Manage Registry Variables and Check Registry Value
By default, the following columns are displayed:
|
• |
Variable Name: The variable name. |
|
• |
Type: Shows the data type of the registry variable. Possible values include Double, Integer, Long, String, Boolean, Timestamp, and Password. For more information about these data types, see Step 3 in Getting started: create registry variables. |
|
• |
Cartridge Name: The name of the cartridge in which the registry variable is defined, if applicable. This column is blank for any registry variables that you create using this dashboard. |
|
• |
Global Default: The global default value assigned to the variable. If the global default points to another registry variable, it starts with the prefix Ref:, followed by the referenced registry variable name. |
|
• |
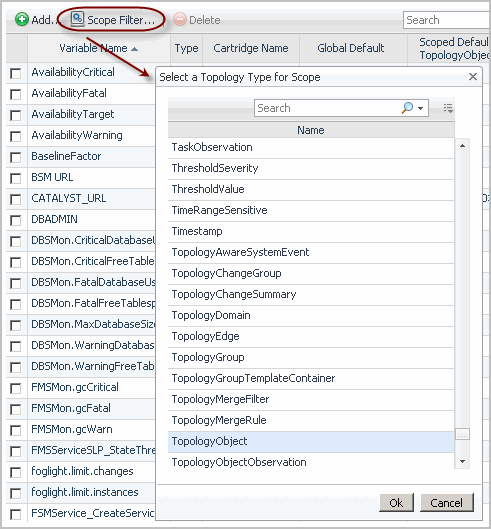
Scoped Default (TopologyObject): The value assigned to the variable when the variable is scoped to a particular type. To scope on a topology type, click Scope Filter and choose from the available types. |
|
• |
Scheduled: Indicates if a performance calendar is defined for the variable. For more information about performance calendars, see Using performance calendars in registry variable definitions. |
|
• |
Active Schedule: If performance calendars are defined, this column indicates the name of the current schedule, if applicable. |
In addition to these columns, the following columns can also be displayed by clicking and selecting them from the Show Columns dwell that appears.
|
• |
Cartridge Version: The cartridge version in which the registry variable is defined. |
|
• |
Last Modified: The date and time at which the registry variable was last modified. |
For more information about the New Registry Variable Wizard, see Getting started: create registry variables.
For more information about these flows, see View and edit registry variable settings and Copy or delete registry variables.
If you have any registry variables that are no longer referenced in rule conditions, you can delete them from the list. When a registry variable is deleted, all references to that variable in rule conditions and expressions become invalid. This may cause the rule to fail to evaluate. If this occurs, you must manually modify the rule condition or expression. For details, see Writing conditional expressions for time-, data-, or schedule-driven rules and Write a conditional expression for an event-driven rule.
|
1 |
On the navigation panel, under Dashboards, click Administration > Rules & Notifications > Manage Registry Variables. |
|
3 |
|
IMPORTANT: You must use a unique name. |
From here, you can edit the newly copied registry variable to better suit your needs. For example, you can have its value change over time, or scope it to topology types or object instances. For further information, see Using performance calendars in registry variable definitions and Scoping registry variables to topology types or object instances.
|
1 |
On the navigation panel, under Dashboards, click Administration > Rules & Notifications > Manage Registry Variables. |
|
3 |
Click Delete. |
|
4 |
|
1 |
On the navigation panel, under Dashboards, click Administration > Rules & Notifications > Manage Registry Variables. |
|
• |
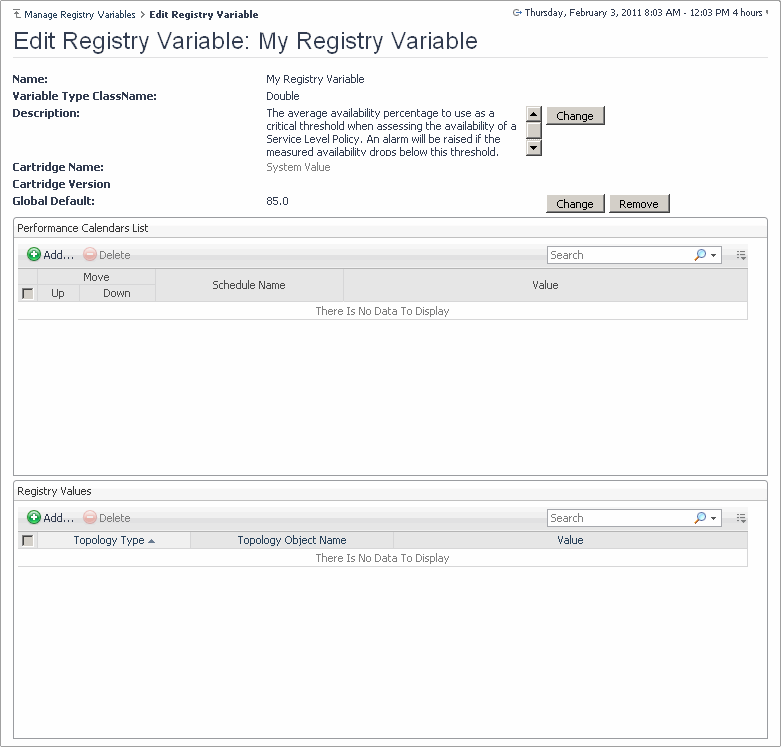
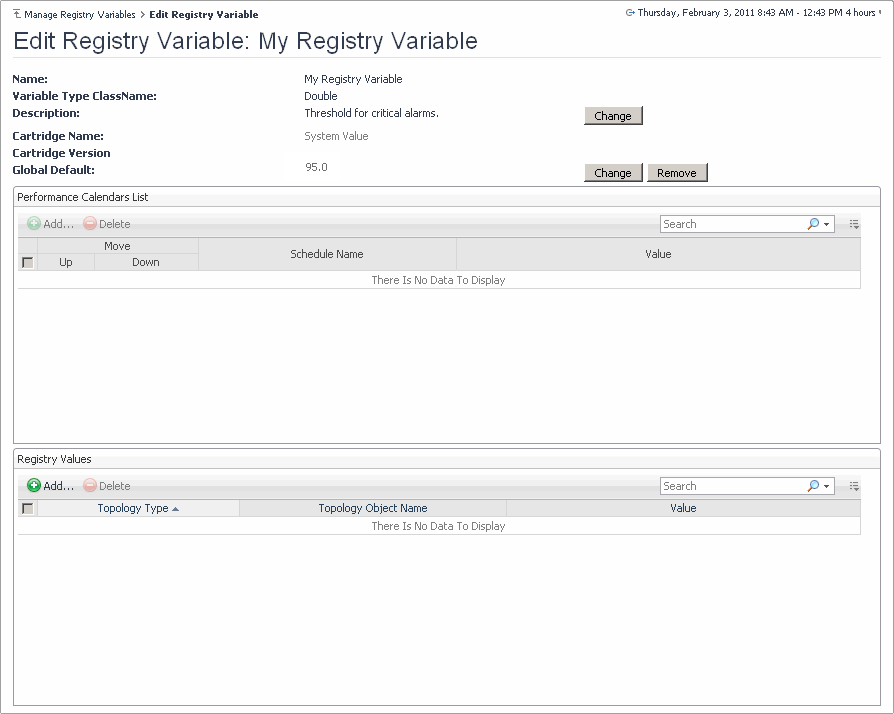
Name: The name of the registry variable. |
|
• |
Variable Type ClassName: The data type of the registry variable. |
|
• |
Description: A brief description of the registry variable. |
|
• |
Cartridge Name: If the registry variable is defined and included in a cartridge, this field contains the cartridge name in which the registry variable is defined. If you created this variable, this is indicated by the System Value setting that appears in this field. |
|
• |
Cartridge Version: If the registry variable is defined and included in a cartridge, this field contains the cartridge version in which the variable is defined. If you created this variable, this field is blank. |
|
• |
Global Default: The global default value. If the global default points to another registry variable, it starts with the prefix Ref:, followed by the referenced registry variable name. |
|
• |
Performance Calendars List: Shows a list of values that are associated with specific schedules. Having one or more entries in this list causes the registry value to change over time. |
|
• |
Registry Values: Shows a list of values scoped to specific topology types and their instances (if applicable). This causes the registry value to change in rules and derived metrics. |
