Quest On Demand uses the Role-based Access Control (RBAC) security policy that restricts information system access to authorized users. Your Quest On Demand organization comes configured with a number of default roles which cannot be changed, but subscribers can create custom roles with the permissions to perform needed operations on the assets of the organization.
If you are the On Demand administrator or the owner of the subscription, you can add users to an existing organization and assign the required roles. If you are not the subscription owner or administrator, contact your On Demand administrator for access.
When you add a user to an organization, you also assign one or more roles. The role assignment determines what permission level a user has and ultimately, what tasks the user can perform. Assigning roles and setting user permissions is referred to as access control.
Access control is a process by which users are granted access and certain privileges to systems, resources, or information. In On Demand, you can grant authenticated users access to specific resources based on your company policies and the permission level assigned to the user.
On Demand comes configured with a number of default roles. The default role permissions settings cannot be changed, but you can create custom roles with specific permission settings to align with your company policies. You can assign multiple roles to each user in order to combine permission sets.
|

|
NOTE: Every user must be assigned to at least one role. You cannot remove all roles from a user.
For more information about the various roles that can be assigned to users, please see the On Demand Global Settings Current - User Guide. |
The Security Administrator role gives users full access to Security Guardian, as well as the following permissions for On Demand global settings:
For more information on assigning roles, see Users and Roles in the On Demand Global Settings User Guide.
The diagrams below illustrate how Security Guardian functions for both Active Directory and Entra ID, including how additional components are integrated.
Functional Overview for Active Directory
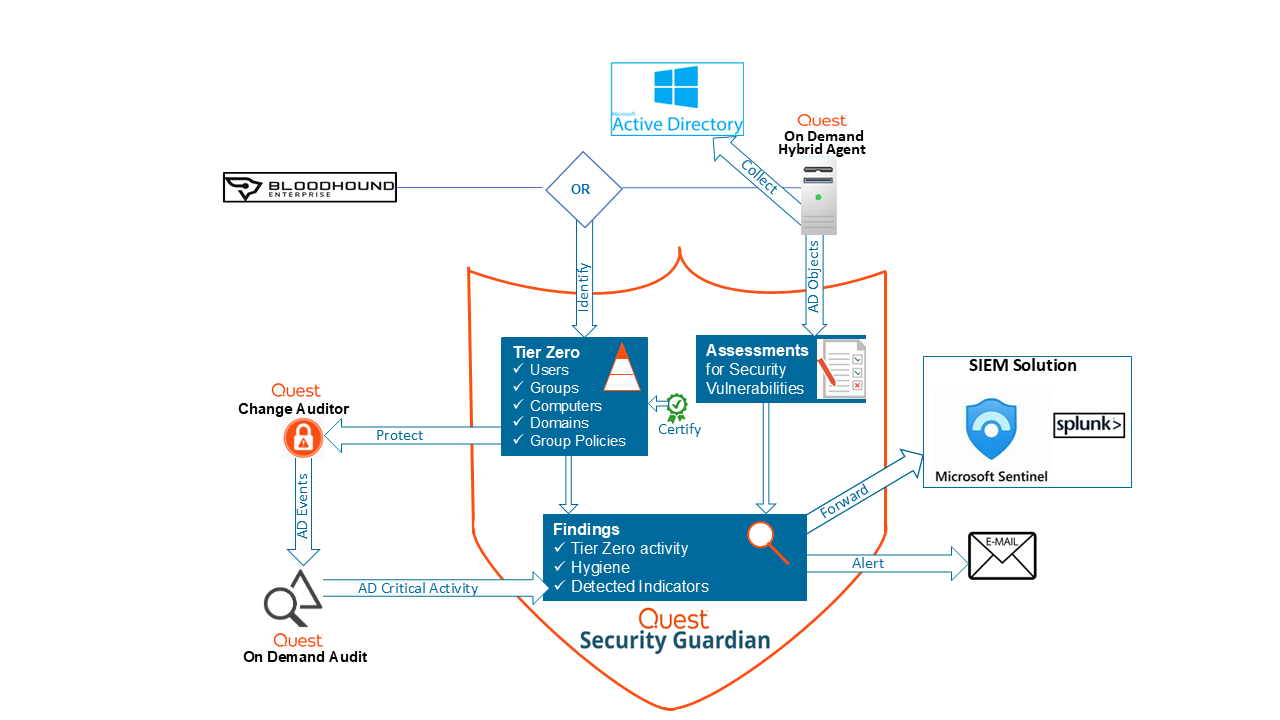 .
.
Functional Overview for Entra ID
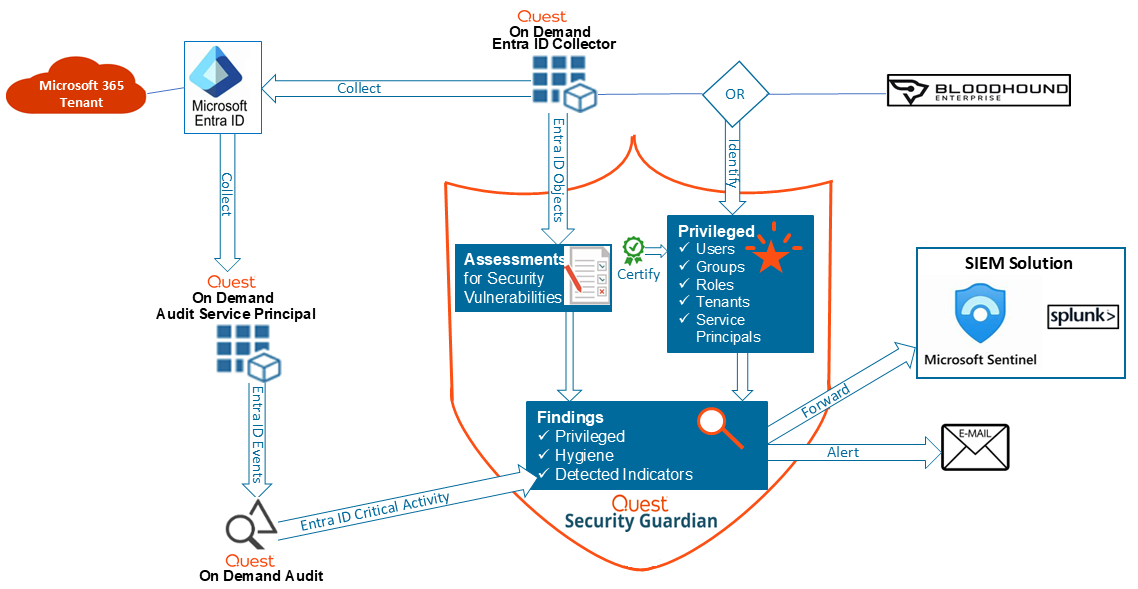
Additional components need to be configured to make Security Guardian fully functional.
To configure additional components:
-
From the On Demand left navigation menu, choose Security | Dashboard.
-
From the Configuration Status tile, configure the necessary components.
|

