Manage Lockboxes
This dashboard is a starting point when creating credentials. Credentials are stored in lockboxes. Ensure that you have the appropriate lockboxes in place before creating credentials. The dashboard displays a list of all lockboxes that are defined on the server, in addition to the System lockbox that is included with the Management Server. This lockbox is not password-protected. Its contents are accessible to all clients in your system. The System lockbox is only intended for use with some agent types, and it is always available for selection in the flow for adding credentials initiated from the Manage Credentials dashboard. For that reason, any purpose-specific wizards included with cartridges whose agents do not support the System lockbox do not provide this lockbox as an option when creating credentials.
|
• |
Default: This lockbox is password-protected. The default password is foglight. Consider changing this password after the installation to protect its contents. |
By default, the following columns are displayed:
|
• |
|
• |
Alarms: The total counts of outstanding credential alarms, broken down by alarm types (Fatal, Critical, and Warning). |
|
• |
Name: The lockbox name. |
|
• |
Credential Count: The number of credentials contained in the lockbox. |
|
• |
Credential Clients: Lists the clients to which this lockbox is released. This column is populated only if the check box Show lockboxes currently assigned to each client is selected on the View Clients dashboard. For more information, see Explore the View Clients dashboard. |
|
• |
|
• |
Change Password: Click to change the lockbox’s password. For more information, see Change the password for a lockbox. |
|
• |
Release to Credential Clients: Click to release the lockbox. For more information, see Release lockboxes to credential clients. |
Use the Add button to add a lockbox to the existing collection.
For more information, see Add or delete lockboxes.
|
2 |
In the New Lockbox dialog box, in the Name box, type a unique name for the lockbox. For example, My Production Server Access. |
|
a |
Select the Secure using a password check box. |
|
b |
|
4 |
Click Add. |
|
2 |
Click Delete. |
|
3 |
|
2 |
In the Add Password To Lockbox dialog box, type the new password in the New Password and Confirm New Password boxes. |
|
3 |
Click Confirm. |
|
2 |
In the Remove Password of Lockbox dialog box, type the existing lockbox password in the Lockbox Password box. |
|
3 |
Click Confirm. |
|
2 |
In the Change Password of Lockbox dialog box, type the current password in the Old Password box, and the new password in the New Password and Confirm New Password boxes. |
|
3 |
Click Confirm. |
|
2 |
If the lockbox is password-protected, in the Release Lockbox to Credential Clients dialog box, type the lockbox password and select one or more credential clients for lockbox release. |
|
3 |
Click Release. |
|
4 |
Optional — Ensure the Credential Clients column is populated. |
|
b |
On the View Clients dashboard, ensure that the Show lockboxes currently assigned to each client check box is selected. |
|
f |
On the Manage Lockboxes dashboard, observe the Credential Clients column of the newly released lockbox entry. The column lists the credential clients to which the lockbox is assigned. |
Manage Credentials
By default, the following columns are displayed:
|
• |
|
• |
Edit: Click to edit a credential’s name, properties, resource mappings, or policies. |
|
• |
Lockbox: The name of the lockbox where the credential is defined. |
|
• |
Name: The name of the credential. |
|
• |
Alarms: The total counts of outstanding credential alarms, broken down by alarm types (Fatal, Critical, and Warning). |
|
• |
Valid Until: The date and time at which the credential expires. |
|
• |
Relative Order: The order in which credentials are returned to credential clients. |
|
• |
Type: Shows the credential type. The following credential types are available: |
|
• |
Challenge Response: Uses one or more challenge and response pairs to grant access without requiring any interaction in the browser interface. The answers are sent by the agent and are part of the agent configuration. Use this type for SSH keyboard-interactive credentials. |
|
• |
Domain, User Name, and Password (Windows): Requires a user name and password to access a monitored resource. The domain name is optional. |
|
• |
DSA Key: Uses the Digital Signature Algorithm (DSA) Key for authentication. |
|
• |
RSA Key: Uses the RSA (Rivest, Shamir and Adleman) Key for authentication. |
|
• |
Use Client’s Login At Connection Time: Uses the currently logged in user’s account to access secured resources. This is not the user currently logged into the Management Server, but the user under which the credential client is running. For example, a credential provided to a Foglight Agent Manager instance launched by a user on a remote machine, causes the connection to the secured resource to be made using this user’s identity. |
|
• |
User Name: Requires a user name to access a monitored resource. |
|
• |
User Name and Password: Requires a user name and password to access a monitored resource. |
|
• |
Resource Mappings: Lists one or more resource mapping expressions associated with the credential. |
|
• |
Policies: Lists the policies associated with the credential. Hovering over this column displays a dwell that shows you this information in tabular form. |
|
• |
|
• |
|
• |
Credentials that are no longer in use can be deleted.
