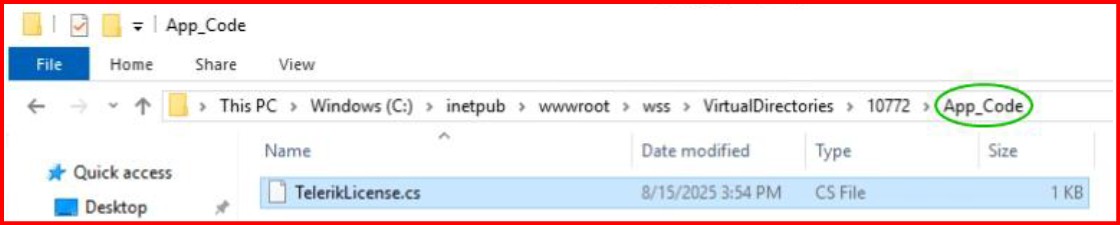
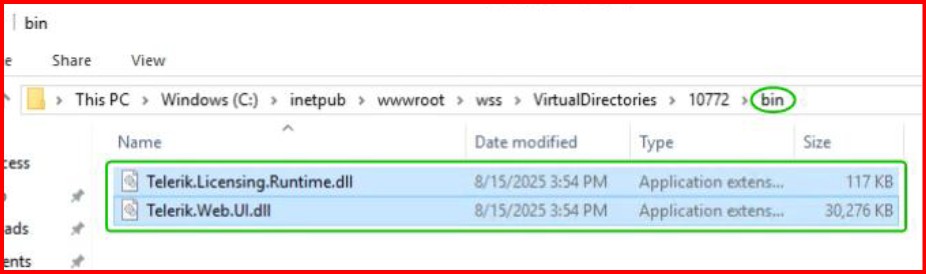
Cyber Vulnerability: CVE 2025 3600 with Telerik.Web.UI.dll
Cyber Vulnerability Published May 2025 - CVE-2025-3600
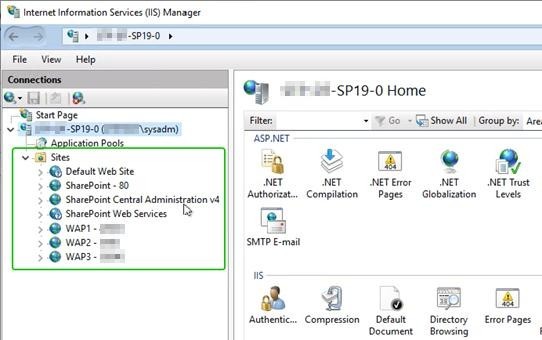
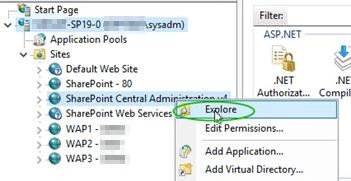
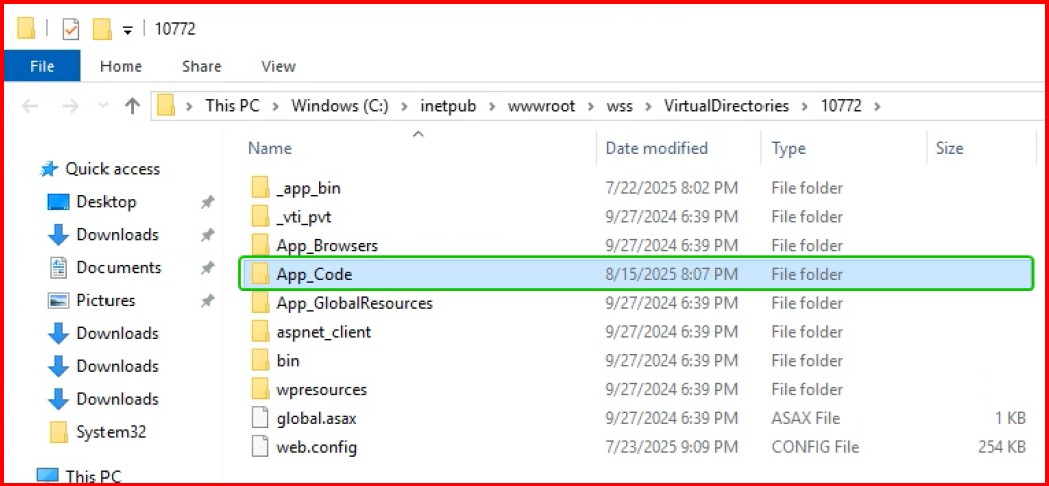
Workaround steps to mitigate with Cyber Vulnerability: CVE 2025 3600
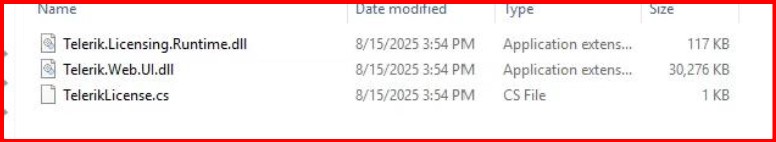
| # Prompt for the DLL folder path $dllPath = Read-Host "Enter the path where the Telerik DLL files are located, without quotes" # Get all DLL files in the folder $dllFiles = Get-ChildItem -Path $dllPath -Filter "*.dll" # Function to extract assembly redirect info function Get-AssemblyRedirect { param ($dll) $assembly = [System.Reflection.AssemblyName]::GetAssemblyName($dll.FullName) $name = $assembly.Name $version = $assembly.Version.ToString() $publicKeyTokenBytes = $assembly.GetPublicKeyToken() $publicKeyToken = ($publicKeyTokenBytes | ForEach-Object { $_.ToString("x2") }) -join "" return @" <dependentAssembly> <assemblyIdentity name="$name" publicKeyToken="$publicKeyToken" culture="neutral" /> <bindingRedirect