|
NOTE: Once an additional component is configured in On Demand, it's available to any other module that uses it. |
| Hybrid Agent |
Gives Security Guardian access to the Active Directory domain(s) that you want to keep secure. |
On Demand Global Settings User Guide - Managing your on-premises domains
When configuring the agent, ensure that:
- the action Collect Active Directory object data is selected
- any domain for which you want object data to be collected is added.
|

|
NOTES:
-
The Collect Active Directory object data action uses Lightweight Directory Access Protocol (LDAP) by default. However, it will use Secure LDAP (LDAPS) if your environment is configured for it. Refer to the topic Secure LDAP Configuration and Deployment in the On Demand Global Settings user guide for details.
-
In addition to the permissions required for the hybrid agent, the service account (which the Collect Active Directory object data action uses) requires an additional permission to assess certain vulnerabilities. | |
| Entra ID Data Collector |
A Service Principal that gives Security Guardian access to Entra ID objects in the tenant(s) that you want to keep secure. |
On Demand Global Settings:
When configuring the tenant, ensure that
Core | Collectors consent is granted to each tenant for which you want Entra ID object data to be collected.
|

|
NOTE: An additional consent, Audit | Basic is needed for the On Demand Audit Entra ID Service Principal to collect Critical Activity, which contributes to Detected Indicator findings in Security Guardian. | |
|
Quest Change Auditor
(via On Demand Audit) |
Sends Active Directory events to On Demand Audit for reporting in Security Guardian Findings and allows you to protect Tier Zero objects.
|

|
NOTE: A minimum of version 7.3 is required to send critical activity events to On Demand Audit, and a minimum of version 7.4 is required to protect Tier Zero objects. |
|
Instructions are provided via a tool tip in the Security Guardian UI. You can also find instructions at On Demand Audit User Guide - Change Auditor Integration
|
|
SpecterOps BloodHound Enterprise
(Optional) |
Identifies Tier Zero assets in your organization's Active Directory domain(s) and Privileged assets in your Entra ID tenant(s), which you can monitor and assess for security vulnerabilities in Security Guardian.
|

|
NOTE: If BloodHound Enterprise is not configured, Security Guardian will be used as your organization's provider. | |
On Demand Audit User Guide - SpecterOps BloodHound Integration |
|
SIEM solution:
(Optional) |
Allows Security Guardian Findings to be forwarded to a configured SIEM tool for further analysis
|

|
NOTE: Regardless of whether your organization uses a SIEM solution, you can also have Finding alerts sent via email. | |
Configuring a Forwarding Destination |
The Security Guardian dashboard displays a visual summary of the current security status of your organization's Active Directory and Entra ID.
To access the Security Guardian dashboard:
From the On Demand left navigation menu, choose Security | Dashboard. The dashboard contains tiles for each of the following components:
- Uncertified Tier Zero Objects (from Active Directory)
- Uncertified Privileged Objects (from Entra ID)
- Active Directory Tier Zero certification summary
- Entra ID Privileged Objects certification summary
- Highest Severity Findings
- Active Hygiene and Active Detected
- Configuration Status
The Uncertified Tier Zero Objects and Uncertified Privileged Objects tiles:
-
display the last time the objects list was synchronized
-
list the last ten uncertified objects of each type that were added to Security Guardian (you can click View All for an object type to view the complete list for each workload )
|

|
NOTE: Objects that have been certified are excluded from the lists. |
-
provide links that allow you to
The Highest Severity Findings tile displays the top five active findings of the highest severity. Information includes:
- the Finding name
- when the Finding was Detected
- the Finding Type (Tier Zero, Privileged Object, Hygiene, Detected TTP, or Detected Anomaly)
- the Severity indicator (Critical, High, or Medium)
- a link that allows you to Investigate the Finding
The View All link at the bottom of the tile allows you to view the list of all active Findings for the organization.
The Active Directory Tier Zero Objects and Entra ID Privileged Objects tiles display graphical representations of the number of certified vs. uncertified objects.
The Active Hygiene and Active Detected tile shows the total number of Hygiene and Detected (TTP and Anomaly) Findings in the organization by severity level (Critical, High, and Medium).
From the Configuration Status tile you can configure additional components and view existing configurations.



 .
.