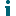When you select Profiles from the hamburger menu in On Demand Migration for Active Directory, you will see a new section for creating Interactive Client profiles.
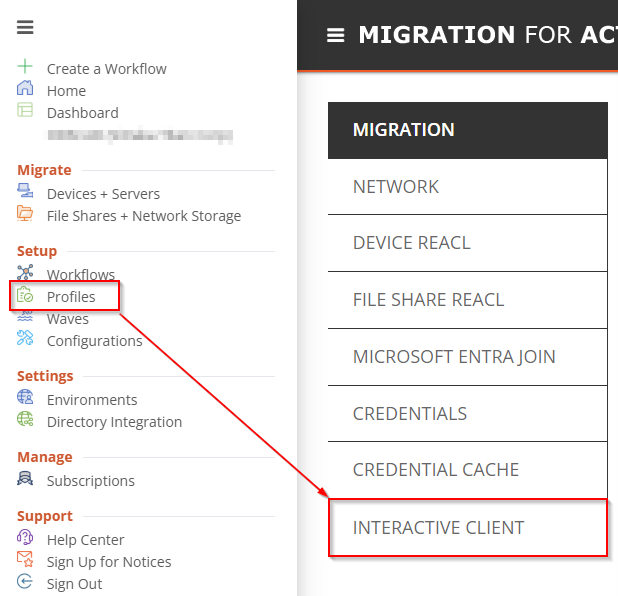
Create a new profile and configure the options for allowing end users to postpone and cancel the device cutover. Enable the option to allow unattended cutover if you want the device cutover to proceed even if the user is not logged on or if they do not respond to the interactive client when it appears. You can create multiple profiles with different options.
What are Actions and Tasks?
Actions are a sequence of Tasks to complete a process.
The Actions screen will allow you to create a new Custom Actions that can be performed against Accounts, Computers or File Shares. Existing or new tasks can be added to a the desired Custom Action and then ordered as necessary to complete the custom process.
It is important to note that System actions and tasks can only be viewed or copied, they are not editable.
How is an Action created or copied?
To add or copy an action: Below the table, click New or select an existing Custom Action and click Copy. Check Show System to view and select any existing Systemactions.
- Action Name (Required): Enter a name for the Custom Action. The Action Name must be unique.
- Action Display Name: Enter the name that appears in the Actions menu.
- Description: Enter a description for the action.
- Action Target: Select one of the options from the drop-down list.
- Computer: The Action will appear in the Actions menu on the Computers screen.
- File Share: The Action will appear in the Actions menu on the File share screen.
- Action Type: Select one of the options from the drop-down list. The Action Type determines what validations are applicable to the job, and which status columns are updated when the job runs. For example, a Custom Action with the ReACL type, will have the same validations as the System ReACL action.
- Other (default): An action not related to any System action. No predefined validations are applicable. By default, new Actions are assigned as type Other.
- Discovery: Gathers properties from the computer.
- Cutover: Moves a computer from the source domain to the new target domain.
- ReACL: Updates computer domain user profiles for use by the matching target user after cutover.
- ReACL Share: Updates the File Share’s domain user profiles for use by the matching target user after cutover.
- ReACL Rollback: Rolls back all changes made by the ReACLShare process.
- ReACL Rollback Share: Rolls back all changes made by the ReACL process.
- Cleanup: Removes the Source SIDs after the Cutover process completes.
- Cleanup Share: Removes the Source SIDs after the Cutover process completes.
- Explicit Rollback: Rejoins a computer back to the source domain.
- Upload Logs: Uploads log files from the Active Directory Pro Agent to the Active Directory Pro Server using Microsoft BITS.
How is a Task created or copied?
To add or copy a task: Below the Tasks table, click New or select an existing task and click Copy. Check Show System to view and select an existing Systemtask.
- Task Name (Required): Enter a name for the task. The Task Name cannot begin with "BT-" which is used to identify system tasks.
- Description: Enter a description for the menu action.
- Task Type (Required): Select one of the options from the drop-down list.
- PowerShell Script: Allows you to define a PowerShell script for the process on the Command and Rollback screens. Global Variables can be added and used in the script.
- Command Line: Allows you to define a Command Line command for the process on the Command and Rollback screen. Global Variables can be added and used in the command line.
- Download File: Downloads a file to the predefined Downloads folder.
- Automatic Rollback:
- Auto-Rollback On Error: if checked, automatic rollback on error is added to the task.
- Include Variables For:
- Manage Credentials: if checked, the PowerShell script or Command Line command includes the $CutoverCredentials_XXXXX parameters.
