Offline Domain Join - Trust Requirements
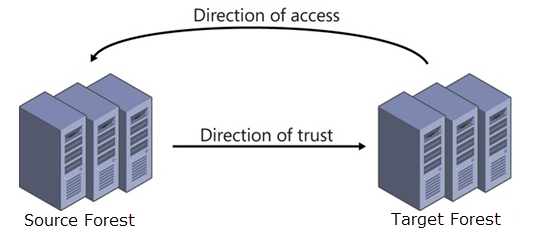
To use the new Cached Credentials job (which supports the Offline Domain Join feature) a one-way external trust must be configured from the source domain to the target domain (source trusts target).
Cached Credentials will validate and cache the login of a target user account prior to a workstation cutover so that they may successfully login to the target forest after cutover without the need to be on the network for the first login which for remote users is typically a challenge. In order to facilitate the caching of target user accounts the workstations being migrated must be allowed to use the target user accounts for authentication which is why the dependency of a one-way trust is required.
With the addition of the one-way trust we can establish a selective authentication model to limit and restrict the access of target objects to explicitly chosen target accounts and source resources by source forest administrators.
Offline Domain Join - Trust Options
When setting up a forest trust you have the options of limiting the direction of the trust (incoming vs outgoing), 1-way or 2-way as well the scope of authentication. With an Active Directory Trust, you can perform Forest-wide authentication or Selective Authentication.
Forest-wide Authentication
With Forest-wide authentication users from the trusted forest can automatically authenticate for all resources in the local forest.
Selective Authentication (Recommended Method)
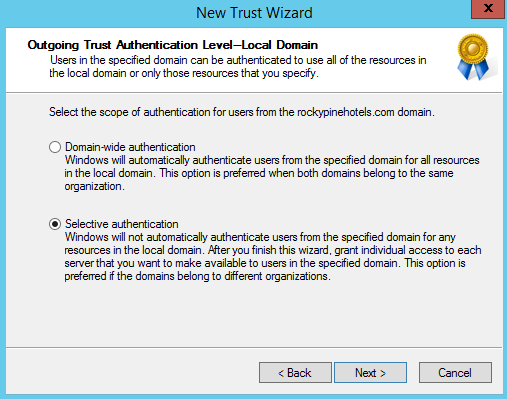
When using the Selective Authentication model, users from the trusted forest are not automatically granted the permission to authenticate to resources in the local forest and must be explicitly giving the permission to authenticate. This is the preferred method for handling trust relationships between two different organizations or where you want to limit the access you grant the trusted forest.
For Offline Domain Join purposes we can use selective authentication to limit the access of the target accounts that have the ability to perform the cache credential steps as well as limit the computer objects where these accounts have the ability to authenticate from which greatly limits the security implications of establishing a trust during an ongoing Active Directory Migration since the source domain is in complete control of where target authentication is allowed to be performed in the local forest.
Configuring an Active Directory Trust
Before we can start setting up selective authentication permissions, we first need to get a one-way trust established so target domain accounts can be cached on source workstations prior to cutover via Offline Domain Join. Below is a guide process to establishing a one-way trust between two organizations with selective authentication being used to limit target forest access.
DNS and Firewall Port Requirements
This guide assumes you have already met all required DNS, Firewall and Network Connectivity Requirements for establishing a trust as most of these would already be in place in order to perform a successful Active Directory Migration:
|
Network Connectivity |
Ensure there is network connectivity established between Forest A and Forest B |
|
Firewall Ports |
Ensure these ports are unblocked between two forests, at network level :
53 TCP/UDP DNS
88 TCP/UDP Kerberos
389 TCP/UDP LDAP
636 TCP LDAP (SSL)
445 TCP SMB
135 TCP RPC Endpoint Mapper
1024-65535/TCP RPC for LSA, SAM, Netlogon (*)
|
|
Name Resolution |
Name Resolution should work between Forest A and Forest B. For that use conditional forwarder or stub zone. |
|
Access |
Membership of Enterprise Admin group is required. Alternatively, the Domain Admin of Forest Root Domain (or equivalent access through delegation) can create Forest Trust. |



