The Duplicate Site Security action lets you to copy the security settings (users, groups, and permissions) of a SharePoint site to one or more other sites within the same farm. This may be useful, for example, if you have created one or more new SharePoint sites and want them to have the same users, groups, and permissions as an existing site.
You also have the option of backing up destination site permissions before the Duplicate Site Security action is carried out.
In a multi-farm environment, site security can be duplicated within a single farm; either the home farm or a remote farm.
Factors to Consider before Duplicating Site Security
·Duplicate Site Security is a one-time action. Any ongoing changes to permissions on the source site will not be replicated to the destination site(s). You can, however, schedule the action to run on a recurring basis.
·The action will replace the list of users with direct permissions on a destination site with that of the source site.
·Any permissions level referenced in the source site that does not exist in the destination site collection will be created there as a custom permissions level (even if it exists as a SharePoint default permission level in the source site collection). If custom permissions levels with the same name but different definitions exist in both locations, you can choose whether or not to overwrite the definitions in the destination site collection.
·If you duplicate security to a site that inherits permissions from its parent, that inheritance will be broken and it will become a site with unique permissions that have been copied from the source. Conversely, if you duplicate security to a parent site, child objects with inherited permissions will inherit the new permissions that have been copied from the source.
·You have the option of duplicating permissions (and breaking any existing inheritance) to target lists with identical names (for example, Calendar to Calendar; Shared Documents to Shared Documents). You cannot, however, duplicate permissions of list items.
·Any list with unique permissions on the destination site that does not exist in the source site will remain intact.
How "Matching" Groups Are Handled
SharePoint groups that include the name of the source site (such as Owners, Members, and Visitors) will be matched to equivalent groups on the destination site, using the destination site name. (For example, Source Owners will be matched to Target Owners and so on.) Whenever a "matching" group already exists on the destination site, the action can:
·add members of the source group to the target group, if they are not already there
OR
·replace members of the target group with members of the source group
OR
·leave the target group membership unchanged.
If a group on the destination site has a matching name but the permissions level is different, ControlPoint will replace the permissions level of the destination group with that of the source group.
Other group settings, including Group Owner, will not be changed.
If a matching group is not found at the destination:
It will be createdusing the name of the destination siteand the membership will be copied from the source. Additional settings will be handled as described in the following table.
|
Setting |
Action That Will be Taken |
|---|---|
|
Group Owner |
ControlPoint will attempt to use the group ownerwhich may be either an individual or another SharePoint groupfrom the source site (provided that owner already exists on the destination site). If the owner does not exist at the definition, the ControlPoint user who is performing the action will become the group owner. |
|
Other group settings |
the SharePoint default values will be used (regardless of whether they match the settings for the source group). |
To duplicate site security:
1In the SharePoint Hierarchy, select the site whose security you want to duplicate.
NOTE: This action is only available at the site level.
2Right-click and choose Users and Security > Duplicate Site Security.
3If you want to back up permissions on the destination site(s) before performing the duplicate action, check the Backup site permissions before duplicating box.
NOTE: If you check this box and encounter issues with the operation, you can restore permissions from the backup using the procedure for Restoring Site Permissions from a Backup.
4If you want custom permissions level definitions from the source to replace any in the destination site collection that have the same name, leave the Replace custom permission level definition if it is not the same in the target box checked.
NOTE: If you uncheck this box, existing custom permissions level definitions will not be changed.
5If you want permissions of source site lists to be carried over to destination site lists of the same name, leave the Duplicate permissions on lists with matching names checked.
NOTE: If you uncheck this box, permissions for lists with matching names will not be changed.
6Specify how you want the action to proceed When a matching group name is encountered:
§Add members from source site if they are not already in target site
OR
§Replace members with members from source site
OR
§Leave existing group membership as is
7From the Available Items list, select the site(s) to which you want permissions duplicated and move them to the Selected Items list.
8When you have finished selecting sites, click [Apply]
Now you can:
·run the operation immediately (by clicking the [Run Now] button)
OR
·schedule the operation to run at a later time or on a recurring basis.
OR
·save the operation as XML Instructions that can be run at a later time.
If you chose the Run Now, option, after the operation has been processed:
·a confirmation message displays at the top of the page, and
·a ControlPoint Task Audit is generated for the operation and displays in the Results section.
If you schedule the operation, a link to the Task Audit is included in the scheduled action notification email.
See also The ControlPoint Task Audit.
