Security overview
This Security and Compliance Guide describes the Foglight® security features. This document includes information about Foglight access control, data protection, and secure network communication. It also describes how Foglight security features meet the National Institute of Standards and Technology (NIST) recommended federal information security standards as detailed in the Federal Information Security Management Act (FISMA).
This section provides an overview of how Foglight manages information security.
It presents the Foglight security measures and Customer security measures at a high level, and then describes the Security features in Foglight.
Foglight security measures
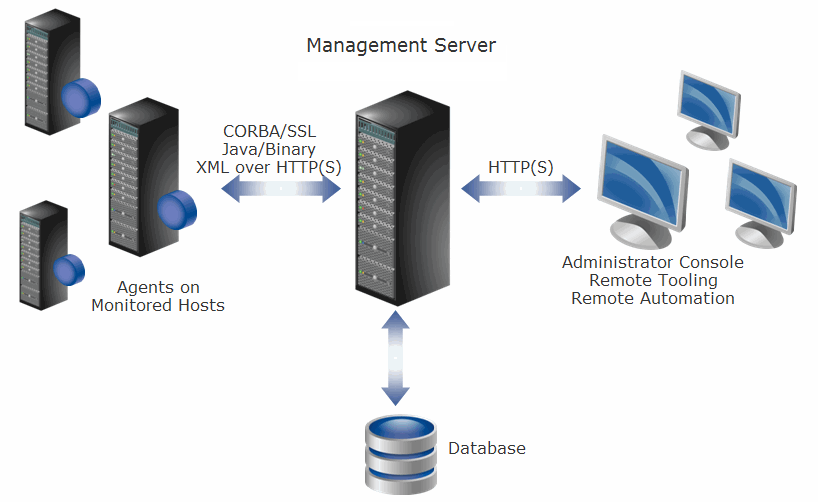
Foglight® provides detailed insight into the service relationships of end users, business and IT services, as well as applications and databases. Intuitive and flexible dashboards can be customized to provide multiple models and views of the managed environment.
Foglight consists of the Foglight Management Server (FMS), a database repository, and a set of cartridges. Foglight relies on a browser-based user interface and is controlled via role assignments in the Foglight security model. The Foglight Web application runs in an Apache Tomcat® server. Users interact with the FMS Web application via an HTTP or HTTPS connection.
Customer security measures
Foglight® security features are only one part of a secure environment. The customer's operational and policy decisions have a great influence on the overall level of security. In particular, the customer is responsible for the physical security of Foglight and its network. Administrators should change default passwords and replace them with strong passwords of their choice.
Security features in Foglight
The following sections describe the features provided by Foglight®. This document does not address security features for individual Foglight cartridges. Please refer to a specific cartridge's security and compliance document for this information.
|
NOTE: If your environment includes APM appliances, review Trust model after you finish this section. |