From here, you can edit the registry variable to better suit your needs. For example, you can have its value change over time, or scope it to topology types or object instances. For further information, see Using performance calendars in registry variable definitions and Scoping registry variables to topology types or object instances.
Many registry variables come included with Foglight and installed cartridges, including AvailabilityCritical, AvailabilityFatal, AvailabilityTarget, and many others. If the existing registry variables do not meet your needs, you can create a new one and add it to the registry variable collection.
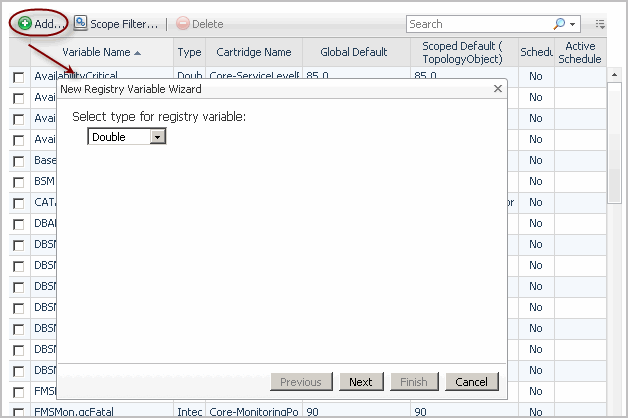
The values that you assign to a variable in the wizard must be consistent with the data type that you specify at variable creation time. For example, if you selected the data type Integer, you need to provide a valid integer number when specifying the value.
|
1 |
On the navigation panel, under Dashboards, click Administration > Rules & Notifications > Manage Registry Variables. |
|
A boolean value: true or false. |
||
|
A decimal value between 2-1074 and |
||
|
An integer value between -231 and 231 -1. For example, valid values include 235 and -10000. |
||
|
An integer value that is too large to fit the Integer data type. It can be in the range between -263 and 263- 1. |
||
|
A password value. Prior to storing the value of the Password data type in the registry, Foglight encrypts it and saves the encrypted value in the database. This is useful in cases where you need to secure password values when passing it to command or remote command actions. For example, you create a registry variable of the Password type, MyPassword, and set its value to demo123. Foglight encrypts the registry value, then stores it encrypted in the database (for example, 43-119-184-240-170-150-124-218-30-112-216-76-197-233-188-206). In a function call registry("MyPassword"), Foglight retrieves the registry value from the database in its encrypted form, which secures the password value. |
||
|
Contains a date and time. For example, valid values include 06/12/06, 2006-06-21 15:30:21.0, June 7, 2006 3:08:21 PM. |
|
b |
|
• |
Name: The name of the variable. This is a required value. The registry variable name cannot be longer than 255 characters and must be unique. In addition, the name cannot be changed once the registry variable has been added. This is because registry variables are referred to by their names in rule conditions and expressions and changing them would invalidate these references. However, you can copy a registry variable and give it a different name. |
|
• |
Description: Comments about the variable or its usage. This value is optional. |
|
• |
To specify the Global Default value, click Next. The New Registry Variable Wizard dialog box refreshes. |
|
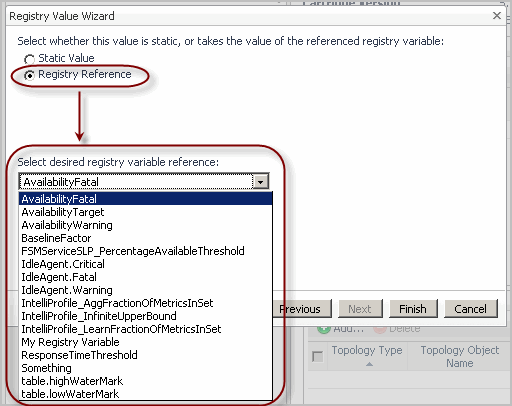
• |
To specify a new, static value as the global default, select Static Value, and then enter the desired value. |
|
• |
To specify another registry variable as the global default, select Registry Reference, and then select the desired registry variable from the list that appears below. |
|
• |
Variable Type ClassName: The data type of the registry variable you specified in Step 3. |
|
• |
Description: The description of the registry variable you specified in Step 4. |
|
• |
Global Default: The global default value you specified in Step 6. If the global default points to another registry variable, it starts with the prefix Ref:, followed by the referenced registry variable name. |
|
• |
Performance Calendars List: Shows a list of values that are associated with specific schedules. Performance calendars are always associated with the global default. If the global default is not set, performance calendars cannot be added. When you first create a registry variable, this list is empty by default. Having one or more entries in this list causes the registry value to change over time. |
|
• |
Registry Values: Shows a list of values scoped to specific topology types and their instances (if applicable). When you first create a registry variable, this list is empty by default.Having multiple scoped values causes the registry value to change in rules and derived metrics. |
From here, you can edit the newly created registry variable to better suit your needs. For example, you can have its value change over time, or scope it to topology types or object instances. For further information, see Using performance calendars in registry variable definitions and Scoping registry variables to topology types or object instances.
