Keeping Event Data on the InTrust Agent Side
To ensure the integrity of event data from the specified data source, you can create agent-side log backup. This will help you to protect data from losses that may occur due to accidental or malicious log cleanup on the target machine. Log backup can be created for the most frequently used data sources (for example, Windows Event logs).
Agent-side log backup uses a compression method similar to that used in InTrust repositories. On average, the contents of the event cache are compressed to 1/15th their original size.
Agent-side cache is always used to process data from monitoring-only data sources. For the data sources used in both gathering and monitoring processes, you can select whether to create agent-side log backup.
Agent-side log backup is unavailable for gathering-only data sources, for example, MS ISA Server logs and MS Proxy Server logs.
|
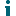
|
TIP: By default, the agent-side log backup feature is disabled but it is recommended to enable this option. This mismatch between the default and recommended setting value arises due to specificity of the InTrust task execution. |
To configure agent-side log backup
- Schedule the InTrust task that will process the selected data source.
- Open the properties of the data source under the gathering policy.
- Select the Enable log backup and use it to gather events option:
- The Clear the backup after gathering check box is automatically selected together with the Enable log backup and use it to gather events option.
- If a data source is used by more than one task and the agent-log backup feature is enabled for the data source, deselect the Clear the backup after gathering check box to avoid data loss.
|
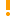
|
Caution: After you enable agent-side log backup, the log will be cleared the next time it is gathered. Subsequent gathering sessions do not clear the log. |
- Click OK to save the settings and close the dialog; commit the changes.
|
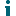
|
Important: Agent-side log backup will be created only if both of the following are true:
- At least one gathering policy processing this log uses it with this option selected.
- The schedule is enabled for at least one task involving this policy.
|
To set the log backup retention period
- Select Configuration | Data Sources, and select the necessary data source.
- From its shortcut menu, select Properties.
- On the General tab, specify agent-side log backup retention period.
Tuning Jobs
Each type of InTrust job has a number of settings, both general and job type-specific. They general settings are available on the General tab of the job’s properties, and specify the following:
- Job name and optional description.
- Account that is used to run a job. Jobs use accounts as follows:
- To access objects in a site, a job can use the task account (by default) or a custom account that you specify. However, if a site account is specified in the site’s properties, the job will use the site account.
- To access data stores—that is, repositories and databases—the job uses the task account or a custom specified account. However, if an account is specified for a data store, the job uses it to access that data store.
- Make sure that accounts used by jobs have the necessary permissions on the site objects and data stores for the job to be performed correctly.
- Whether the job is enabled or disabled. If disabled, the job appears in the task workflow, but it is not executed.
So, to make your job available for execution, you must supply the job name and enable the job.
Using Deadlines
On the Deadline tab of the job’s properties, you can provide an optional deadline value for a job. The deadline is the period of time that will pass before the job is started.
The countdown starts in the following situations:
- The moment the task is launched (if the Task option is selected).
- At the beginning of another job (if the Job option is selected and a preceding job is specified).
When the specified time runs out, this setting launches the next job or jobs without terminating the job in progress.
A deadline can be specified for any job in the task, unless it is the job that starts the task or one of such task-starting jobs running simultaneously.
|
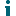
|
Note: Turning on the deadline and specifying zero values for days, hours and minutes is the same as turning the deadline off. |
Job Types
See the following topics for details about the specific job types:
Gathering Job
A gathering job collects audit data to a repository and/or audit database.
To configure a gathering job
- In the job’s properties dialog box, open the Gathering tab.
- Assign a gathering policy to a site.
- Select the repository and/or database where the collected data will be stored.
|
|
Caution: Do not configure gathering jobs to collect events to repositories that are used for real-time gathering in InTrust Deployment Manager. |
- Specify whether to use agents for data collection.
Gathering to a database always starts with events that follow the last gathered event. Thus, if you have gathered data for a certain period of time using a certain filter, then you cannot gather data for the same period of time using a different filter.