|
• |
Challenge Response: Uses one or more challenge and response pairs to grant access without requiring any interaction in the browser interface. The answers are sent by the agent and are part of the agent configuration. |
|
• |
Domain, User Name, and Password (Windows): Requires a user name and password to access a monitored resource. The domain name is optional. |
|
• |
DSA Key: Uses the Digital Signature Algorithm (DSA) Key for authentication. |
|
• |
RSA Key: Uses the RSA (Rivest, Shamir and Adleman) Key for authentication. |
|
• |
Use Client’s Login At Connection Time: Uses the currently logged in user’s account to access secured resources. This is not the user currently logged into the Management Server, but the user under which the credential client is running. For example, a credential provided to a Foglight Agent Manager instance launched by a user on a remote machine, causes the connection to the secured resource to be made using this user’s identity. |
|
• |
User Name: Requires a user name to access a monitored resource. |
|
• |
User Name and Password: Requires a user name and password to access a monitored resource. |
|
3 |
Click Next. |
|
4 |
Editing credential properties. On the Credential Properties page, specify the authentication properties based on the credential type selected in Step 2, and click Next. |
|
a |
On the Credential Name And Lockbox page, provide a unique name for the credential that you are about to create. |
|
b |
Select the lockbox where you want to store the credential from the Select A Lockbox list. Choose from the existing lockboxes (like the System lockbox), or create a new one, if required. |
|
NOTE: The System lockbox is only intended for use with some agent types, and it is always available for selection in the flow for adding credentials initiated from the Manage Credentials dashboard. For that reason, any purpose-specific wizards included with cartridges whose agents do not support the System lockbox do not provide this lockbox as an option when creating credentials. |
|
c |
Click Next. |
|
6 |
Indicate if you want un-encrypted credential data to be accessible by clients using the Unencrypted Credential Data Accessible to Clients check box. |
|
7 |
Mapping monitored resources. On the Resource Mapping page, specify the resources that you want to monitor with the agent that will use this credential. |
|
a |
To add a resource mapping, click Add and specify the resource mapping using the New Resource Mapping Condition dialog box that appears. |
|
c |
|
8 |
Editing policies. On the Policies page, add one or more authentication policies to the credential. |
|
a |
To add a policy, click Add and select a policy type from the menu that appears. |
|
c |
|
2 |
Click Copy From An Existing Credential. |
|
4 |
|
• |
To choose from existing lockboxes, click the Lockbox box and select a lockbox from the list that appears. |
|
• |
To create a new lockbox, click Add a New Lockbox, and in the New Lockbox dialog box that appears, type the name and password, then click Add. |
|
6 |
Indicate if you want un-encrypted credential data to be accessible by clients by using the Unencrypted Credential Data Accessible to Clients check box. |
|
7 |
At the bottom of this dialog box, specify the authentication data based on the credential type selected in the original credential. For example, if you selected User Name and Password as the credential type, type the user name and password required to associate with this credential using the User Name, Password, and Confirm Password boxes. |
|
8 |
Click Next to specify the credential policies and resource mappings, or click Finish to exit the flow. Add additional information including credentials policies and resource mapping at a later time, if required. |
|
2 |
Click Delete. |
|
3 |
|
2 |
Click Credential Properties in the menu. |
|
3 |
In the Update Credential Properties dialog box, edit the credential properties, as required. |
|
4 |
Click Save. |
Credential names are specified during creation. They can be changed at a later time, if required.