For example, there is a simple rule that applies to the servlets in your application; an alarm fires if the request response time for a servlet exceeds a value set by the ResponseTimeTooLong registry variable that is scoped to the topology type J2EEServlet and with the default scoped value of eight seconds. However, you know that at certain times of day response times for servlet instances are expected to exceed this threshold. At these times, the acceptable response time can be as long as 15 seconds. To prevent alarms from generating as a result of false positives, leave the variable’s scoped value of eight seconds, and create a schedule that recurs daily at the times when it is acceptable for response times for the servlet instances to exceed eight seconds, and specify the alternative threshold of 15 seconds by associating this value with the schedule.
|
1 |
|
• |
|
• |
To reference another registry variable, select Registry Reference, and then select the desired registry variable from the list that appears below. |
From here, you can proceed to Scoping registry variables to topology types or object instances.
|
1 |
|
2 |
|
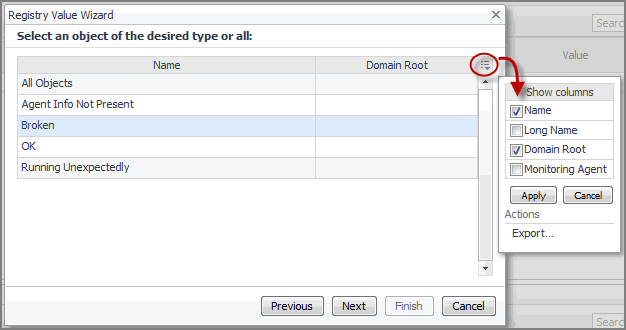
TIP: Use the Customizer to display two additional columns that are hidden by default: Long Name and Monitoring Agent. Long Name consists of the object name followed by its type name. For example: Broken (AgentHealthState). Monitoring Agent contains the name of the monitoring agent. This information is important if you have monitoring agents whose definitions include objects of the same type and name, like the legacy Cartridge for Operating Systems agents. For more information about the Customizer, see the Foglight User Help. |
|
3 |
Optional — narrow down your scope to a particular object. By default, All Objects is selected, meaning that the registry value is scoped to all instances of the selected type. |
|
• |
|
• |
To reference another registry variable, select Registry Reference, and then select the desired registry variable from the list that appears below. |
|
1 |
On the navigation panel, under Dashboards, choose Administration > Rules & Notifications > Check Registry Value. |
|
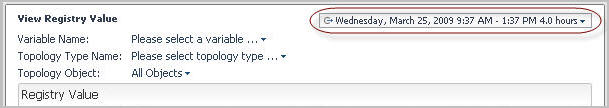
• |
Variable Name: The name of the registry variable whose value you want to view. |
|
• |
Topology Type Name: The topology type with which the registry value is associated. |
|
• |
Topology Object: The object instance of the specified topology type with which the registry value is associated. |
|
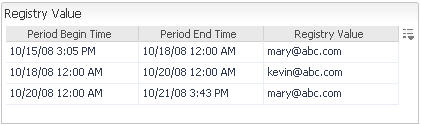
• |
Registry Value: The value to which the variable is set during a specified date and time range. If there are multiple time ranges during which the registry value changes, the table shows the registry value for each range. |
|
a |
|
b |
In the Registry Variable list, scroll down until you find a registry variable, and select that entry. For example, to select the SYSADMIN variable, select SYSADMIN. |
|
a |
|
b |
In the Topology Type list, select a type. |
|
a |
|
b |
In the Topology Object list, select an object instance. |
|
7 |
Optional — Reduce the number of columns that appear in the Registry Value table by clicking |
|
• |
Export as CSV, to export the table contents to a Comma Separated Values (CSV) file. |
|
• |
Export as PDF, to export the table contents to a PDF file. |
|
• |
Export as Excel, to export the table contents to an Excel file. |
|
• |
Export as XML, to export the table contents to an XML file. |
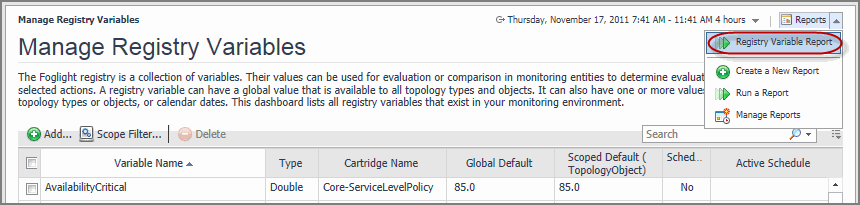
Some Foglight dashboards have reports associated with them. This allows you to run a report based on the current dashboard. You can generate the report using the Reports menu in the top-right corner.
