Removing Web sites from the existing collection
|
2 |
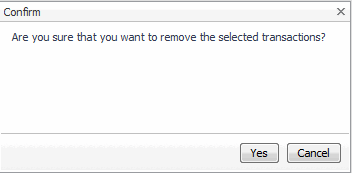
Click Yes to confirm the removal and close the message box. |
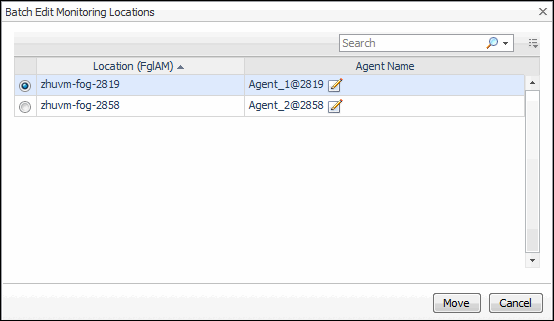
Moving multiple transactions as a group
|
4 |
Click Move Transactions. |
|
6 |
Click Move. |
Removing stale transactions from the Performance Browser dashboard
|
1 |
|
2 |
On the navigation panel, under Dashboards, click Management Server > Servers > Data Management. |
Viewing and editing individual Web transaction details
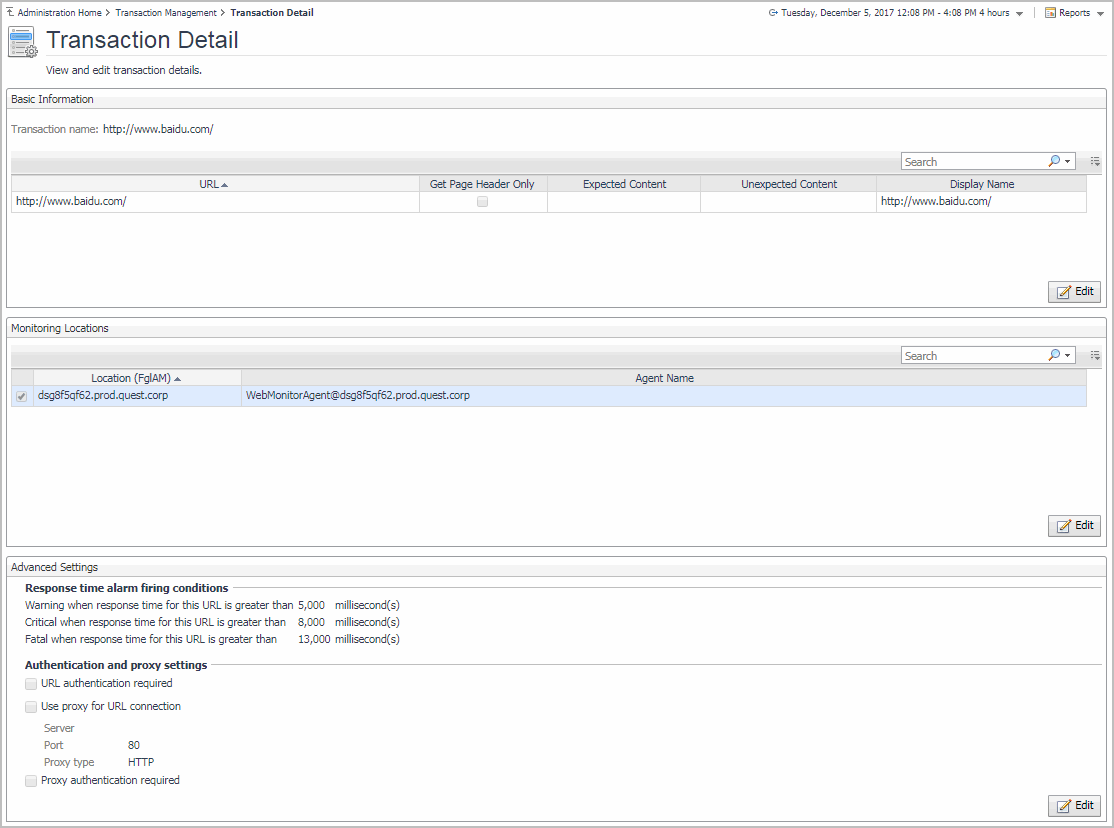
For more information about the Transaction Management dashboard, see Exploring your collection of monitored Web sites. For complete details about the data appearing on this dashboard, see Transaction Detail view.