|
2 |
Click Credential Name in the menu. |
|
3 |
|
4 |
Click Save. |
|
2 |
Click Policies in the menu. |
|
a |
|
• |
Use Count: The maximum number of times the credential can be used, successfully or unsuccessfully, by a selected client. |
|
• |
Failure Rate: The maximum number of authentication failures allowed over a specific time period. |
|
• |
Validity Window: The time period during which the credential can or cannot be used. |
|
• |
Cache Time: The time period during which the credential data is cached on the credential client, without requesting it from the Management Server. |
|
c |
Provide additional information required by the selected policy type. For example, if you selected Use Count in Step b, you need to provide the maximum number of times the credential can be used. |
|
d |
Click Add. |
|
4 |
Copying policies from an existing credential. You can copy credential policies from any credential type. |
|
a |
|
2 |
Click Policies in the menu. |
|
3 |
|
2 |
Click Policies in the menu. |
|
3 |
In the Update Policies of Credential dialog box, in the row containing the policy that you want to edit, click |
|
b |
Click Save. |
The type and structure of resource mappings depend on the selected credential type, which in turn depends on the range of installed cartridges. Some cartridges, for example, support the Use Client’s Login At Connection Time and User Name and Password credential types, while others can only accept the Challenge Response or User Name types. A Domain, User Name, and Password (Windows) credential type, for example, that requires a valid domain name, user name, and password to access a monitored system, can have one or more resource mappings for accessing Windows-based systems based on a condition that evaluates the target host name.
|
• |
Usage: Defines the type of the system that is mapped. For example: OS Monitoring by WMI. |
|
• |
Access Resources Using: Identifies the resource component that is evaluated by the resource mapping. For example: Target Host Name, Target Host Address, Target Port, or Is Local Host. Other options may be available. |
|
• |
Equal or Not Equal: Indicates if the targets selected by the matching expression should be included or excluded from the mapping. For example, you can create one resource mapping to select a group of hosts and another to exclude a different set of hosts. |
|
• |
Matching Type: Specifies the condition type. For example, conditions can contain regular expressions or domain names. |
|
TIP: Regular expressions support case insensitive matching when the (?i) flag is used. For example, (?i)host1.example.* returns Host1.example and host1.example.com as matches. Regular expressions run through the JRE Pattern class that supports case insensitivity. For syntax information and usage tips, visit http://rd-www.prod.quest.corp/static/sun_docs/jdk-1_6_0/docs/api/java/util/regex/Pattern.html. |
|
• |
Evaluate This Condition: Indicates if the condition is used during the credential matching. |
|
• |
Matching Values: One or more expressions that are used to scope on the target resource. For example, you can create an expression that defines a host name. Multiple matched values are combined with the logical OR operator, meaning that if one expression evaluates to True, the resource is mapped even though another expression may evaluate to False. |
The selections available with each building block in a resource mapping depend on the resource mapping’s Usage type, which in turn depends on the selected credential type and the range of installed cartridges. The selections mentioned above do not reflect the values available with all of the cartridges that support credentials. For information about the available credential types supported by a specific cartridge and the related resource mappings and their building blocks, refer to the cartridge documentation.
|
2 |
Click Resource Mappings in the menu. |
|
a |
|
• |
equals: Select this option to select the resources the credential can access. |
|
• |
does not equal: Use this option to select the resources the credential cannot access. |
|
f |
Select or clear Evaluate This Condition. |
|
h |
Click Add. |
|
a |
|
2 |
Click Resource Mappings in the menu. |
|
3 |
To add a condition to an existing resource mapping, in the row containing the resource mapping, click |
|
4 |
To edit an existing resource mapping condition, in the row containing the resource mapping, click |
|
2 |
Click Resource Mappings in the menu. |
|
5 |
The Confirm Deleting Resource Mapping dialog box closes and the Update Resource Mapping of Credential dialog box refreshes, no longer showing the newly deleted entry. |
|
1 |
|
• |
To move one credential up or down, use the |
|
• |
To move multiple credentials, select the rows containing the credentials that you want to move, and use the |
|
3 |
|
1 |
On the Manage Credentials dashboard, click Query Credential. |
|
2 |
In the Query Credential dialog box, specify the criteria as required. |
|
3 |
Click Execute. |
Monitor Alarms
Credential clients generate alarms when certain pre-defined conditions are met. These errors typically happen when a client attempts to access a resource and encounters a policy-related problem. The Monitor Credential Alarms dashboard lists all alarms generated by the existing credential clients and provides additional information about each event. The list includes any alarms generated by the Catalyst Credential Check rule and Credential events generated by the Foglight Agent Manager.