The Manage Registry Variables dashboard is associated with the Registry Variable Report. Run this report by choosing Registry Variable Report from the Reports menu, and specifying the input parameters in the report wizard.
Manage Schedules
Foglight allows you to control access to a schedule. For each schedule you can grant or deny read, write, or control access to roles or users. For more information about security concepts in Foglight, see Managing Users and Security.
Foglight employs the following behavior when it comes to schedule permissions:
|
1 |
|
b |
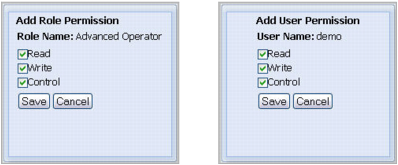
In the dialog box, use the Read, Write, and Control check boxes to assign permissions as required, and click Save. |
|
b |
To edit permissions, ensure that Edit is selected and use the Read, Write, and Control check boxes as required. |
|
c |
Click Save. |
|
1 |
|
1 |
|
2 |
|
3 |
Click the Delete Selected button at the bottom. |
|
4 |
|
1 |
|
2 |
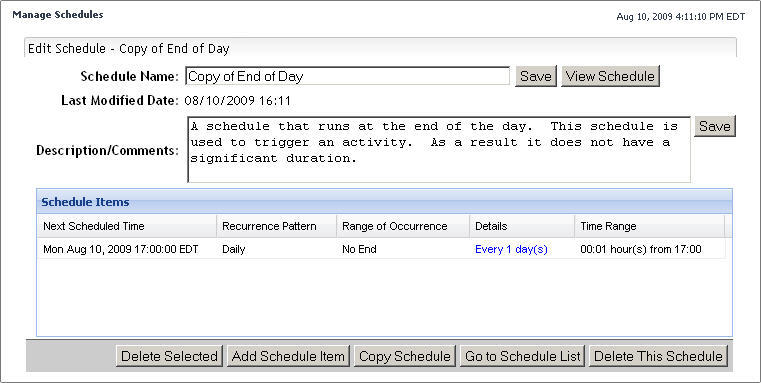
On the Manage Schedules dashboard, click the Schedule Name column of the row containing the schedule whose definitions you want to view. |
|
1 |
|
3 |
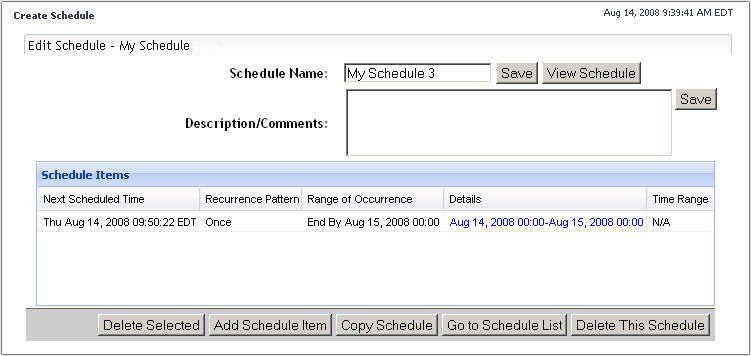
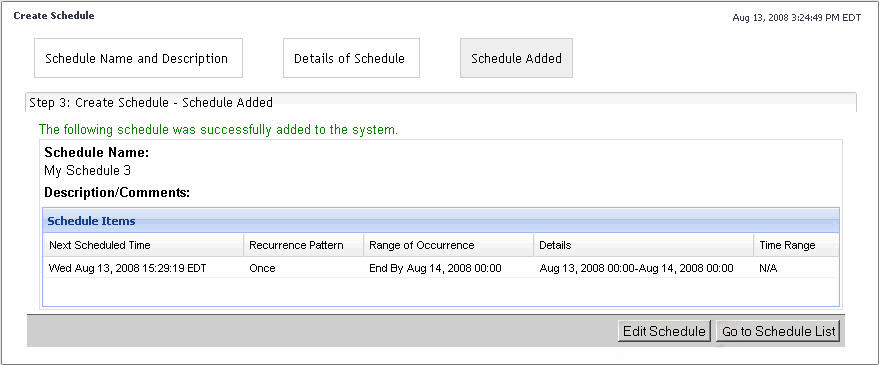
To add a schedule item, click Add Schedule Item. |
|
4 |
|
5 |
When you finish editing the schedule, click Go to Schedule List. |
A default Foglight installation includes a number of scheduled, including Always, Business hours, Business week, and many others. Rules, registry variables, and derived metrics can make use of schedules. For example, a registry variable can have multiple values, each associated with a specific schedules. If none of the existing schedules meet your needs, you can create a new schedule and add it to the schedule collection.
|
• |
|
• |
|
4 |
Click Next. |
|
6 |
When you finish adding schedule items to the schedule, click Go to Schedule List. |
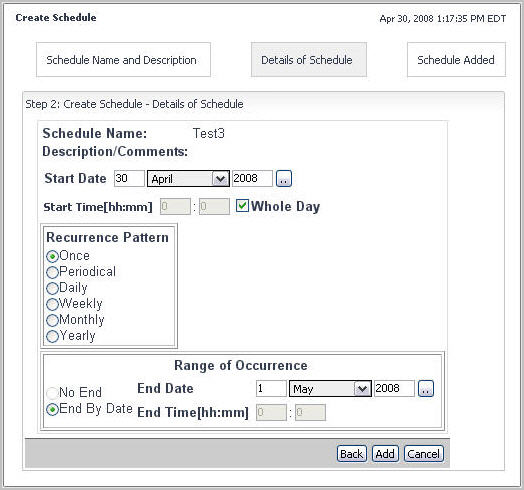
There are six types of patterns that you can define in a schedule item.
