Using adcorgpwd.exe to enable FIPS compliant algorithms
adcorgpwd.exe -e
OR
adcorgpwd.exe -enablefips
|
|
Note: If adcorgpwd.exeis not used with the options as mentioned above, the product may still use some non-FIPS compliant algorithms. |
The following section describes the necessary steps you need to take after upgrade.
Run InTrustFIPSMigratorTool.exe
Go to C:\Program Files (x86)\Quest\InTrust\Server\ADC\SupportTools folder.
Run InTrustFIPSMigratorTool.exe tool (refer page number 15 of this guide and follow the steps from 2 to 7).
Update Server ID
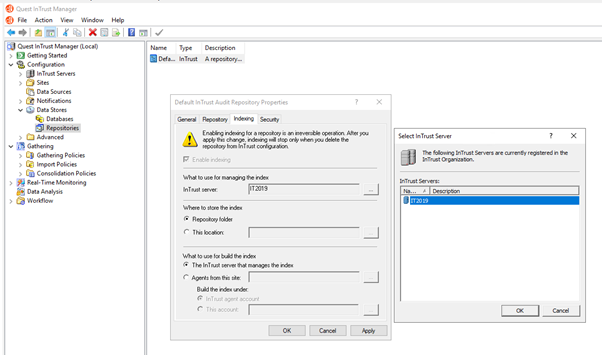
In Quest InTrust Manager | Configuration | Data Stores | Repositories, right-click on all repositories name individually and select Properties.
On the Indexing tab, select InTrust Server and click OK (Attached screenshot for reference)
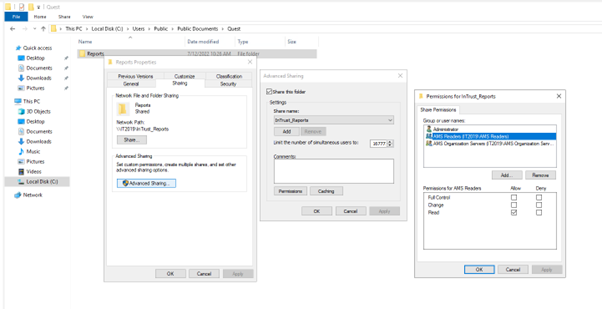
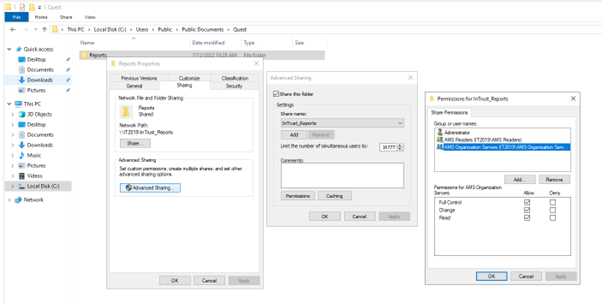
Network Access for InTrust_Reports.
Go to C:\Users\Public\Documents\Quest folder
Right click on Reports folder & go to properties
On sharing tab, Click on Advanced Sharing
Click on Permissions -> Add
<Server Name>\AMS Readers & <Server Name>\AMS Organization Servers
After installing the 11.6.1 version, please follow the below-mentioned steps to enable FIPS manually.
Using adcorgpwd.exe to enable FIPS compliant algorithms
Run adcorgpwd.exe (Default location: C:\Program Files (x86)\Quest\InTrust\Server\ADC\SupportTools) using below command:
adcorgpwd.exe -e
OR
adcorgpwd.exe -enablefips
|
|
Note: If adcorgpwd.exe is not used with the options as mentioned above, the product may still use some non-FIPS compliant algorithms. Once FIPS compliant algorithms are enabled, they will remain enabled and cannot be changed back to non-FIPS algorithms. The Intrust Server and agents are updated to use FIPS approved algorithms and hence if we are adding 11.6.1 server in existing organization with agents and server with 11.4 or below, the communication and authentication cannot succeed.. |
Restart the machine.
The following topics describe some differences you may find in InTrust after the upgrade.
A new event forwarding engine was introduced in InTrust 11.4. As a result, the following organization parameters fell out of use:
Even though they are still visible in the organization parameter editor, they have no effect in InTrust 11.4 and later.
In InTrust 11.3.2, the rule group tree was reorganized to put all attack detection rules in an easy-to-locate dedicated group. The upgrade doesn't reconfigure any existing real-time monitoring policies, so if you want to use the rules at their new locations, you need to edit the policies that reference the old rules. Otherwise, the policies will keep applying the rules at their old locations.
This utility migrates InTrust Task and Job details from previous version to 11.6.
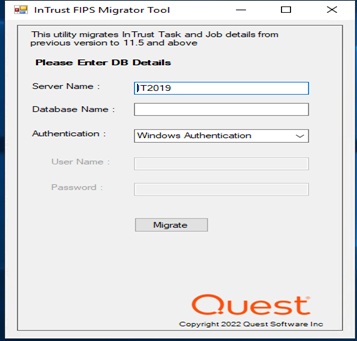
|
Note:If Always on high availability feature is used, enter the Listener name in Server Name field. |
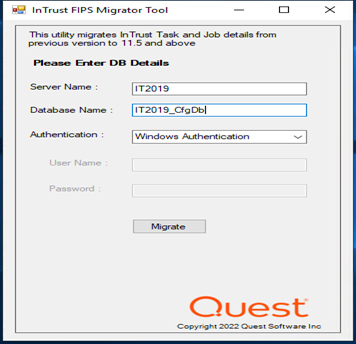
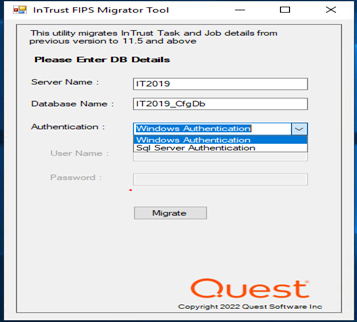
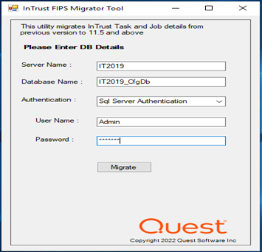
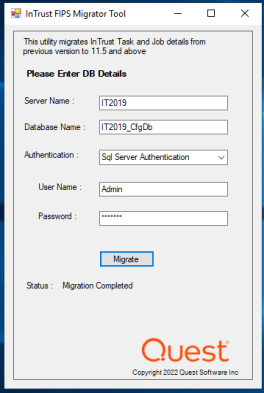
The Migration is successfully completed.
If configuration database replication over a WAN link is configured in your InTrust deployment, you need to take a few additional configuration steps. To follow this procedure, you should have the Replication of the InTrust Configuration Database document handy. For details about any steps, see the Technical Details and Procedures topic in that document.
These errors can be safely ignored.