For complete information about alarms in Foglight, see the Foglight User Help.
By default, the Monitor Credential Alarms dashboard displays the following columns:
|
• |
|
• |
Time: The date and time at which the alarm is generated. |
|
• |
|
TIP: Use the Select All or Unselect All buttons to quickly select all alarms, or to clear your selection, as required: |
|
• |
|
• |
Instance: The topology object instance against which the alarm is raised. |
|
• |
Message: The alarm message. |
|
• |
Origin: The event that caused the alarm to fire. |
To filter the list of alarms, click Alarm Filter in the top right and provide the desired settings.
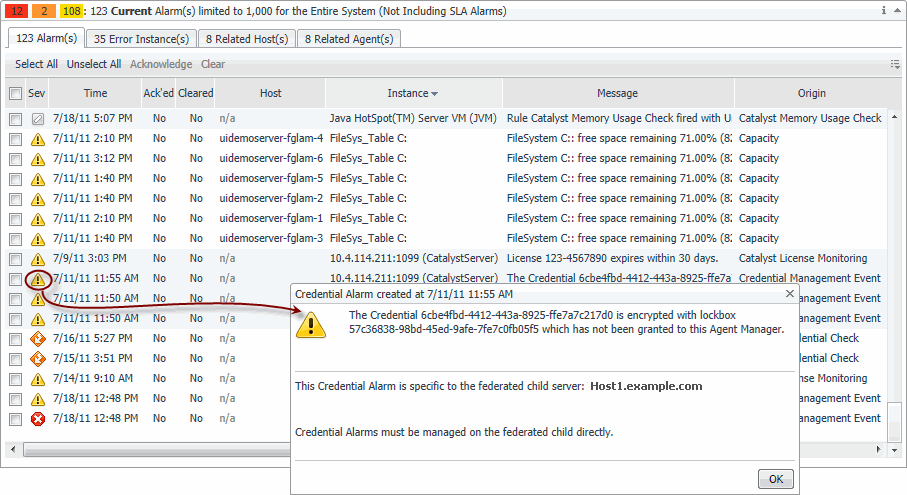
To view the Credential Alarm dialog box, click any column.
Use this dialog box to find out more about the problem that caused the alarm. From here, click the Diagnostic link to access the part of the browser interface that you can use to further investigate the problem.
The Credential Alarm dialog box that appears shows a smaller subset of information, containing only the alarm message and the name of the Federated Child server. To retrieve complete information about this alarm, log in to the Federated Child server, navigate to the Monitor Credential Alarms dashboard, and drill down on the alarm to display the common version of the Credential Alarm dialog box.
For complete information about alarms in Foglight, see the Foglight User Help.
|
Attempt is made to authenticate a connection through the CleartextCredentialService with a credential that is not granted direct access rights. |
|||
|
A lockbox that is associated with a credential is not granted to the Agent Manager Host. |
|||
|
The credential used to establish a connection fails to authenticate access to the remote resource. |
|||
|
A connection to the remote host cannot be established using the retrieved credential. |
|||
|
2 |
Click Acknowledge. |
|
2 |
Click Clear. |
View Clients
By default, the following columns are displayed:
|
• |
Alarms: The numbers of Fatal, Critical, and Warning alarms generated against each client, color-coded to indicate the severity. |
|
• |
Name: The name of the credential client. |
|
• |
Client Type: The credential client type. For example, FglAM (Foglight Agent Manager). |
|
• |
Assigned Lockboxes: The name of the lockbox released to the credential client. |
|
• |
Host: The name of the monitored host on which the client is running. |
Selecting the check box Show lockboxes currently assigned to each client causes the Credential Client column on the Manage Lockboxes dashboard to be populated. For more information about the Manage Lockboxes dashboard, see Explore the Manage Lockboxes dashboard .