ControlPoint offers several advanced tools for analyzing data in the SharePoint environment, including:
·a summary of components and statistics at different levels of the SharePoint Hierarchy
·activity throughout the SharePoint farm
·storage used by various SharePoint objects
·site content
·information about users, including:
§permissions for Web applications, site collections, sites, and pages, and
§"orphaned" users, which are users who have permissions within SharePoint but are no longer listed in the Active Directory
·trends over a specified time period
·the contents of SharePoint audit and change logs.
An additional tool, the ControlPoint Task Audit, enable you to review ControlPoint actions taken by administrators.
Analysis tools are accessible for various levels of the hierarchy. As with other ControlPoint features, the scope of the analysis is determined by the hierarchical context.
Most analyses can also be configured so that they can be invoked directly from a url, which can be bookmarked, emailed, or placed on a SharePoint site.
NOTE: This chapter describes all of the ControlPoint analysis tools. Depending on the configuration of your ControlPoint menus, however, the analysis tools to which you have access, and their location in the menus invoked from the left navigation pane, may vary.
You can also create dashboards for monitoring key statistics within your farm.
When you select a ControlPoint analysis tool from the left navigation pane, you are prompted to specify the parameters you want to use. The most common parameters used in various ControlPoint analysis tools are described below.
Note that, depending on the analysis, some parameters may be located in the Advanced Parameters section.
Cached vs. Real-time Data
Some ControlPoint analyses give you the option of using either cached or real-time data for analyses performed on the farm, one or more Web applications, or site collections.
If the Use cached data box is checked, your analysis will include data that has been collected by ControlPoint during the last run of Discovery . The advantage of using cached data is that the analysis will be processed more quickly and will not compete for system resources. Because Discovery is run on a nightly basis, the use of cached data is often sufficient, especially when the analysis contains data that is not likely to change significantly over the course of a day.
The advantage of using real-time data (when the Use cached data box is unchecked) is that your analysis will contain the most current information. However, because the data is being captured in real time, the analysis will take longer to process and may tie up system resources.
IMPORTANT: For analyses performed on a single site collection or site, real-time data is always used and the Use cached data option is disabled. Because data collection within a single site collection or site is less time-consuming, the impact on system resources is minimal.
Specific Date or Time Period
For analyses that cover a specific time period, you select the time period by specifying a Start Date and End Date.
For analyses that involve activity, only cached data is used, since these analyses are based on accumulated summary data collected nightly by SharePoint usage analysis jobs.
For analyses involving other types of data (such as site collection storage) you are given the option of using real-time data.
IMPORTANT: Historical data that predates the ControlPoint cache will not be reflected in analysis results. For example, if the ControlPoint cache was created two weeks ago, a maximum of two weeks-worth of data is available for analysis, regardless of the date range you specify. Similarly, any historical data that postdates the last run of ControlPoint Discovery will not be reflected in results. For example, if you request data for a time period that covers the last 30 days and the last time Discovery ran was 10 days ago, analysis results will reflect the time period up to the last Discovery run date.
The format that ControlPoint uses to display dates is based on browser settings (rather than server settings). If you want to change the format (from mm/dd/yy to dd/mm/yy for example), go to Internet Options and change the Language Preference.
It is worth noting that deleted sites will display in activity and storage analysis results if they were active during the specified time period.
Open drill-down Options
For analyses that allow you to drill down to a more detailed ControlPoint analysis, you can choose to display it in a separate window by checking the Open drill-downs in new window box.
If you leave this box unchecked, the analysis to which you are drilling down will display in the current workspace, and parameters from the original analysis will be carried over. You can return to the original analysis by clicking the Back arrow in the report header.
Note that, when you link to a SharePoint page from analysis results, it always displays in a separate window.
Expanded Results Option
For most analyses that contain nested data, you have the option of choosing whether or not you want to display results expanded.
If you want to display results at the highest level of detail, uncheck the Display with results expanded box. You can then expand items individually, and view, print, or export additional detail for selected items only.
If your analysis contains a lot of nested data and you want to view, search, print, or export all of the analysis detail without drilling down, you may choose to have results display fully expanded by checking the Display with results expanded box .
TIP: If you choose to display expanded results and your analysis contains a large amount of data, you can use the Document Map to more easily navigate through results. See Analysis Results Display.
Additional Parameters for Permissions Analyses
The following parameters are specific to SharePoint user permissions analyses:
·If you want to limit results to one or more specific users, the Select users field allows you to select the users you want to include in your analysis. If you leave this field blank, all users will be included.
NOTE: You must use real-time (not cached) data if you are selecting users based on a SharePoint User Profile Property.