When gathering to a repository, you always store events as specified by the filters you use. Duplicate events are also stored.
Events from the data sources of Microsoft Windows Events type (such as Windows Application log) have standard descriptions. If you are gathering these events to a repository, event descriptions are collected automatically. If you are gathering events to an audit database and you need to store these descriptions, take the following steps:
- Locate the corresponding data source by selecting Configuration | Data Sources.
- Open its properties dialog box. Click the Microsoft Windows Events tab and select Store event descriptions to database.
Using Agents to Gather Data
Data can be gathered with or without agents. To decide whether or not to use agents, consider the following:
- If collected with agents, data is communicated to the server in compressed form, which greatly decreases network traffic. Moreover, agent-side encryption ensures that data cannot be intercepted and decoded when being transferred over the network.
- There are few reasons, if any, for not using agents. For example, on some critical computers you may want no extra services, even if they start and stop automatically. You can collect data from such computers without agents.
- Finally, in some cases you cannot avoid using agents: for example, when you need to collect audit data from behind a firewall or when you want to collect Unix events.
To automatically install agents to all site computers in bulk, from site's shortcut menu, select Install Agents. Note that this is possible only in the Windows environment, on computers that are on the same side of a firewall.
For detailed description of manual agent installation, see Installing Agents Manually.
You can automate the installation of agents using Group Policy settings. InTrust is shipped with a Windows Installer file containing the agent package.
To automatically install agents on specific computers using Group Policy
- Copy the agent package from the Agent folder in your InTrust distribution to a share available to all those computers.
- In the Active Directory Users and Computers MMC snap-in, create an OU that includes all of the required computers and add a Group Policy object for this OU.
- Using the Group Policy Object Editor MMC snap-in, in Computer Settings, assign the agent package to the Group Policy object you added earlier.
- To make InTrust process these computers with agents, make sure the computers are included in InTrust sites.
To prohibit automatic agent installation on site computers
- Right-click the site and select Properties.
- On the General tab, select the Prohibit automatic agent deployment on site computers option.
To gather audit data with agents
- Open the gathering job properties.
- Select Use agents to execute this job on target computers.
- When the job starts, agents are installed automatically to site computers (if not deployed yet) and perform audit data gathering locally.
You can enable agent-server authentication using Diffie Hellman (DH) and agent-side data encryption using 3DES.
To enable agent-server authentication and agent-side data encryption
- Select Configuration | InTrust Servers, and right–click the InTrust server the agents belong to.
- On the Agent tab of the properties dialog box, select the corresponding options.
Consolidation Job
A consolidation job copies audit data from one repository to another.
When you create or modify a consolidation job, you need to select the following:
- The server where to run the job
- The source and target repositories
- The policy according to which data will be picked for consolidation
- The repository objects from which the audit data is taken
Consolidation over a Firewall
You can consolidate audit data from a repository that is located on an InTrust server behind a firewall. To do it, first find out the local repository path on the InTrust server behind the firewall and the password of the InTrust organization behind the firewall. Then take the following steps:
- Create a new repository. For that, right-click Configuration | Data Stores | Repositories and select New Repository.
Consider giving the new repository a name that indicates it is located behind the firewall.
- On the Repository Location step of the New Repository Wizard, supply the local repository path so that it is identical to the local path of the repository behind the firewall. Complete the wizard.
|
|
Caution: The path you specify is not verified. The repository object you created on step 1 is just a representation of the source repository. The actual repository will be found as long as the path is correct. |
- Right-click the necessary task and select New Job; start creating a consolidation job.
- On the Select Repositories step, do the following:
- Select the source repository
- Select Use this server to manage source repository and specify the InTrust server that hosts the repository.
- Specify the port over which your firewall allows communication. By default, port 900 is used.
- Specify and confirm the password of the InTrust organization that the InTrust server behind the firewall belongs to.
- Select the destination repository.
- Complete the wizard.
Now, you can configure job dependencies in the task and use the task as necessary.