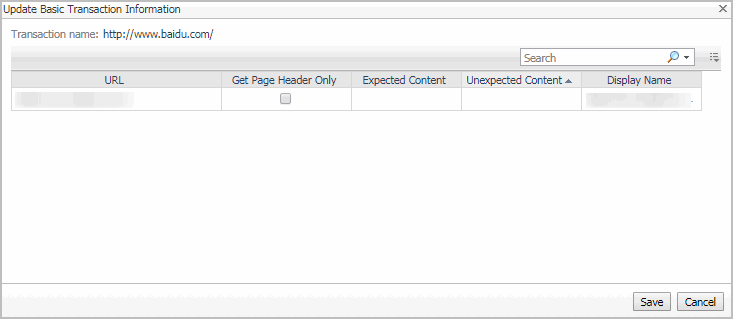
You can make changes to any transaction details that appear on this dashboard by clicking the appropriate Edit button and making the required changes.
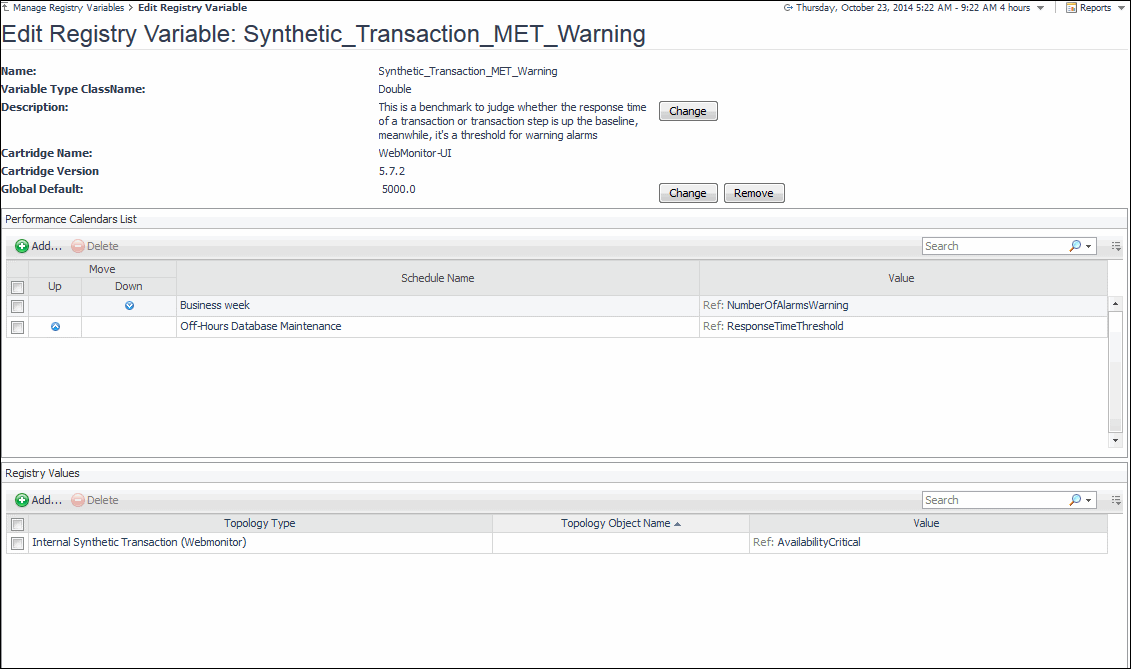
Any changes you make to transaction alarm thresholds results in creating topology-scoped values of the registry variables that control these thresholds, and the other way around. The topology type used to contain Web transaction definitions is Internal Synthetic Transaction (Webmonitor), and the Internal Synthetic Transaction (Webmonitor) topology object names are the configured transactions names.
For more information about the Foglight registry, see the Administration and Configuration Help.
|
• |
|
• |
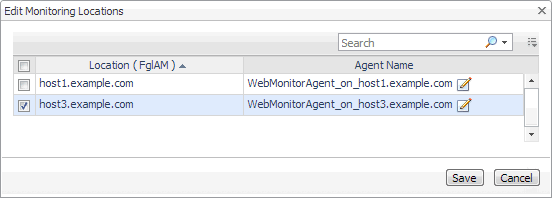
To start monitoring this Web site with a new set of monitoring agents, in the Monitoring Location view, click Edit. |
|
• |
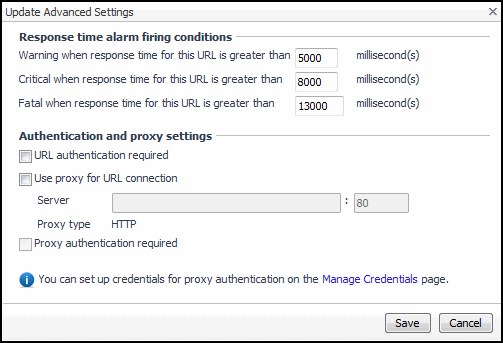
To specify different thresholds for alarm generation, or authentication and proxy settings, in the Advanced Settings view, click Edit. |
|
2 |
Click Save. |