|
1 |
|
a |
Specify the day, month and year of the start date using the Start Date area. |
|
b |
Specify the hour and minute of the start time using the Start Time [hh:mm] area. |
|
3 |
Specify the date and time after which the schedule item ends using the controls in the Range of Occurrence area. |
|
a |
Use the End Date area to specify the day, month and year of the start date. |
|
b |
Use the End Time [hh:mm] area to specify the hour and minute of the end time. |
|
• |
New schedules. In the lower-right corner, click Add. |
|
• |
Existing schedules. In the lower-right corner, click Save. |
|
1 |
|
2 |
Specify the start date and time, and the duration of the recurrence pattern in the Start Date, Start Time, and Duration areas. |
|
a |
Use the Start Date boxes to specify the day, month and year of the start date. |
|
b |
Use the Start Time [hh:mm] boxes to specify the hour and minute of the start time. |
|
c |
Use the Duration [hh:mm] boxes to specify the hour and minute of the start time. |
|
IMPORTANT: The recurrence period must be longer than the duration specified in <Link>step 2. For example, if the duration of the schedule item is three hours, the recurrence periods should occur at intervals that are longer than three hours. |
|
4 |
Specify the date and time after which the schedule item ends using the controls in the Range of Occurrence area. |
|
• |
To specify an end date, in the Range of Occurrence area, ensure that End By Date is selected, and specify the end date and time using the End Date and End Time [hh:mm] areas. |
|
• |
To have the schedule item recurring at the recurrence pattern specified in Step 3 without an end date, in the Range of Occurrence area, select No End. |
|
• |
New schedules. In the lower-right corner, click Add. |
|
• |
Existing schedules. In the lower-right corner, click Save. |
|
1 |
| |||
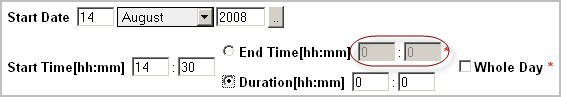
NOTE: The Duration [hh:mm] boxes appear disabled when you specify the End Time [hh:mm] option.
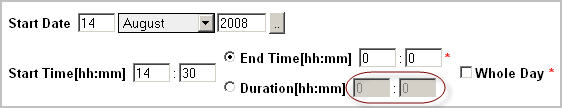 The end time should occur after the start time. | |||
| |||
| |||
|
• |
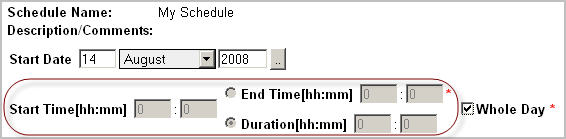
If you want the schedule to occur for the entire day, select the Whole Day check box. |
|
5 |
Specify the date and time after which the schedule item ends using the controls in the Range of Occurrence area. |
|
• |
To specify an end date, in the Range of Occurrence area, ensure that the End By Date option is selected, and specify the end date and time using the End Date and End Time [hh:mm] boxes as required. |
|
• |
To have the schedule item recurring at the recurrence pattern specified in Step 4 without an end date, in the Range of Occurrence area, select No End. |
|
• |
New schedules. In the lower-right corner, click Add. |
|
• |
Existing schedules. In the lower-right corner, click Save. |
|
1 |
| |||
NOTE: The Duration [hh:mm] boxes appear disabled when you specify the End Time [hh:mm] option.
 The end time should occur after the start time. | |||
| |||
| |||
|
• |
If you want the schedule to occur for the entire day, select the Whole Day check box. |
|
5 |
Specify the date and time after which the schedule item ends using the controls in the Range of Occurrence area. |
|
• |
To specify an end date, in the Range of Occurrence area, ensure that the End By Date option is selected, and specify the end date and time using the End Date and End Time [hh:mm] boxes as required. |
|
• |
To have the schedule item recurring at the recurrence pattern specified in Step 4 without an end date, in the Range of Occurrence area, select the No End option. |
|
• |
New schedules. In the lower-right corner, click Add. |
|
• |
Existing schedules. In the lower-right corner, click Save. |
|
1 |
| |||
NOTE: The Duration [hh:mm] boxes appear disabled when you specify the End Time [hh:mm] option.
 The end time should occur after the start time. | |||
| |||
| |||
|
• |
If you want the schedule to occur for the entire day, select the Whole Day check box. |
|
• |
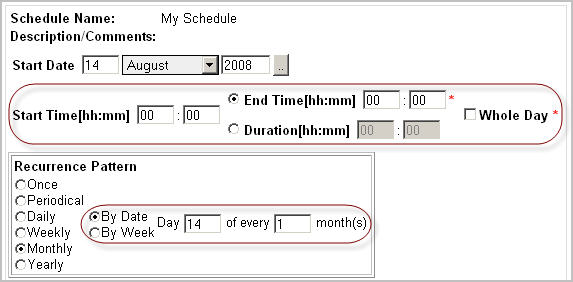
To have the schedule occurring on a specified day of the month, at the rate of one or more months, in the Recurrence Pattern area, ensure that the By Date option is selected, and then specify the day of the month and the rate at which it occurs. |
|
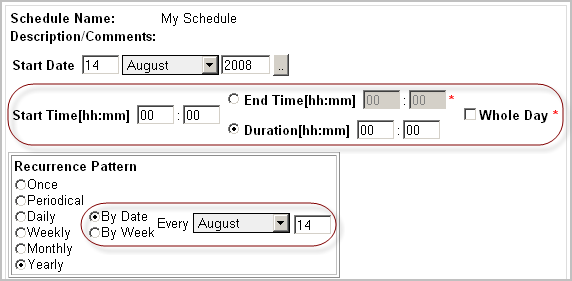
• |
To have the schedule occurring on one or more days of the week, at a rate of one or more months, in the Recurrence Pattern area, select the By Week option. |
|
5 |
Specify the date and time after which the schedule item ends using the controls in the Range of Occurrence area. |
|
• |
To specify an end date, in the Range of Occurrence area, ensure that End By Date is selected, and specify the end date and time using the End Date and End Time [hh:mm] boxes as required. |
|
• |
To have the schedule item recurring at the recurrence pattern specified in Step 4 without an end date, in the Range of Occurrence area, select No End. |
|
• |
New schedules. In the lower-right corner, click Add. |
|
• |
Existing schedules. In the lower-right corner, click Save. |
|
1 |
| |||
NOTE: The Duration [hh:mm] boxes appear disabled when you specify the End Time [hh:mm] option.
