt, type the command cmdutil followed by a space; then type a slash (/) followed immediately by the command name (do not include a space). Identify each parameter or command option by preceding it with a hyphen or dash, followed by the command option. Include a space before any input to the command option. When using two or more command options, include a space after each option and input pair. Again precede the option name with a hyphen and a space before any input. After typing the command, press [Enter] to run the command.
Each command includes examples to model the syntax. In these examples, the command prompt is designated by the right angle bracket, >. Thus, command structure is as follows:
>cmdutil /[command name] -parameter1 p1_input -parameter2 p2_input
Examples:
To open an existing DVM repository on the local machine, type the following command and press [Enter]:
>cmdutil /opendvmrepository -localpath E:\Repository
To create a new account in the Credentials Vault, type the following command and press [Enter]:
>cmdutil /credentialsvaultaccount -add -accountusername admin -accountpassword password -description "Admin credentials"
This section describes the commands and options available for the Rapid Recovery Command Line Management utility.
The addencryptionkeytoprotectedmachine command lets you apply an existing encryption key to a machine that the Core is protecting.
The usage for the command is as follows:
/addencryptionkeytoprotectedmachine -core [host name] -user [user name] -password [password name] -name [encryption key name] -comment [comment or description of key]
The following table describes the options available for the addencryptionkeytoprotectedmachine command:
| Option | Description | ||
|---|---|---|---|
-? |
Display this help message. | ||
-core |
Optional. Remote Core host machine IP address (with an optional port number). By default, the connection is made to the Core installed on the local machine. | ||
-user |
Ocmdptional. The user name for the remote Core host machine. If you specify a user name, you must also provide a password. If none is provided, then the credentials for the logged-on user are used. | ||
-password |
Optional. The password to the remote Core host machine. If you specify a password, you also have to provide a user name. If none is provided, then the credentials for the logged-on user are used. | ||
| -protectedserver | The name or IP address of the protected machine. | ||
-keyname |
Optional. The name of the encryption key. Specify this option if you know the name of the encryption key that you want to set for the protected machine.
|
Apply an existing encryption key to a protected machine. If you want to disassociate the key from the protected machine, then select <none> or specify the <none> value for the -keyname option:
>cmdutil /addencryptionkeytoprotectedmachine -protectedserver 10.10.8.150 -keyname EKname