Delete a certificate
Remove a certificate referred to by an alias.
bin/fglam --delete-certificate "user alias 1"
A full example for managing certificate for FglAM
Virtual Machine Automation
|
3 |
|
4 |
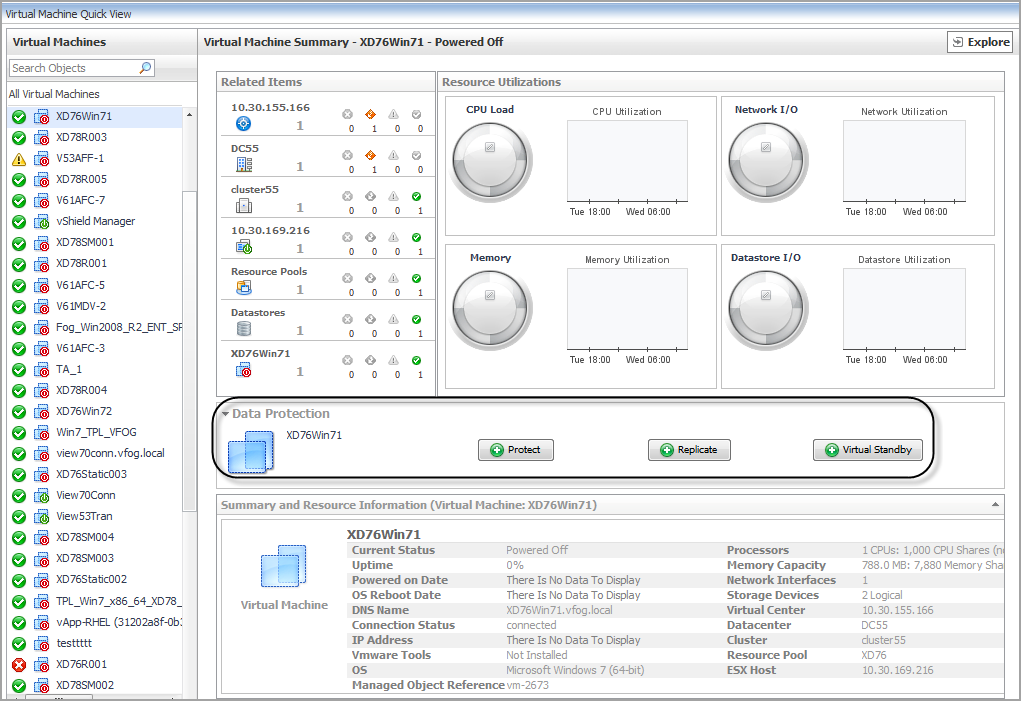
Select a Virtual Machine from the Monitoring > Virtual Machine Quick View > Virtual Machines tree view. |
The Protect Virtual Machine Automation includes the following three options:
|
• |
|
• |
|
• |
Automation of VM Protection
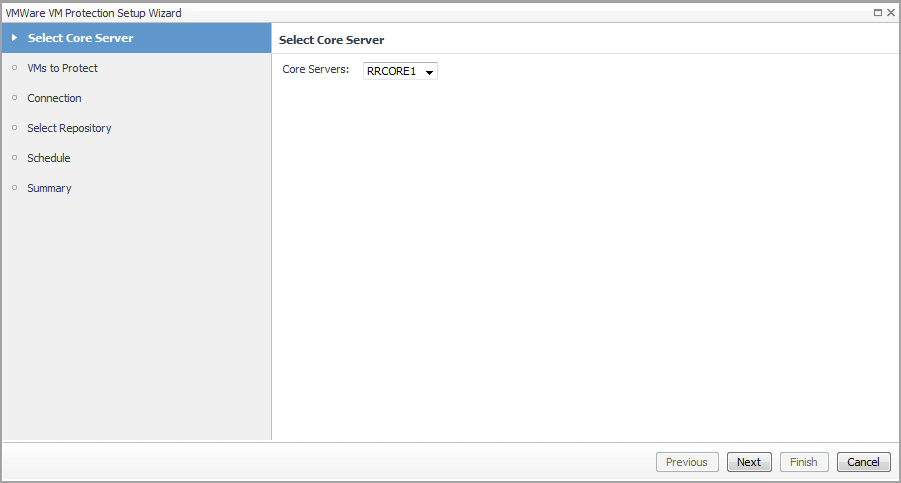
The VMware VM Protection Setup Wizard guides you through the procedure for identifying virtual machines that you want to protect. This wizard also enables you to customize the schedule for performing the protection automation.
|
3 |
|
4 |
Select a Virtual Machine that you want to protect from the Monitoring > Virtual Machine Quick View > Virtual Machines tree view. |
|
5 |
|
6 |
|
7 |
In the VMs to Protect step, select VMs from the left vCenter table, click >> to move selected VMs to the right table, and then click Next. |
|
8 |
|
9 |
In the Select Repository step, select a repository from the Core Repositories drop-down list, and then click Next. |
|
10 |
|
• |
Default protection: The automation will be performed hourly for all volumes. |
|
• |
Periods: The automation will be performed on specified weekdays or weekends. |
|
• |
Daily protection time: The automation will be performed on a daily basis. |
|
11 |