 The end time should occur after the start time. | |||
| |||
| |||
|
• |
If you want the schedule to occur for the entire day, select the Whole Day check box. |
|
• |
To have the schedule occurring on a specified day of the month, at the rate of one or more months, in the Recurrence Pattern area, ensure that By Date is selected, and then specify the day of the month and the rate at which it occurs. |
|
• |
To have the schedule occurring on a particular day of the week, in the Recurrence Pattern area, select the By Week option. |
|
5 |
Specify the date and time after which the schedule item ends using the controls in the Range of Occurrence area. |
|
• |
To specify an end date, in the Range of Occurrence area, ensure that End By Date is selected, and specify the end date and time using the End Date and End Time [hh:mm] areas. |
|
• |
To have the schedule item recurring at the recurrence pattern specified in Step 4 without an end date, in the Range of Occurrence area, select the No End option. |
|
• |
New schedules. In the lower-right corner, click Add. |
|
• |
Existing schedules. In the lower-right corner, click Save. |
Manage Retention Policies
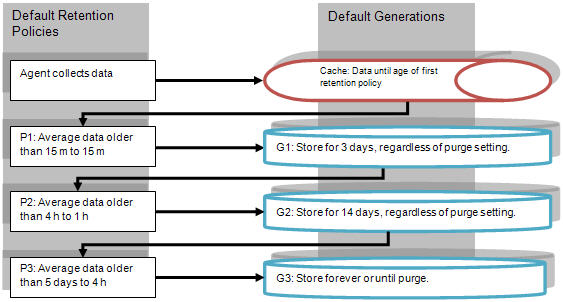
While it is theoretically possible to create any retention policy that you desire in Foglight 5, the design of the system constrains the easy-to-accomplish retention policies to a narrow range of options. Specifically, the database design of Foglight provides a structure that is capable of holding data in three different buckets, called generations, that are defined in <Foglight_home>/config/storage-config.xml. Each generation has a predefined period of time in which it retains data.
Without modifying database generations, there are specific rules that you must follow when assigning retention policies, to ensure that you achieve the expected results. Any changes to the database generations in <Foglight_home>/config/storage-config.xml require a Management Server restart, in order for these changes to take effect.
|
• |
Generation 1: Holds data for 0 – 3 days |
|
• |
Generation 2: Holds data for 3 – 14 days |
|
• |
Generation 3: Holds data for indefinitely |
The data service periodically writes data from the short-term memory cache to Generation 1. The frequency in which data is written is defined in the first retention policy (for more information, see How retention policies interact with database generations). This interval should not exceed 15 minutes to prevent the Foglight Management Server memory from growing too large.
A nightly roll-up job aggregates data and writes that data to Generation 2 and Generation 3. The roll-up is only done once a day, according to the time set in the Daily Database Maintenance schedule. For more information about this and other schedules in Foglight, see Associate Metric Calculations with Schedules.
|
• |
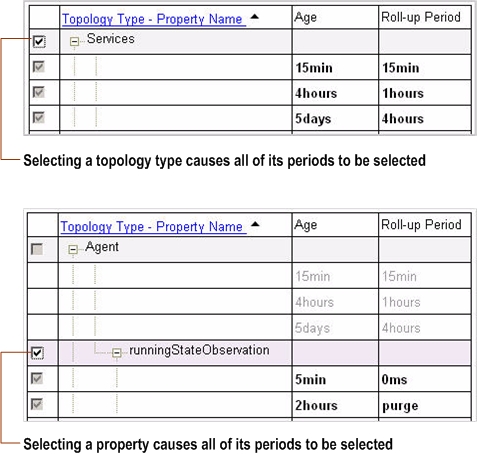
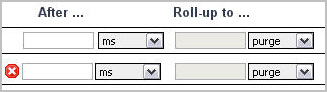
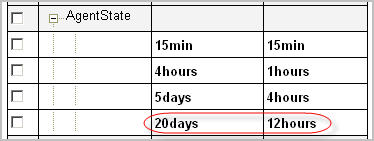
Age: Specifies the age at which the data is eligible for a roll-up |
|
• |
Roll-up period: Specifies the period of time over which the data is aggregated |
The policy that is applied to TopologyObject, and therefore any object which does not have explicitly assigned policies, is as follows:
As indicated in the above diagram, any data whose retention policies include the purge settings is stored in the Generation 3 aggregation, from which it is purged in accordance with the purge settings. Purging from the last generation is done by recreating the tables to filter out the observations that are to be purged, and it occurs once a month for each configured purge setting. For example, if there are n policies that request a purge after 12 months and m policies that request a purge after 18 months, then at the start of the month, Foglight performs a single purge on the 12-month tables and a single purge on the 18-month tables. If your business requirements dictate that any data older than x months should be purged from the database, the most efficient implementation is to edit the Generation 3 setting in <Foglight_home>/config/storage-config.xml, whose default length is set to one hundred years, to x months. For example, the following code block illustrate a Generation 3 setting in storage-config.xml that dictates the purge of any data that is older than six months:
|
Data is persisted at the roll-up interval defined in the Level 1 policy for three days. | |||
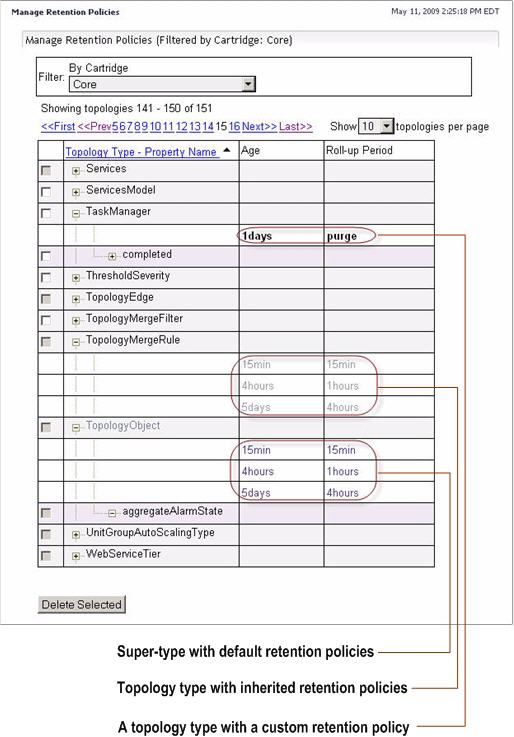
Use the Manage Retention Policies dashboard to view, edit, and create retention policies for topology types and properties of topology types. Each policy specifies one or more time periods after which the data is rolled up and the granularity of the roll-up.