·If the scope of your analysis includes sites with multiple child objects, you can choose to display all objects (including those whose permissions are inherited) by unchecking the Show Unique Permissions Only box.
NOTE: If this option is checked, only sites with unique (non-inherited) permissions will be included in the results.
·If you want results to include only users who have direct permissions (that is, do not have permissions via a SharePoint group), check the Include only users with Direct permissions box.
TIP: You can use this option to identify "rogue users" who should have permissions through membership in a SharePoint group, then initiate an Add User to Groups action directly from analysis results. See Acting on Search or Data Analysis Results.
·If your selection includes Active Directory groups and you are running the analysis using real-time data:
§ You can include separate line items for users who have permissions through those groups by checking the Include users with AD group membership box.
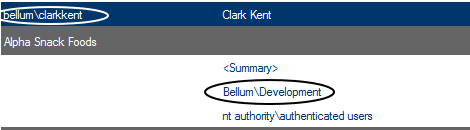
If you leave this box unchecked, only the permissions of the AD group itself (not the users within it) will be included in analysis results.
§You can include a summary section at the end of the analysis that lists the Active Directory groups within the scope of your analysis along with all of their members by checking the Include AD Group Members table box.
NOTE: You cannot display membership in Active Directory groups if you are running the analysis on cached data (and the checkbox will be disabled). If the ControlPoint Application Administrator has configured the application to prevent members of Active Directory groups from being displayed, this option will not be visible. Built-in groups (such as authenticated users) are not counted.
·If you want to limit results to one or more specific permissions levels, select them from the Limit to Users with permissions level(s) list box. (All built-in and custom permissions levels that are currently assigned to at least one user on at least one site within the scope of your analysis display in the this box.)
If the analyses includes lists and/or items, permissions levels that are assigned to a list/item that are not assigned at the site level will not display in the list box. (The list box is populated by data collected by the ControlPoint Discovery process, which does not go below the site level.) A list- or item-level permissions level can, however, be entered in the Limit by Other Levels field.

·If you want results to include only sites for which anonymous access is allowed, check the Show Anonymous Access Only box.

·If you want a cumulative total of unique users who have permissions for objects within the selected scope, check the Calculate Total Users with Permissions box.
Total Users with Permissions includes:
§Web application Service Accounts
§Users granted permissions through Web application policies
§Site Collection Administrators
§Users within Active Directory groups to which the ControlPoint Service Account has access (that is, within the same domain or forest or in a different domain/forest for which with a two-way trust exists). Disabled Active Directory accounts are included in this total. If an Active Directory user has been renamed but still has permissions in SharePoint under the old name, each name will be counted as a separate user.
Excluded from this total are built-in groups and special accounts, such as nt authority\authenticated users (or any account that begins with "nt authority") and sharepoint\system, and users granted permissions via augmented Claims or alternate authentication providers.
NOTE: If you choose to run the analysis using cached data, Total Users with Permissions uses data recorded in the ControlPoint Administration Database (xcadmin), and is current as of the last Discovery run. (The actual number of users within Active Directory groups are always counted in real-time, however.) If you run the analysis using real-time data, all users are counted in real time, which may significantly increase the amount of time it takes to run the analysis.
All ControlPoint analysis results displays include a standard header and footer, in addition to analysis-specific detail.
Analysis Results Toolbar
ControlPoint analysis results pages include a toolbar which contains page navigation, export, and print capabilities.
Above the toolbar are links that enable you to:
·select all objects in analysis results to include in a ControlPoint operation
·download results as a CSV file
Analysis Results Detail
The analysis results detail sections contains summary information, followed by the analysis-specific content.
The summary section includes the parameters used, as well as the name of the user who ran the analysis and the run date and time.
Note that, if the analysis was run using cached data, the date and time that the cache was last refreshed via ControlPoint Discovery displays. The information in the analysis is current as of that date and time. If the analysis was run on real-time data, the Cached field will be populated by the value "False."
You can sort line items in analysis detail for any column that includes an up/down arrow.
Analysis Results Footer Information
The analysis footer, which appears on every page of the results, contains the following information:
·the name of the administrator who generated the analysis (which can be useful if results are exported or printed and distributed, since the content of the analysis reflects that administrator's permissions)
·the number of pages in the analysis (you can scroll through multi-page results from the navigation toolbar in the search results header), and
·the date and time when the results were generated.
Selection Summary
The Selection table is repeated at the end of the Results section. This information is included in printed or exported results, as a helpful reminder of the item(s) included in your analysis.