- Network Profile Settings: if checked, the PowerShell script or Command Line command includes the $NetworkProfile_XXXXX parameters.
- Migration Profile Settings: if checked, the PowerShell script or Command Line command includes the $MigrationOption_XXXXX parameters.
- Global Variables: if checked, the PowerShell script or Command Line command includes the Global Variables.
- Script: Enter a PowerShell script or Command Line command. If creating a PowerShell script, click Load Script Framework to populate the entry box with the basic framework of a script. Enter or edit the Command Line command or PowerShell script. Text is required. The return value of the script or command will determine success or failure.
- Rollback: Enter a PowerShell script or Command Line command to run in case of failure/Rollback. Ideally this would undo the effects of the above script. If creating a PowerShell script, click Load Script Framework to populate the entry box with the basic framework of a script. Enter or edit the Command Line command or PowerShell script. Text is required. The return value of the script of command will determine success or failure.
- Task Timeout: For PowerShell script or Command Line command, enter the number of seconds the process will be attempted before timing out.
- Retry Count: For the PowerShell script or Command Line command, enter the number of times the process will be retried.
- Update Interval: For PowerShell script or Command Line command, enter the number of seconds between process runs.
- File Download: Enter the following options if adding or copying a Download File task. When a new download job is created for a managed workstation, the specified file that is stored in the configured Custom Downloads Repository will be downloaded to c:\Program Files (x86)\Binary Tree\P365ActiveDirectoryAgent\Downloads\ on the workstation’s local disk.
- File Name (required): The file name. Based on the File Location for Download Jobs used during installation The File Name cannot contain invalid filepath characters and cannot use the following reserved file names: map.usr, map.gg, and ReACL-config.json.
- File Path: The target Location of the download job. The Target Location cannot contain invalid filepath characters and cannot use the following reserved file names: map.usr, map.gg, ReACL-config.json. A Target Location is required if the File Name contains environment variables.
The local download folder on an Active Directory managed machine will be secured with permissions only for the BUILTIN\Administrators group.
|
|
NOTE: If rights other than BUILTIN\Administrators are required then the administrator will need to make a change on the local downloads folder (c:\Program Files (x86)\Binary Tree\P365ActiveDirectoryAgent\Downloads\) on the Agent machine. |
How is a Task added to an Action?
To add a Task to an Action: Select a Task in the Tasks table, select an Action in the Select Action drop-down menu and click the Add To button.
Under a given Action the Tasks are listed in the order in which they will be executed. Drag and drop tasks to reorder them. Tasks can be viewed, copied, or removed by selecting the tasks and clicking the appropriate button.
How do you activate an Action?
Only Actions marked as Active will appear in the Actions menus. Select an Action in the table and click the Disable or Enable button to change the active status of the Action. Inactive actions can be displayed in the table by clicking the Show Disabled button. You may want to create a new action, enable it, and then disable the corresponding System action.
Additional Information
Custom Action Example
How are Mapping Files downloaded?
Use the Downloads page to generate the User Mapping File (Map.usr) and Group Mapping File (Map.gg). These files are automatically created during the ReACL process so the only time they need to be created manually is when re-permissioning SQL databases.
To create the mapping files:
- Click the Download button.
- Select the source and target environment and click Submit.
- Use the browser options to open or save the mappings.zip file containing the User Mapping File (Map.usr) and Group Mapping File (Map.gg). Each time the Create Mapping Files process is run, the Map.usr and Map.gg files are overwritten.
Note, Use the Downloads page to generate the Active Directory and Exchange Processing Wizard Mapping Files. Additional detail for Active Directory and Exchange Processing Wizard Mapping Files can be found at Migration Manager for AD 8.15 - Resource Processing Guide (quest.com)
To enable GCC/GCCH Device Migration, please contact Quest Support for additional configuration described in the following article: Update GCC/GCCH tenant object's RID value for ReACL. This configuration is required for successfully switching the user profile during cutover.
How are device agents downloaded?
To download a device agent:
- Select an available agent version from the drop-down menu.
- Click the Download button.
- Use the browser options to save the agent installer package.
What are the Device Agent Service URL and Auth key used for?
The Device Agent Service URL and Auth Key as defined on the Downloads section of the Configurations page are provided to the Device Agents at install and allow them to connect to the correct customer’s On Demand Migration Active Directory project. They are unique to the agents in a given client and all agents of the same client should use the same values. If installing the agent from the command line without UI the arguments for providing the Service URL and Auth Key are their names in all uppercase i.e. SERVICEURL and AUTHKEY respectively.
How are device agents automatically upgraded?
To automatically upgrade the device agents:
- Click the Enable button at the bottom of the Device Agent section.