oldVersion="0.0.0.0-$version" newVersion="$version" /> </dependentAssembly> "@ } # Generate XML content $redirects = foreach ($dll in $dllFiles) { Get-AssemblyRedirect -dll $dll } # Display the result for copy-pasting Write-Host "`nPaste this inside the <assemblyBinding> node in your web.config:`n" $redirects |
| <dependentAssembly> <assemblyIdentity name="Telerik.Licensing.Runtime" publicKeyToken="xxxxxxxxxxxxxxxx" culture="neutral" /> <bindingRedirect oldVersion="0.0.0.0-1.6.5.0" newVersion="1.6.5.0" /> </dependentAssembly> <dependentAssembly> <assemblyIdentity name="Telerik.Web.UI" publicKeyToken="xxxxxxxxxxxxxxxx" culture="neutral" /> <bindingRedirect oldVersion="0.0.0.0-2025.2.528.462" newVersion="2025.2.528.462" /> </dependentAssembly> |
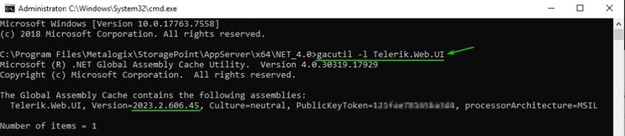
<StoragePoint installation path>\AppServer\x64\NET_4.0\gacutil -l Telerik.Web.UI Sample output
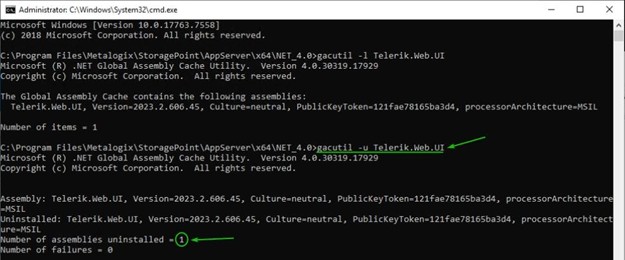
gacutil -u Telerik.Web.UI Sample output
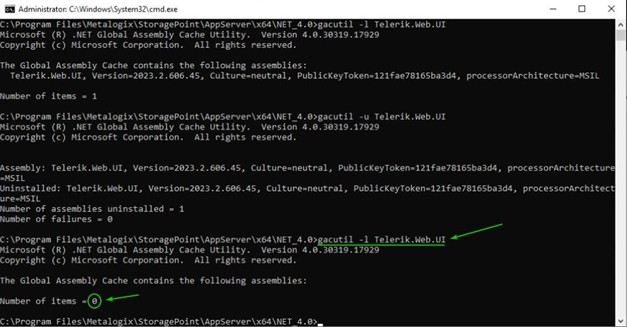
C:\Program Files\Metalogix\StoragePoint\AppServer\x64\ 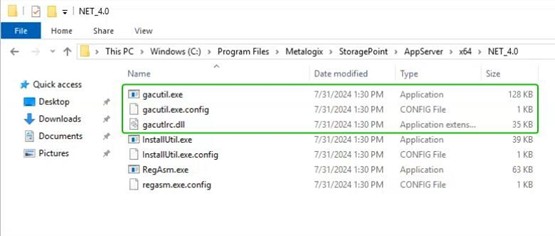
iisreset
net stop sptimerv4
net start sptimerv4