In some cases your retention policies may cause an unacceptable increase in the database size, which typically happens if the granularity is high and the data is not frequently purged. Alternatively, the database size can be controlled by deleting specific topology objects and any metrics that they contain. This can be done through the Retention Policies dashboard. In addition to associating the default monitoring policies with data storage cycles, this dashboard allows you to inspect the topology objects and to delete them by applying specific retention policies to the collected data, or to purge specific data objects as required. For more information about this dashboard, see Monitor Server Performance.
If a topology type references the default data storage cycle, its retention policies cannot be modified or deleted. The default data storage cycle can be modified using the Retention Policies dashboard. For more information about this dashboard, see the Foglight User Guide. Any types descending from that type that inherit its retention policies can have their retention policies modified or deleted. This also applies to the descendants that have custom retention policies.
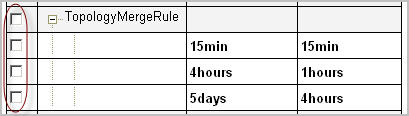
This prevents any accidental modifications of default observation life cycles through the Manage Retention Policies dashboard. For example, the retention policies of the TopologyObject super-type reference the default cycle, and as such, cannot be modified. The TopologyMergeRule type is a descendent of TopologyObject which inherits the retention policies of the ancestor type; those policies can be modified or deleted using the Manage Retention Policies dashboard. Modifying the TopologyMergeRule‘s retention policy, inherited from TopologyObject, creates a custom policy. The TaskManager type, also a descendant of TopologyObject, has a custom retention policy; this policy can be modified or deleted as required. The Manage Retention Policies dashboard indicates whether a type directly references the default storage cycle, inherits policies from another type, or has its own custom policies.
|
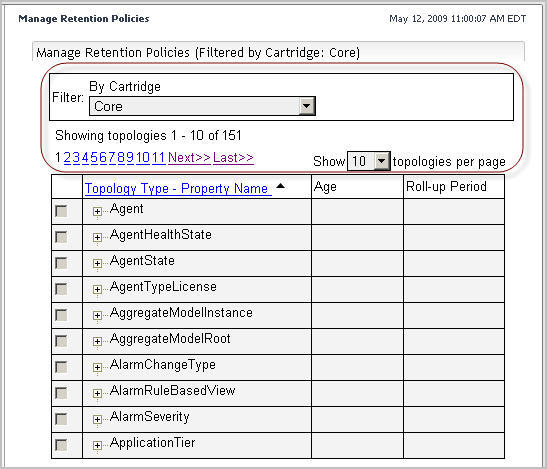
2 |
On the navigation panel, under Dashboards, choose Administration > Data > Manage Retention Policies. |
|
3 |
To sort the list of retention policies by the topology type to which they apply, click the Topology Type—Property Name column heading as required. |
If a topology type directly references the default data storage cycle, such as the TopologyObject super-type, its retention policies cannot be deleted. The default data storage cycle can be modified using the Retention Policies dashboard. In addition to associating the default monitoring policies with data storage cycles, this dashboard allows you to inspect the topology objects and to delete them by applying specific retention policies to the collected data, or to purge specific data objects as required. For more information about this dashboard, see the Foglight User Guide.
Any types descending from TopologyObject that inherited its retention policies can have their retention policies deleted. This also applies to the descendants that have custom retention policies.
For example, the retention policies of the TopologyObject super-type reference the default cycle, and as such, cannot be modified. The retention policy of any TopologyObject descendents that inherit its default policy can be deleted after its conversion to a custom policy. Any custom policies are enabled for deletion by default.
|
1 |
On the navigation panel, under Dashboards, choose Administration > Data > Manage Retention Policies. |
|
2 |
Topology types with inherited retention policies only. Convert the inherited retention policy to a custom policy. |
|
a |
On the Manage Retention Policies dashboard, in the Topology Type—Property Name column, click the row containing the topology type that has inherited policies. |
|
b |
|
4 |
Click the Delete Selected button at the bottom. |
|
5 |
|
6 |
The Retention Policy Confirmation dialog box closes and the Manage Retention Policies dashboard refreshes, no longer showing the newly-deleted sampling periods. |
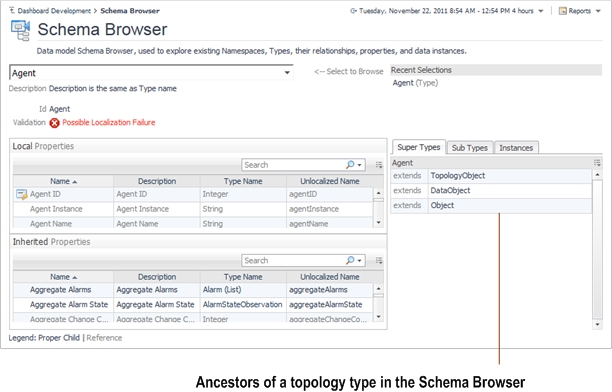
For more information about the Schema Browser, see the Foglight User Guide.
The Manage Retention Policies dashboard allows you to edit existing retention policy periods. If a topology type directly references the default data storage cycle, such as the TopologyObject super-type, its retention policies cannot be modified. The default data storage cycle can be adjusted using the Retention Policies dashboard. In addition to associating the default monitoring policies with data storage cycles, this dashboard allows you to inspect the topology objects and to delete them by applying specific retention policies to the collected data, or to purge specific data objects as required. For more information about this dashboard, see the Foglight User Guide.
