Access Explorer agent
The indexing of only explicit permissions is done for the following reasons:
A local agent does an immediate scan as soon as it is added. Remote agents only scan according to a schedule, but if you want the agent to scan as soon as it is added you can enable the Immediately scan on agent restart or scope change option. This option is cleared by default.
Scopes
|
• |
Scopes tab of the Agent Properties. |
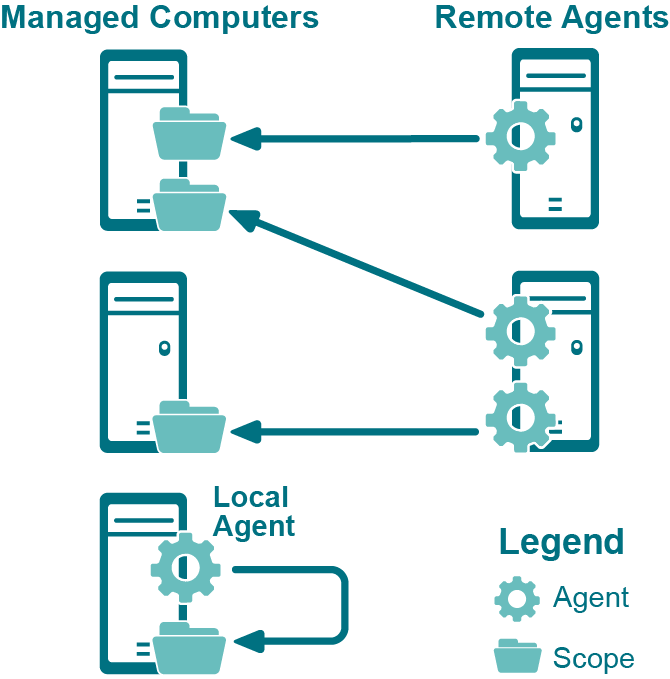
Figure 1 depicts the possible deployment scenarios for Access Explorer agents and managed computers in remote and local installations.
Database
The Security Explorer server stores all data gathered in a SQL Server® database, including indexed data received from the agents. See Setting up the Access Explorer database.
Service accounts
|
Yes1 | |||
|
1 The managed domain service account is used to install, upgrade, or remove the agent on the target computer. In the case where the agent is deployed locally, the agent will run as Local System. In the case where an agent is deployed remotely, the managed computer service account is used to read information from the remote computer. | |||
Access Explorer uses the Advanced Encryption Standard with a 256-bit key to protect secure data.