This example shows how to create a data source for the Apache access log. The example assumes that the following settings are specified in the Apache configuration file httpd.conf:
To create a data source for the Apache access log
The expression you specified matches lines similar to the following:
The expression matches five fragments in each line, and these fragments are mapped to fields as follows:
| Match | Field |
Description |
|---|---|---|
| 1 | Computer | Client IP address or hostname |
| 2 | Date/Time | The time when the server finished processing the request |
| 3 | Insertion String 1 |
Request line from the client |
| 4 | Insertion String 2 |
Status code that the server sends back to the client |
| 5 | Insertion String 3 |
The size of the object returned to the client |
To see an example of field mapping configuration
If you use software that stores its audit trails in databases, you can set up InTrust to gather such logs and store them. This can be required by regulations, or you may want to create backup storage for those logs using a different platform.
To create a custom database events data source
In the wizard, configure the following settings:
If you use agents for gathering, the keyword is resolved on the agent side, and gathering is performed from all of the site's computers simultaneously, which gives better performance. If you do not use agents, the keyword is resolved by the InTrust server, and each computer in the site is processed in turn.
To edit an existing database events data source, right-click the data source and select Properties.
The SQL query you specify must include the variable %LAST_GATHERED_EVENT%. This keyword defines where the gathering starts from. If you ignore this keyword, the entire contents of the database are gathered. Doing so multiple times severely impedes performance and, if you gather to a repository, results in duplicate data.
It is recommended that you use %LAST_GATHERED_EVENT% as part of a “where” statement, such as the following:
select Time, ID, TestString from TestDatabase where Time >= %LAST_GATHERED_EVENT% order by Time
It makes sense to associate %LAST_GATHERED_EVENT% with event time. This helps avoid duplication of data even if different selection parameters are used in the query for different sessions.
It is also a good idea to make the query order events by time. Otherwise, the value of %LAST_GATHERED_EVENT% may remain the same from session to session. If you order by time, which is unique for most events, the value of %LAST_GATHERED_EVENT% is updated after each gathering, so you do not have to specify it for subsequent gathering sessions.
When you first create the data source, specify a value for %LAST_GATHERED_EVENT%. If you use the keyword as recommended, supply the date and time from which you want gathering to start. If you want to gather everything, supply a time earlier than the earliest in the log.
Be careful to use a time formatting and conversion convention that is appropriate for your RDBMS. If you associate %LAST_GATHERED_EVENT% with time, it is best to use the 24-hour format rather than the 12-hour format to avoid confusion.
On the Database Fields Mapping step, establish a correspondence between the fields in the original database and the InTrust representation of that database. The following controls are used:
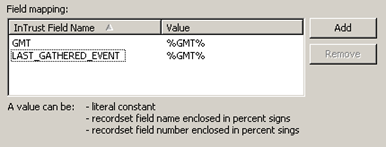
On the left, specify the InTrust event fields. On the right, supply the database fields that match them.
InTrust field names are predefined, and you cannot specify custom names. However, you can supply as many insertion strings as you like, such as “Insertion String #1” or “Insertion String #99”. These are provided for fields that are unrelated to any of the existing InTrust fields.
The GMT and LAST_GATHERED_EVENT fields are mandatory. GMT should be mapped to event date and time. LAST_GATHERED_EVENT should be mapped to the field whose content InTrust will look at to determine where to start gathering. It is best to map LAST_GATHERED_EVENT to event date and time as well.
To use the data source in a new gathering policy