Any types descending from TopologyObject that inherited its retention policies can have their retention policies modified. This also applies to the descendants that have custom retention policies.
For example, the retention policies of the TopologyObject super-type reference the default cycle, and as such, cannot be modified. The retention policy of any TopologyObject descendents that inherit its default policy can be modified after its conversion to a custom policy. Any custom policies are enabled for edits by default.
|
1 |
On the navigation panel, under Dashboards, choose Administration > Data > Manage Retention Policies. |
|
2 |
Topology types with inherited retention policies only. Convert the set of inherited retention policy to custom policies. |
|
a |
On the Manage Retention Policies dashboard, in the Topology Type—Property Name column, click the row containing the topology type that has inherited policies. |
|
b |
|
9 |
Click Save. |
The super-type, TopologyObject, has a set of default retention policies that directly reference the default data storage cycle. You cannot create additional policies for this type. The default data storage cycle can be adjusted using the Retention Policies dashboard. In addition to associating default monitoring policies with data storage cycles, this dashboard allows you to inspect the topology objects and delete them by applying specific retention policies to the collected data, or to purge specific data objects as required. For more information about this dashboard, see the Foglight User Guide.
Any types descending from TopologyObject that inherited its retention policies can have their retention policies modified. This also applies to the descendants that have custom retention policies.
For example, the retention policies of the TopologyObject super-type reference the default cycle. You cannot add new retention policies to that topology type. The retention policy of any TopologyObject descendents that inherit its default policy can be modified to include additional policies. However, adding a new policy to a set of inherited default policies converts all of the type’s policies to custom.
|
1 |
On the navigation panel, under Dashboards, choose Administration > Data > Manage Retention Policies. |
|
2 |
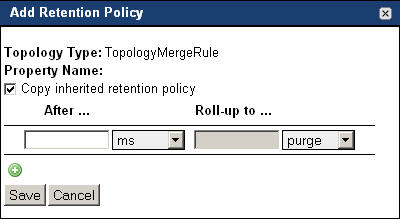
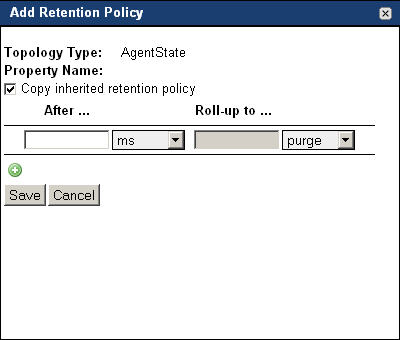
On the Manage Retention Policies dashboard, click the topology type to which you want to add a new retention policy. |
|
3 |
Topology types with one or more inherited retention policies only. Ensure that the retention policy that you are about to create does not overwrite any inherited policies |
|
NOTE: This check box appears in the Add Retention Policy dialog box only if the selected type includes any inherited retention policies. |
|
7 |
Click Save. |
This section contains information on how to monitor, estimate, and manage the size of your database.
Foglight server comes with a rule, Catalyst Database Space Checking, which monitors the size of the database and triggers alarms at different severity levels. The following registry variables define the thresholds used by the rule:
|
• |
DBSMon.MaxDatabaseSize (the intended maximum size of the database, in bytes) |
For more information about the Catalyst Database Space Checking rule, see Catalyst Database Space Checking rule.
The following observation types are persisted in the obs_string_* tables:
Complex observations are persisted in the obs_binary_* tables.
You can check the typical record size of a table by looking at the database serviceability metrics in the browser interface. Select the Configuration > Data node in the navigation panel, and in the display area, expand the Foglight > All Data > FSMDatabases > <foglight_management_server_machine> > Tables node. You will see a list of sub-nodes that represent the tables used by Foglight.
Select and expand one of the obs_binary_* nodes and you will find several metric nodes. You can calculate the typical record size using the following formula:
(dataLength + indexLength) / numberRows
MySQL with innodb engine does not shrink the table space file, even after you truncate the tables.
|
3 |
Use mysqldump to dump all of your InnoDB tables: |
|
NOTE: Substitute dbport, dbuser, dbpwd, and dbname with the correct port number, user name, password, and database name. |
|
NOTE: Substitute dbport, dbuser, and dbpwd the correct port number, user name, password, and database name. |
If you are using an external database, you may experience a situation where the database password for the Foglight database account has changed (for example, when password policies change). Use the following method to reconfigure Foglight to start up with the new database password. The password can be encrypted using the keyman command, and then updated in the external database and in the server.config file.
If the administrative password for the embedded database changes, use the same procedure, and update the server.database.embedded.password parameter in the server.config file.
|
2 |
In the Command Prompt or the terminal window, navigate to the Foglight Management Server installation directory. |
|
4 |
Change the database password in Foglight, in the server.config file. |
|
a |
Open the config/server.config file for editing. |
|
c |
Save the changes to the server.config file and restart the Foglight Management Server. |
For more information about the keyman command, see the Command-Line Reference Guide.
Add Topology Types
Use the XML syntax when defining a topology type. For example:
|
1 |
|
2 |
To add one or more topology types that are defined in an XML file accessible by your local machine, complete one of the following steps in the Import From File area of the Add Topology Type dashboard. |
|
• |
Ensure that the File on Local Computer option is selected. Then click Browse, and navigate to the topology file in the file browser that appears. |
|
• |
Select the File on Local Computer option, and in the box to the right, type the absolute path and name of the topology file |
|
a |
Select the Location on Server. |
|
b |
In the File Location on Server box, type the path and name of the topology file. Use either an absolute path or a path relative to the installation directory of the Foglight Management Server. |
|
4 |
To define one or more topology types using the text editor in the Add Topology Type dashboard, in the Import From Text area, type the topology definition that you want to add between the <types> and </types> tags. |
|
5 |
Close Click Import Topology. |